Poor software development could open the door to cybercriminals. Applications nowadays must contend with a constant barrage of malicious activity from bots and automated scripts designed to probe for vulnerabilities that could yield access to web apps hosting valuable content such as proprietary data or customer records.
The sheer disconnect between software developers and IT security teams ends up securing a spot in the unwanted lot of internal application vulnerabilities considered as high or critical risks.
Historically, web developers had limited choice when it came to static application security testing (SAST) tools, but that’s no longer the case. With the inception of open source frameworks and languages like NodeJS, SAST-enabled integrations have exploded in popularity yet many of these options are still largely unknown to the development community.
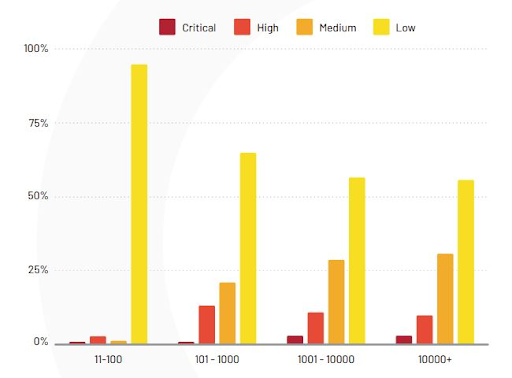
The broke down of severity of vulnerabilities according to company size
Source: EdgeScan
SAST – Static Application Security Testing
Static application security testing (SAST), or static analysis, tests the source code of applications to uncover definite vulnerabilities that could be a serious threat to your business.
How Does SAST Work
Static Analysis tools are designed to analyze and detect defects in code, ranging from minor issues with code readability and style, to potential vulnerabilities that can result from the use of improper programming constructs or be exposed by changes in the environment.
Akin to how a security guard’s role is to prevent anyone with bad intentions from entering the premises, a Static Code Analyzer looks over source code in order to identify pieces of code that can allow any anonymous user to inject signs of malicious activity onto a website or application.
Benefits of SAST
- Static application security testing (SAST) scans source code looking for anomalies that may indicate a security weakness.
- Following shifting security ‘Left’, SAST tools can be implemented early in the SDLC (Software Development Life Cycle) utilized before your code is even compiled, which allows for detecting vulnerabilities in the build stage.
- Static application security testing (SAST) reports real-time bugs
- SAST tools can be easily added to a development team’s already established toolset. This will allow them to run scalable testing on their codebase – giving developers the freedom to choose how and when they want to test their applications without putting undue limitations on themselves or their projects.
Drawbacks of SAST
It doesn’t provide any insight into how applications or their elements behave within dynamic environments, so it’s important to conduct additional testing in dynamic environments whenever possible.
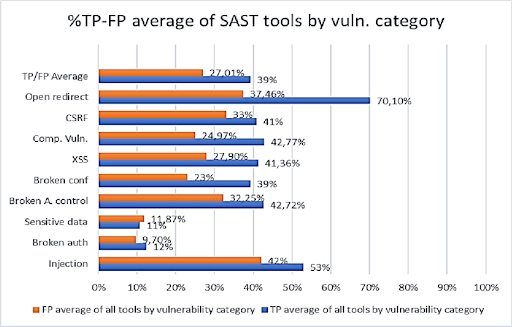
Static application security testing assessments have high probability reporting false positives which can lead to an inflated sense of a project’s vulnerabilities.
Static application security testing (SAST) is only as good as its last scan and therefore it’s important to be able to run a new scan every few hours in order to track the most recent updates on reports.
Tools used for SAST
Source analysis security testing tools are used by software engineers to scan their source code for additional risks in what are otherwise readily available frameworks or libraries that line the shelves of essential coding resources which have already been tested and approved as trusted.
Starting early with your application security testing can be crucial, especially if you are building an app by considering it the new Facebook.
There are also earlier detection tools available and that’s where Static Application Security Testing (SAST) tools shine. They operate prior to deployment of apps in the production environment and can help identify defects that could lead to potential vulnerabilities in your software or website.
