India’s financial sector is in the middle of an exciting yet challenging transformation. As digital technologies grow, so do the risks lurking in the shadows. Cyber threats aren’t just headlines anymore—they’re real, pressing issues for businesses. To tackle this, SEBI launched the Cybersecurity and Cyber Resilience Framework (CSCRF). It’s not just about rules; it’s a shield to help organizations safeguard their operations and rebuild quickly if something goes wrong.
Why the CSCRF Matters
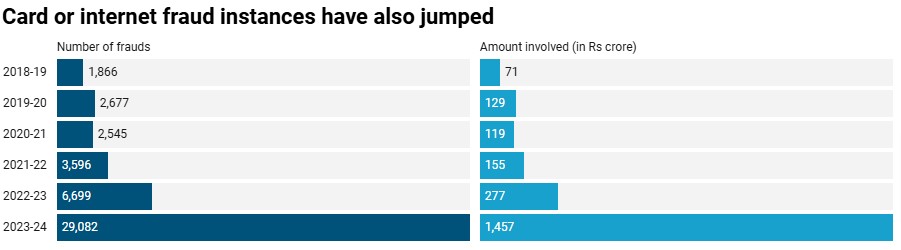
The scale of cyber risks today is staggering. Did you know over 1.5 million complaints were registered on the National Cyber Crime Reporting Portal recently?
That number is hard to ignore and paints a serious picture of how vulnerable organizations are. Financial services, unfortunately, often find themselves in the crossroads, with cyber incidents shooting up by 60% in a year.
SEBI’s CSCRF isn’t about ticking boxes for compliance. It’s about protecting trust—trust from clients, stakeholders, and everyone relying on these institutions. Beyond meeting regulatory requirements, the framework pushes for adopting smart cybersecurity practices that ultimately strengthen the industry as a whole.
The scale of cyber risks faced by the financial sector has grown significantly in recent years. Meanwhile, over 1.5 million complaints were registered on the National Cyber Crime Reporting Portal, revealing the extent of vulnerabilities faced by organizations. This data underscores the pressing need for SEBI-regulated entities (REs) to implement the CSCRF.
Governance and Oversight
Good governance is where it all starts. Without clear leadership and accountability, it’s tough to stay ahead in a constantly shifting threat landscape. An Information Security Committee (ISC) can work wonders here, prioritizing tasks, crafting policies, and ensuring compliance. But here’s the thing—governance isn’t just about policies on paper. Board members need to be engaged, not just passively informed. When they understand the threats and their implications, the organization is better prepared. On top of that, empowering employees creates a culture where security becomes everyone’s job, not just the IT team’s.
Role of Information Security Committee (ISC)
There is a dedicated Information Security Committee (ISC) tasked with overseeing cybersecurity efforts and formulating policies, setting strategic objectives, and ensuring compliance with regulatory requirements.
Furthermore, board-level oversight is essential in governance. Board members must be actively engaged in understanding the cybersecurity landscape and its implications for the organization.
Regular reviews of cybersecurity policies are also a key aspect of governance. Organizations must ensure that their policies are not only comprehensive but also adaptive to the evolving threat landscape. This involves periodic assessments to identify gaps and update policies accordingly, keeping pace with technological advancements and emerging cyber threats.
Risk Assessment and Management
Each organization has unique goals, challenges, and dependencies. The first step is figuring out what truly matters. Is it protecting sensitive customer data? Ensuring compliance? Securing third-party connections? Without clarity, managing risks is like playing darts blindfolded. Leadership needs to steer the ship here. Assigning someone like a Chief Information Security Officer (CISO) is critical, but that’s just the beginning. Everyone in the organization needs to know their role, whether it’s recognizing phishing attempts or following access control policies.
