In the digital age, where mobile applications have become the backbone of daily activities such as banking, communication, social networking, and entertainment, the escalation of cyberattacks on these platforms is a pressing concern. These applications, which handle a plethora of sensitive user data, have emerged as prime targets for cybercriminals. As the complexity of mobile applications skyrockets, so does the sophistication of the attacks aimed at exploiting their vulnerabilities.
The rise in static and dynamic attacks on mobile applications is not just a technical dilemma; it’s a burgeoning threat to businesses and organizations worldwide. The consequences of these attacks are far-reaching, extending from financial losses and reputational damage to severe breaches of user data and privacy. Understanding the intricacies of static and dynamic attack vectors, and implementing robust mitigation strategies, is paramount in this digital era.
This comprehensive guide delves into the nuanced world of static and dynamic mobile application attacks, shedding light on the intricate battle between cybersecurity measures and evolving cyber threats.
Further, we aim to equip readers with the knowledge to navigate the complex landscape of mobile application security, emphasizing the critical role of both SAST and DAST in defending against the sophisticated cyber threats of today.
What is Static Analysis?
Static Analysis, in the context of mobile application security, is a critical automated process used for scrutinizing the source code of mobile apps without executing them. Static Analysis is a proactive measure to ensure that the app is secure, efficient, and compliant with the necessary standards before it reaches the end-users. This is especially important given the sensitive nature of data handled by mobile apps and the diverse range of threats targeting mobile platforms.
How does it work?
The core functionality of Static Analysis tools revolves around this process of scanning code, identifying problematic patterns, and providing relevant feedback to help developers address potential issues before the software is deployed or executed. This proactive approach is crucial for enhancing the quality, security, and performance of software applications.
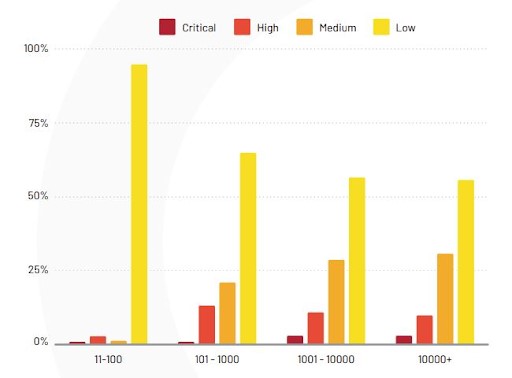
The breakdown of the severity of security vulnerabilities according to company size.
Image Source
Static analysis can be used to identify a wide range of vulnerabilities, including:
Coding errors:
These are errors in the code that can be exploited by attackers to gain unauthorized access to data or systems.
In Android applications, a common coding error related to security is improper handling of sensitive data, such as storing it unencrypted in shared preferences or on external storage. Here’s a simplistic example:
SharedPreferences prefs = getSharedPreferences(“UserDetails”, MODE_PRIVATE);
SharedPreferences.Editor editor = prefs.edit();
editor.putString(“username”, username);
editor.putString(“password”, password);
editor.apply();
In this example, the application is storing user credentials (username and password) in shared preferences without any form of encryption. Shared preferences in Android are key-value pairs used to store data, but they are not secure for sensitive information, especially if MODE_PRIVATE is not used or if the device is rooted.
How the vulnerability can be exploited:
- If the device is compromised or rooted, attackers can easily access shared preferences and retrieve sensitive information like usernames and passwords.
- Additionally, if the application mistakenly uses a less secure storage mode (like MODE_WORLD_READABLE), other apps on the same device could access this data.
Logic flaws:
These are flaws in the logic of the application that can be exploited by attackers to cause unexpected behavior.
Here’s an example of a logic flaw in an insecure access control in a Banking App
Imagine a banking app that allows users to view their account details and perform transactions. The app has different types of accounts (e.g., savings, checking) and different user roles (e.g., primary account holder, secondary user). The app’s logic is supposed to restrict secondary users from accessing certain features, like initiating large transactions.
However, due to a logic flaw, this restriction is not properly enforced:
public void makeTransaction(String accountType, User user, double amount) {
// Check if the user is a secondary user
if (user.isSecondaryUser()) {
// Check if the account is a savings account
if (accountType.equals(“savings”)) {
// Supposed to restrict large transactions for secondary users
if (amount > 1000) {
showError(“Transaction limit exceeded for secondary users.”);
return;
}
}
}
// Proceed with the transaction
processTransaction(accountType, user, amount);
}
The logic flaw here is that the restriction on large transactions for secondary users is only applied to savings accounts, not checking accounts.
An attacker or a malicious secondary user could exploit this flaw by initiating a large transaction from a checking account, bypassing the intended security check.