1. SonarQube
SonarQube is a SAST tool used by many organizations to find bugs. It is a lightweight platform that doesn’t consume much disk space and memory. SonarQube’s Community Edition provides static code analysis catering for around 15 languages including Java, JavaScript and Python based off of your cloud platform of choice.
2. Synopsys
As part of its commitment to help organizations achieve their goals by delivering innovative solutions, Synopsys provides integrated software development tools (SDT) and services that enable companies to develop secure products faster, at lower cost.
Find critical defects and vulnerabilities by finding software bugs before they’re released into production. Synopsys understands the frameworks underlying the development, so it is able to provide highly accurate analysis that keeps developers from being distracted by false positives.
3. Veracode
Veracode comes with rapid static analysis that outpaces human testing and provides automated security feedback directly in the IDE and even from within your CI/CD pipeline. It provides rapid security feedback as your application builds and tests, providing more quality assurance.
Veracode has a full policy scan that conducts full reviews of a company’s IT infrastructure and gives clear guidance on how to fix any issues found so that one can deploy their product with confidence.
4. Checkmarx
Checkmarx is an application security testing tool that comes with numerous features for finding vulnerabilities in programs.
It’s super easy to set up, supports numerous languages without configuration, and does not require heavy modification. It also has a better signal-to-noise ratio than many other tools like it.
5. AppSealing
Our very own Appsealing’s Static Application Security Testing (SAST) has a set of technologies designed to analyze application source code, binaries, and byte code in a non-running state, revealing security vulnerabilities that make mobile applications susceptible to attacks.
No app code is executed while using SAST, so there’s no fear of posing a threat to the mobile or network environment.
AppSealing provides real-time feedback to the developers. This gives them a solid foundation for fixing their mistakes on time, so that their product remains uncompromised and passes onto the next phase of the software development life cycle (SDLC) in top shape.
How Can We Differentiate SAST and DAST?
There are two different types of application security testing—SAST and DAST. SAST testing and DAST testing are both application security testing methodologies, but their approaches tend to be similar in a sense that they both identify flaws in applications although different to one another.
A report may state that your application has potentially vulnerable areas, but this doesn’t mean you are doomed. In fact, it could help you identify what needs fixing as well as guide towards developing a long-term strategy for plugging those holes.
In order to understand the difference between dynamic application security testing (DAST) and static application security testing (SAST), let’s look at some of the 5 key differences and how these two methods identify flaws in an application.
SAST VS DAST
| SAST |
DAST |
| Static Application Security Testing is a type of White Box security testing. It is made possible thanks to code compilation feature provided to developers by web application server software and other factors. | Dynamic Application Security Testing refers to a class of Black Box security testing where you do not have access to the internal framework that made up the application, source code, design and its documentation. |
| Static Application Security Testing (SAST) is where vulnerability testing is done from the inside of an application outwards. | In Dynamic Application Security Testing, outside-in security testing is performed in which the application and its architecture is analyzed based on what an attacker would think of. |
| Static Application Security Testing doesn’t require the deployment of any application. | Dynamic Application Security Testing requires a running application. |
| Static Application Security Testing tool scans only instances of code that are stored in memory, which makes it difficult to discover any vulnerabilities that could only be triggered when the code is executed at runtime. | Dynamic Application Security Testing is a method of finding vulnerabilities where the code is actually running by checking for anything that could be modified from its original source, such as the data and control flows. |
| Static application security tools take up more time and money to use than other ‘in place’ security testing alternatives. If a static tool is used on a development platform the need for recompiling can cause a delay in production delivery time. | Dynamic Application Security Testing tool works like a hacker, probing for vulnerabilities and tests for mistakes that could leave a system open to compromise. It also finds SQL Injection and injection flaws, so you can quickly secure your backend from malicious attack. |
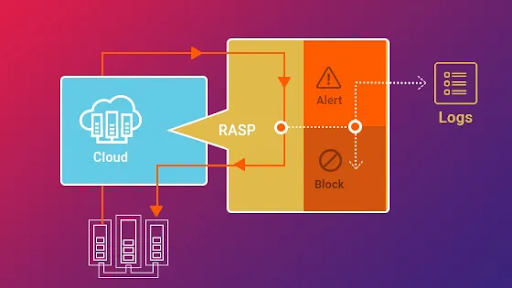
Where does RASP fit into the picture?