Information Security Policies
Policies are the backbone of any cybersecurity strategy, but they need to be practical, not theoretical. SEBI’s framework encourages organizations to create policies tailored to their actual needs. These should clearly define roles, outline risk management strategies, and include step-by-step plans for incident response. Getting input from various teams makes a big difference so that they don’t look great on paper but are impossible to follow in real life aren’t much use. And training? That’s where it all clicks. Teaching employees about phishing, password hygiene, and data protection ensures everyone’s on the same page.
Access Control Measures
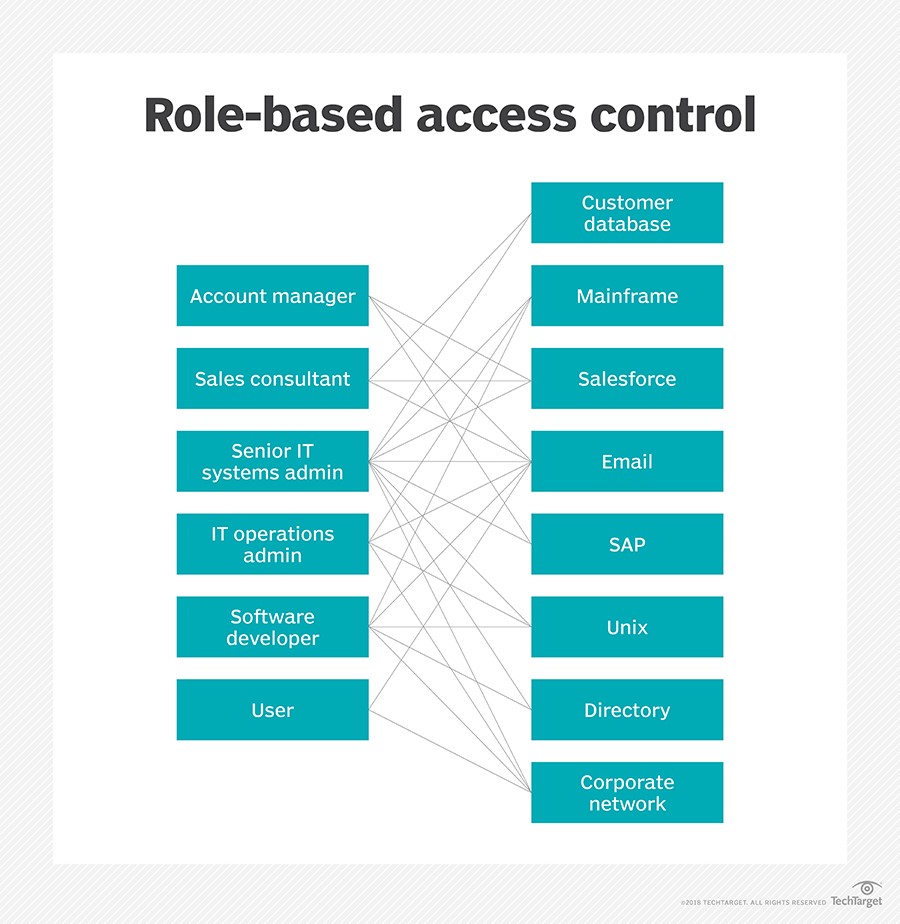
Access control might sound like an IT buzzword, but it’s one of the simplest ways to tighten security. Role-Based Access Control (RBAC) ties permissions to roles instead of individuals, making it much easier to manage. Add Multi-Factor Authentication (MFA), and you’ve got another layer of defense. Whether it’s a code, a fingerprint, or facial recognition, MFA ensures that even if someone’s password is compromised, the account stays secure. Regularly auditing access permissions is another must—people change roles, leave organizations, and permissions tend to pile up unnecessarily.
Network Security
It is imperative to understand that Network security isn’t just about firewalls and software—it’s about creating an environment where threats can’t get a foothold. Firewalls act as the gatekeepers, while Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) keep a watchful eye for anything unusual and act swiftly to neutralize threats.
Even small details, like closing unused ports or updating firmware, can have a big impact. Secure protocols such as SSH and TLS add another layer of safety, especially for sensitive data transfers. And let’s not forget MFA for admin accounts—it’s a simple step that goes a long way in preventing unauthorized access.