How It Can Be Exploited:
A secondary user, who should have limited privileges, could exploit this flaw to perform unauthorized large transactions from a checking account, leading to financial loss or other serious consequences.
Insecure configurations:
These are configurations in the application that can be exploited by attackers to gain unauthorized access or cause the application to malfunction.
Imagine an Android application that uses Firebase, a popular backend-as-a-service platform, for its database needs. Firebase is used to store user data, app settings, and other sensitive information.
The Firebase database rules are incorrectly set, allowing unrestricted read/write access. This is often a default setting for ease of development, but it should be properly configured before the app is deployed.
{
“rules”: {
“.read”: true,
“.write”: true
}
}
In this configuration, the “.read” and “.write” properties are set to true for all paths, meaning anyone with the Firebase database URL can read from and write to the database without any authentication.
This is a common misconfiguration, especially during the early stages of development, where developers might prioritize ease of access over security.
How It Can Be Exploited:
An attacker who discovers the Firebase URL can access all the data stored in the database. They can read sensitive user information or even write malicious data to the database. This could lead to data breaches, unauthorized data manipulation, and compromise of user privacy.
Advantages and Disadvantages
SAST
SAST and DAST are two common application security testing (AST) methods used to identify and fix security vulnerabilities in software applications. Both methods have their own advantages and disadvantages, and the best method for a particular application will depend on the specific needs of the organization.
SAST for mobile apps involves analyzing the source code of mobile applications to identify security vulnerabilities. This is done without executing the application, focusing on the code written for platforms like Android (Java, Kotlin) and iOS (Swift, Objective-C).
How SAST Works:
SAST tools scan the mobile app’s source code to detect issues such as insecure code practices, hard-coded credentials, and other potential security vulnerabilities.The analysis includes reviewing code for platform-specific security issues, like Android Intent Sniffing or iOS Keychain vulnerabilities.
These tools can also identify non-compliance with mobile development best practices, such as improper use of APIs or misconfigurations in app permissions.
When Is SAST Conducted:
SAST is typically integrated early in the mobile app development lifecycle, often during the coding phase. This allows developers to identify and fix security issues before the app is compiled and deployed.
Dynamic Application Security Testing (DAST) for Mobile Apps
DAST for mobile apps involves testing the app from an external perspective while it is running. This approach does not require access to the source code and focuses on identifying runtime vulnerabilities.
How DAST Works:
DAST tools interact with the mobile app as an end-user or an attacker would, typically through its user interface or exposed APIs. The testing includes checking for vulnerabilities that manifest during runtime, such as issues with data storage, insecure communication, and authentication flaws.
DAST can also identify misconfigurations and vulnerabilities in the app’s interaction with backend services, third-party libraries, and the mobile operating system.
When Is DAST Conducted:
DAST is usually conducted after the mobile app is in a testable state, either in a simulator/emulator environment or on actual devices. This stage is often during or after the integration and testing phases of development.
Key Considerations for Mobile Apps:
Platform-Specific Issues:
Both SAST and DAST for mobile apps need to consider platform-specific security issues and best practices, as vulnerabilities can differ significantly between Android and iOS.
Integration with CI/CD:
Integrating SAST and DAST into the Continuous Integration/Continuous Deployment (CI/CD) pipeline can automate security testing, making it a seamless part of the mobile app development process.
User Interface and User Experience:
DAST for mobile apps should also consider the user interface and user experience aspects, as these can impact how security vulnerabilities manifest and are exploited.
| Aspect | SAST for Mobile Apps | DAST for Mobile Apps |
| Nature of Testing | Internal, “white box” testing of source code | External, “black-box” testing of running app |
| Focus Areas | – Code-level vulnerabilities
– Secure coding practices – Platform-specific issues (e.g., Android, iOS) |
– Runtime vulnerabilities
– User interaction – Integration with external components (OS, network) |
| When Conducted | Early in the development lifecycle, during coding | Later stages, on testable versions of the app |
| Advantages | – Early detection of vulnerabilities
– Detailed code-level insights – Helps in compliance with coding standards |
– Identifies runtime and real-world vulnerabilities
– Tests app’s interaction with external components |
| Limitations | – Cannot detect runtime issues
– Limited in assessing real-world interaction scenarios |
– No insights into specific code issues
– Remediation can be complex as it’s conducted later in the cycle |
| Integration in Dev Cycle | Integrated into continuous integration for immediate feedback | Integrated into later stages of testing, closer to production environment |
| Platform Considerations | Must consider platform-specific security challenges and best practices | Needs to address real-world usage scenarios and platform-specific runtime issues |
What is Dynamic Analysis?
Dynamic code analysis, also known as dynamic application security testing (DAST), is a method of analyzing computer software in which the program is executed, and its behavior is monitored to identify potential vulnerabilities.