Runtime application self-protection (RASP) being a server-based technology works with applications to prevent attacks, and they believe that it is essential not only to analyze traffic, but also the behavior of users.
Runtime application self-protection (RASP) keeps a lookout for malicious activity that tries to take over your app. If the security tool finds any traces of something fishy, it will stop it from executing.
One of the biggest benefits of Runtime Application Self-Protection technology is that it protects applications from malicious attacks without needing outside protection, like a firewall. RASP works inside the application to fend off cyberattacks even before they have a chance to spread.
The National Institute of Standards and Technology advises that Runtime Application Self-Protection (RASP) be used within applications to reduce the risk of security vulnerabilities.
4 Key Benefits of RASP
- The RASP tool is here to save you from the dangers of not conducting code reviews every so often. This tool can help you conduct effective penetration testing to detect and eliminate vulnerabilities in your code before it’s too late
- You get better cyber security incident response with RASP tools because you can quickly detect and assign indicators of compromise (IoCs) to observations that RASP has already ingested earlier, even if those IoCs did not exist when the observations were made.
- Runtime Application Self-Protection (RASP allows development teams to be more prepared and aware of what their application is doing at any given time. Using runtime analysis, developers can spot patterns that use up resources or do not need to take place in certain areas. This leads to them being able to fix problems that may be going on without the knowledge of anyone else on the team.
- Its seamless integration and no-code deployment leads to minimal impact on the app’s overall performance; therefore, it can be said that RASP is an all-encompassing, application security choice.
How can SAST, DAST & RASP be used in tandem?
When we think of using DAST, SAST and RASP methodologies, it needs to be understood that everything will depend on the kind of penetration test you need for your business.
By using a combined approach of using both SAST and DAST scanning techniques, one can find more vulnerabilities and exploits which translate to fewer security risks.
Static applications security testing (SAST) is the ideal way to prevent vulnerabilities from entering your application when it’s still in development. Testing is always a good idea, especially since finding and fixing vulnerabilities early typically means easier maintenance when you address the problems later on.
For example, if you find a vulnerability early in the testing phase, you can potentially just make one change in your code instead of having to create two fixes for separate problems like you would have had to do if it was discovered at a later date.
On the other hand, employing dynamic application security testing (DAST) ensures customers are receiving only the very best applications from your team that have been thoroughly tested for any vulnerabilities that might compromise their data.
The heartbeat of any DevOps initiative is the combination of new and refined cultural and operational relationships between the development (Dev) team, quality assurance (QA), system administrators (SysAdmins), and security teams.
It’s sometimes difficult to get companies and individuals to provide you with data that allows you to analyze their application code. While some are hesitant when it comes down to giving out data which would be used in Static app sec testing, others struggle with other issues that they fear could become a potential problem.
In the case of code analysis, when used on dynamic applications, things are not bullish when it comes to getting information about the underlying causes of application vulnerabilities and are also ineffective in making security testing easier.
With RASP solutions, organizations can quickly and effectively secure infrastructure and applications by providing the missing piece necessary in more traditional estate-based scanning solutions.
Runtime Application Self-Protection (RASP) limits the risk of introducing unexpected vulnerabilities or bugs in the target software. Complementing DAST and SAST tools, Runtime Application Self-Protection complements Dynamic Analysis Software Testing tools to help DevSecOps teams understand security risks in both software development processes, penetrating applications to prevent malicious attacks, mitigate risk through security awareness and accelerate DevOps adoption into their environment.
DevOps teams need to create applications that are fast and work within the speed at which technology continually advances, changing hardware and software configurations. And RASP could be the game changer.
AppSealing RASP
AppSealing is protecting More than 800+ mobile applications worldwide. Take a look with a demo