Cybersecurity is no longer optional—it’s essential. SEBI’s CSCRF offers a practical approach to building resilience in the financial sector. By adopting these measures, organizations can do more than just survive—they can thrive in a digital-first world, with trust and security as their foundation.
Using secure protocols like SSH and TLS further ensures that sensitive information stays private while moving through your network.
Firmware updates patch vulnerabilities that attackers are always on the lookout for, making them a key part of staying ahead in the cybersecurity game.
Data Protection and Privacy
The CSCRF emphasizes encryption as one of the best tools to keep data secure, whether it’s sitting idle on a device or being sent across networks. For data at rest, methods like AES-256 and RSA encryption offer rock-solid security. Adding Full-Disk Encryption (FDE) and File-Level Encryption (FLE) can provide even greater protection, ensuring both entire systems and individual files are locked down.
When data is being transferred, secure protocols like TLS/SSL are essential for safeguarding emails and file exchanges. Using VPNs or IPsec tunnels creates private pathways for communication, giving organizations an added layer of confidence.
The framework also stresses the importance of preventing data leaks before they become a problem. Data Loss Prevention (DLP) tools track how information moves through your systems and flagging anything unusual. These tools don’t just monitor—they can recognize sensitive information and block unauthorized attempts to share it. By integrating with cloud platforms, email systems, and devices, DLP solutions provide comprehensive coverage, helping businesses stay ahead of potential risks and keep critical data under control.
Incident Management and Response
Dealing with security breaches can be challenging, but preparation can make all the difference. To help organizations respond effectively, the CSCRF emphasizes two key steps:
-
Assembling an Incident Response Team (IRT):
- Include technical experts like IT professionals and cybersecurity analysts who can address technical issues.
- Add legal advisors to manage compliance and PR specialists to handle public communication during a crisis.
- Build a team that’s diverse in expertise and ready to act swiftly when needed.
-
Crafting and Testing an Incident Response Plan (IRP):
- Develop a practical plan that outlines clear roles and responsibilities during an incident.
- Incorporate step-by-step processes for identifying, containing, and resolving threats.
- Regularly test the plan with real-life scenarios to ensure it works when it matters most.
By creating a well-prepared team and a tested plan, organizations can respond more effectively and minimize disruption during security incidents.
Business Continuity and Disaster Recovery (BCDR)
Disruptions can happen anytime, but having a strong BCDR strategy ensures organizations are ready to handle them. The CSCRF suggests focusing on:
-
Building a Business Continuity Plan (BCP):
- Identify the processes, technology, and people critical to keeping operations running during a crisis.
- Develop step-by-step procedures to maintain these essentials, even in challenging situations.
- Don’t forget to include external partners, such as key suppliers, in the plan.
-
Preparing a Disaster Recovery Plan (DRP):
- Focus specifically on restoring IT systems—like servers and networks—as quickly as possible.
- Prioritize systems based on their importance and set clear recovery timelines.
- Test the plan often to ensure everything works as expected when it’s needed.
Together, these plans help organizations stay resilient, keep essential operations running, and recover quickly from unexpected events.
Training and Awareness
Cybersecurity isn’t just about tools and systems—it’s about people. Employees are often on the front lines when it comes to identifying and managing threats, which makes their training essential.
-
Start with everyday skills:
Teach your team how to identify phishing emails, set strong passwords, and handle sensitive information responsibly. These foundational skills can make a huge difference.
-
Make training interactive:
Run phishing simulations to give employees real-world practice in spotting scams. These exercises can be eye-opening and help reinforce lessons in a practical way.
-
For your IT and security teams, go a step further.
- Offer advanced training on topics like threat detection and response. Encourage certifications that build expertise and confidence, ensuring they’re equipped to tackle complex challenges.