Dynamic code analysis can be used to identify a wide range of vulnerabilities, including:
Buffer overflows:
These occur when a program tries to store more data in a buffer than it can hold, which can allow an attacker to execute arbitrary code.
Format string vulnerabilities:
These occur when a program incorrectly formats a string, which can allow an attacker to inject malicious code.
Injection attacks:
These occur when an attacker injects malicious code into a program, such as through a SQL injection or cross-site scripting (XSS) attack.
Vulnerable APIs:
These occur when a program uses an API that has known vulnerabilities.
In mobile app security, Dynamic Analysis is essential for identifying vulnerabilities that emerge when the app interacts with the mobile ecosystem. For example, testing a fitness app’s GPS and data synchronization features under different device conditions can reveal unique vulnerabilities.
How It Works
Dynamic Code Analysis is a process where software is analyzed in real-time as it runs, to identify issues that only manifest during execution. This contrasts with static code analysis, which examines code without executing it. For example, a web application might be dynamically tested to see how it handles simultaneous user logins or unexpected user inputs, revealing runtime errors or security vulnerabilities like SQL injections.
Execution of Software:
The software is run in a controlled environment, often with a variety of test cases. For instance, a mobile app might be tested under different network conditions to see how it handles data transmission or loss of connectivity.
Monitoring and Analysis:
Tools monitor the running software’s operations, such as memory and CPU usage. For example, a tool might detect a memory leak in an application when it observes an unexpected increase in memory consumption over time.
Detection of Issues:
Issues like security vulnerabilities or performance bottlenecks are identified. For instance, a dynamic analysis tool might uncover a buffer overflow vulnerability during a stress test.
Reporting:
Detailed reports are generated, pinpointing the location and nature of the issues. These reports might include stack traces or memory dumps to help developers understand and fix the issues.
Types of Dynamic Code Analysis
Performance Testing:
This involves analyzing how the application performs under various conditions. For example, a video streaming app might be tested for its load handling capabilities to ensure smooth streaming during peak usage times.
Memory Profiling:
This focuses on how an application uses memory, identifying potential leaks. An example would be a game app being monitored for memory usage to ensure it doesn’t consume excessive system resources.
Security Testing:
This type of analysis looks for vulnerabilities that could be exploited by attackers. For instance, testing a financial app for how it handles SQL injection attacks.
Quality Assurance:
Ensures the application behaves as expected. For example, testing a navigation app to ensure it provides correct directions under different user inputs and conditions.
Advantages of DAST
Real-World Testing:
Dynamic analysis simulates real-world scenarios, providing insights into how software behaves in practical situations. For example, testing how a messaging app handles network fluctuations can reveal its robustness in real-world use.
Comprehensive Vulnerability Detection:
It’s particularly effective for finding complex runtime vulnerabilities. For instance, identifying race conditions in a multi-threaded application that only occur under specific timing conditions.
User Experience Insights:
It can reveal issues affecting user experience, like slow response times or crashes. For example, testing a photo-editing app for responsiveness when applying filters can uncover performance issues.
Limitations of DAST
Resource Intensive:
Requires significant resources and time, as it involves running the software in various scenarios. For example, thoroughly testing a cloud storage app for all possible user interactions can be time-consuming.
Late Detection:
Issues are often found later in the development cycle, which can make them more expensive to fix. For instance, discovering a critical security flaw in an e-commerce app just before its scheduled release can lead to costly delays.
Limited by Test Scenarios:
The effectiveness depends on the test cases used. If certain scenarios are not tested, like a rare combination of user inputs, vulnerabilities in those scenarios may remain undetected.
Static (SAST) Vs Dynamic (DAST) vs RASP – How are They Different?
Static, Dynamic, and Runtime Application Self-Protection (RASP) attacks refer to different methodologies and stages at which security vulnerabilities are exploited in applications.
Understanding the differences between static attacks, dynamic attacks, and RASP is essential for comprehensive application security. Static attacks focus on vulnerabilities in non-running code, dynamic attacks exploit flaws during runtime, and RASP provides a proactive, real-time defense mechanism within the application. Each plays a critical role in a layered security strategy to protect applications from various cyber threats.
Here’s a breakdown of how they differ:
Static Attacks:
Static attacks are a type of cybersecurity threat that targets vulnerabilities in an application’s source code or compiled binaries. These attacks are carried out before the application is actively running. Understanding static attacks is crucial for developers and security professionals to secure applications at the code level.
Nature of Attacks:
Static attacks exploit vulnerabilities that can be identified through the analysis of static code or binaries, without the need for the application to be in execution.
Examples include exploiting unpatched vulnerabilities found in the application’s binaries or using hard-coded credentials embedded in the code.