Compliance and Reporting
Regulations like SEBI’s guidelines aren’t just about ticking boxes—they’re about ensuring trust and accountability. Staying compliant doesn’t have to be overwhelming if you approach it methodically:
Designate a team to stay updated on SEBI’s communications. Their job is to evaluate how changes affect your operations and recommend updates to your processes. Keep your policies dynamic: Review and revise them regularly to ensure they’re in step with evolving requirements and remain practical for your team.
Audit logs are another critical area where precision matters. To make them work for you:
- Use a centralized system for collecting and managing logs. This makes it easier to retrieve and review data when needed.
- Secure your logs with tamper-proof measures to ensure their integrity.
- Follow retention guidelines from SEBI to avoid compliance issues and keep your records in order.
By integrating these steps into your regular workflows, you’re not just meeting regulatory demands—you’re showing stakeholders that cybersecurity and transparency are priorities.
Vendor and Third-Party Management
Partnering with vendors and third-party providers is an essential part of modern business, but it often comes with security challenges. Recognizing these risks, the CSCRF encourages organizations to take proactive steps to manage these relationships securely.
Start with a Thorough Security Review: Before entering into any agreements, take time to evaluate a vendor’s cybersecurity practices. Look for their track record in safeguarding data, their use of encryption, and whether they have established incident response protocols. Regular reviews shouldn’t stop after onboarding—continuous checks ensure that standards remain consistent.
Draft Contracts with Clear Expectations: A strong contract sets the tone for accountability. Include specifics about:
- How sensitive data will be managed and protected.
- The steps and timelines for notifying your organization in the event of a breach.
- Defined accountability and consequences if security issues arise.
Monitor Regularly to Stay Ahead: Once a vendor is onboarded, keep an eye on their practices. Periodic audits and evaluations can reveal vulnerabilities early, giving your team a chance to address concerns before they become major problems.
Implementing CSCRF
When it comes to putting CSCRF into action, it’s not just about checking boxes. It’s about embedding security into how the organization operates every day. Here are a few ways to do that:
- Get leadership involved early and often so security goals align with business priorities.
- Stay on top of risks by running regular assessments and adjusting strategies as needed.
- Set up access controls to ensure employees only get to what they need for their roles.
- Keep security policies straightforward and easy for teams to follow.
- Use tools like firewalls and encryption to protect sensitive information and critical systems.
- Prepare for incidents by having clear, tested response plans ready to go.
- Build continuity plans to keep things running smoothly during unexpected disruptions.
- Train employees often so they’re aware of the latest threats and know how to handle them.
- Maintain detailed records to show compliance with regulatory requirements.·
- Watch over vendors to ensure their security practices align with your organization’s standards.
Conclusion
The Cybersecurity and Cyber Resilience Framework (CSCRF) represents a significant step forward in securing India’s financial sector against cyber threats. By providing a comprehensive set of guidelines covering everything from governance to incident response, it helps organizations build robust cybersecurity strategies.
However, implementing the CSCRF is not a one-time effort. It requires ongoing commitment, regular updates, and a willingness to adapt to new threats and technologies. Organizations that successfully implement the CSCRF will not only meet regulatory requirements but will also be better positioned to protect their assets, maintain customer trust, and thrive in an increasingly digital financial landscape.