Dynamic attacks
Dynamic attacks occur during the runtime of an application, exploiting vulnerabilities that become apparent when the application is active and interacting with users or systems. These attacks are dynamic in nature and require different strategies for detection and prevention compared to static attacks.
Nature of Attacks:
These attacks target vulnerabilities that manifest during the application’s runtime, exploiting flaws in real-time operation and user interaction.
Common examples include SQL injection and Cross-Site Scripting (XSS) attacks, where attackers exploit the application’s runtime interactions.
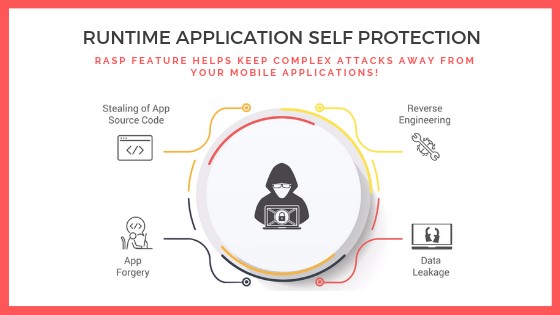
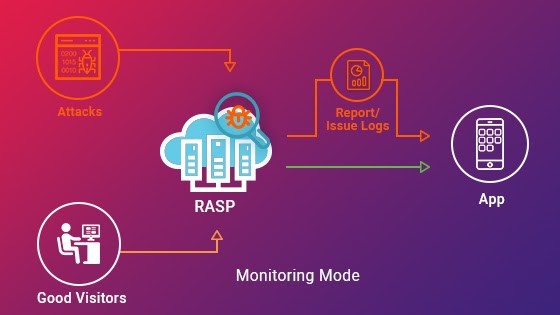
RASP
Runtime Application Self-Protection (RASP) is a security technology that protects applications from attacks in real-time. Unlike static or dynamic attacks, RASP is a defensive mechanism that integrates with an application to identify and mitigate threats as they occur during runtime.
Nature of Attacks:
RASP is designed to protect against a variety of attacks in real-time, actively monitoring and responding to threats within the application.
Examples:
RASP systems can detect and block attacks like SQL injections as they happen and prevent unauthorized data access or modifications
About AppSealing RASP
AppSealing is a security solution specifically designed for mobile applications. It focuses on protecting apps against various types of threats without requiring access to the source code.
Here are some key aspects of AppSealing:
-
No-Code Approach:
One of the standout features of AppSealing is its no-code approach to security. This means that app developers can implement security measures without needing to write additional code or modify their existing codebase. This approach simplifies the process of securing mobile applications, making it accessible even for those without specialized security expertise.
-
Real-Time Protection:
AppSealing provides real-time protection against a range of threats, including common vulnerabilities and exploits that target mobile applications. This includes protection against reverse engineering, tampering, and various forms of data breaches.
-
Platform Support:
Typically, AppSealing supports major mobile platforms like Android and iOS, ensuring that a wide range of mobile applications can benefit from its security features.
-
Ease of Integration:
The solution is designed for easy integration into existing app development workflows. This means that developers can add robust security features to their apps without significant changes to their development process.
-
Focus on Mobile App Security:
AppSealing is specifically tailored for mobile applications, which means its security features and protections are designed to address the unique challenges and threats faced by mobile apps.
-
Compliance and Data Protection:
By providing advanced security features, AppSealing helps mobile apps to comply with various data protection regulations and standards, which is crucial for apps handling sensitive user data.
Conclusion:
Understanding the nuances of Static and Dynamic Mobile Application Attacks, along with the implementation of Runtime Application Self-Protection (RASP), is crucial in the realm of mobile application security. Static attacks, which exploit vulnerabilities in the source code or compiled binaries, highlight the importance of thorough code analysis and secure coding practices. These vulnerabilities, often overlooked during development, can lead to significant security breaches if not addressed early.
On the other hand, dynamic attacks emphasize the vulnerabilities that emerge during the runtime of mobile applications. These attacks exploit flaws in real-time operation, such as improper handling of user inputs or insecure communication channels, underscoring the need for rigorous testing and monitoring of applications in their operational environment.
AppSealing RASP platform stands as a pivotal technology in this landscape, offering real-time protection by integrating directly with mobile applications. It actively monitors and mitigates threats as they occur, providing an essential layer of defense against both known and unknown vulnerabilities. RASP’s ability to respond instantaneously to attacks during runtime complements the preventative measures taken during the development stages through static and dynamic analysis.
Together, these approaches form a comprehensive security strategy. While static and dynamic analyses are proactive measures taken at different stages of the application lifecycle, RASP provides a reactive defense mechanism during the application’s operation. This multi-layered approach is vital in safeguarding mobile applications against the evolving landscape of cyber threats, ensuring the protection of sensitive data and maintaining user trust in an increasingly digital world.