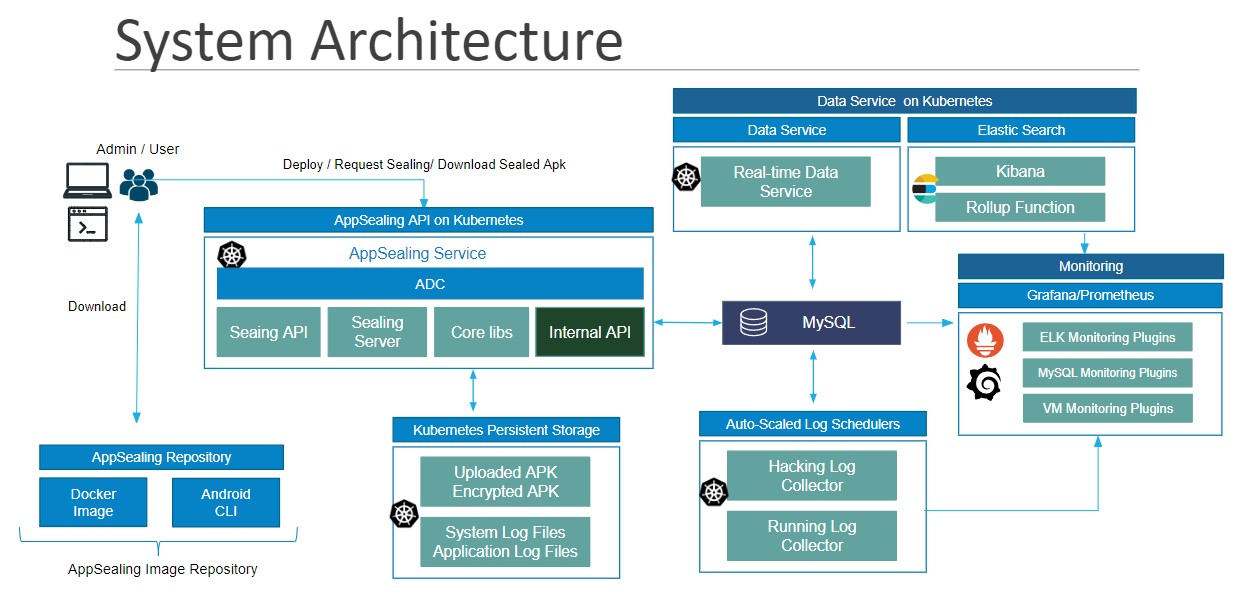
Why AppSealing Could Help You Navigate CSCRF
SEBI’s CSCRF has a lot of moving parts, and figuring out how to stay secure while checking all the boxes isn’t easy. AppSealing was made to simplify things and it helps you protect your mobile apps, secure your data, and handle the tough stuff.
Focused on Real Security
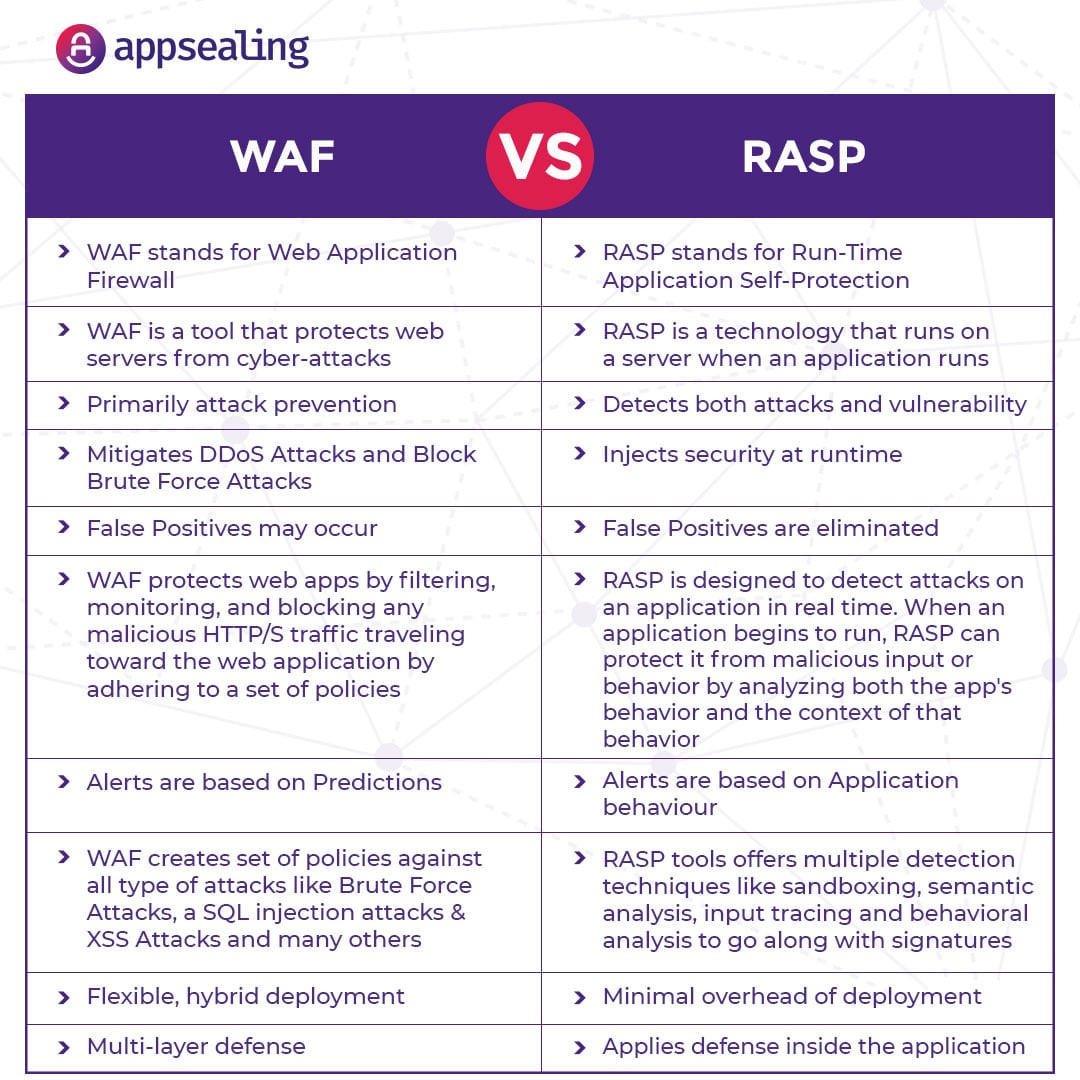
Giving your mobile apps the protection they need, AppSealing covers threats like reverse engineering and tampering. Data breaches? That too. One of the standout features is Runtime Application Self-Protection (RASP). Even if someone tries to tamper with your app while it’s running, AppSealing steps in to block it.
On top of that, it keeps your data secure with encryption—both when it’s stored and when it’s moving between systems. This isn’t just nice to have; it’s a key part of SEBI’s requirements. Plus, it handles data localization rules, so you don’t have to worry about compliance slipping through the cracks.
Proactive, Not Reactive
Good security doesn’t wait for something to go wrong. AppSealing monitors your apps constantly. Whether it’s malware, unauthorized access, or vulnerabilities, it spots the problem early so you can fix it fast.
Built for Compliance
Meeting CSCRF requirements isn’t just about avoiding penalties—it’s about protecting your organization. AppSealing aligns directly with SEBI’s goals: anticipate risks, respond quickly, and recover smoothly. It’s also compliant with global standards like ISO 27001 and PCI DSS, which makes it a great fit if you’re working in a regulated industry.
No-Code Simplicity
One of the best parts about AppSealing? You don’t have to rework your app to use it. No big code changes, no lengthy adjustments. It’s plug-and-play, which means you can start securing your apps without adding extra strain on your developers. It works with native apps, hybrid setups, and cross-platform builds, so compatibility won’t be an issue.
Trusted by Businesses
AppSealing isn’t just another security tool. It’s already being used by companies around the world, especially in industries where compliance is critical. For businesses following SEBI’s CSCRF, its localized features help simplify some of the trickiest parts of staying compliant.
Need help along the way? Their support team is there for you, whether you need technical advice or guidance with regulatory requirements.
Is It the Right Fit?
AppSealing is designed to make your life easier. It’s not just about security; it’s about simplifying the entire process of protecting your apps and meeting compliance goals. If you’re dealing with CSCRF challenges, this could be the solution that helps you get ahead.