The instances of cyberattacks are not only growing in numbers but also in the nature of its complexity. Attackers are constantly in the lookout for a vulnerability to breach their target organization. According to the global consulting firm Accenture, USD 5.2 trillion of global value (2019–2023 estimates) is under threat due to cyberattacks.
On most occasions, businesses have to rely on more than just a basic virus scan. However, all companies need to test their defense mechanisms regularly to understand how prepared they are to handle a contingency. This is where penetration testing comes into play.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.

Penetration Testing
Penetration testing, or pen testing, is a form of ethical hacking where computer systems or a network of web applications are attacked by highly skilled security professionals to find vulnerabilities. The test can be automated, carried out manually, or even be a mix of both depending on the requirements.
The idea behind penetration testing is to identify possible entry points in the organization’s network and breach the defense mechanism of the target. Once the system is hacked, the security professionals gather as much information as possible and prepare a report that helps the company to take corrective measures and fortify their walls. Since the testing is carried out by people trying to help the organization, it is also known as the white-hat attack.
Penetration testing is also oftentimes confused with vulnerability scanning and some consider them to be the same concepts. However, the basic difference between the two is that vulnerability scan searches systems and reports on known vulnerabilities, whereas penetration testing is much more aggressive and attacks the organizations systems and intends to replicate real life attacks. You may learn more about the differences between the two from our earlier post here.
Why Penetration Testing is Important
No organization’s default security system is watertight. There are always tiny holes that need to be found and plugged. The importance of this method of cybersecurity can be gauged from the fact that in 2016, The Pentagon opened its doors to outsiders to test the defense of their unclassified computer systems. The 1,400 hackers who registered for the “Hack the Pentagon” program exposed 100 security threats that even an organization like the United States Department of Defense was not aware of earlier.
Here are a few reasons why organizations must employ pen testing professionals from time to time:
Discovering Vulnerabilities Before Attackers
A pen tester, under a controlled environment, carries out attacks the very same way hackers with malicious intent would do. They break their heads to find vulnerabilities that could potentially cause damage to the organization. They filter issues like software errors, poor configurations, inaccurate system settings, and other shortfalls. This helps organizations to understand vulnerabilities and correct them as soon as possible to avert any major attacks.
Reducing Network Downtime
IT system downtime can burn a hole in the pockets of business organizations. According to a Gartner report, organizations lose up to USD 5,600 on an average per minute due to this reason. A regular pen test reduces the downtime drastically, thus keeping the organization’s engine running smoothly.
Building a Safer Ecosystem
Pen testers not only find faults in the organization’s system but also suggest ways to tackle them. Experienced testers help their clients to understand their flaws and engage with the firm’s technical experts to build better defense mechanisms to avert potential attacks.
Protecting Reputation
Several factors go into building brand value and consumer trust. Every security mishap involving customers’ data directly affects the brand value and sales and even brings bad repute for the company, which big organizations cannot afford.
Types of Penetration Testing
To expose loopholes in a company’s security system, there are three types of pen testing models which can be employed: black-box testing, white-box testing, and gray-box testing, which are described below:
Black-Box Testing
During a black-box test, the tester has little to no information about the internal security structure of the system. So, the tester is much like a usual hacker who has to work his way through your systems. During Black Box testing, the tester will use general hacking techniques to gather information and infiltrate the security structure by exploiting the vulnerabilities. This system exposes the basic frontline vulnerabilities of a security structure.
White-Box Testing
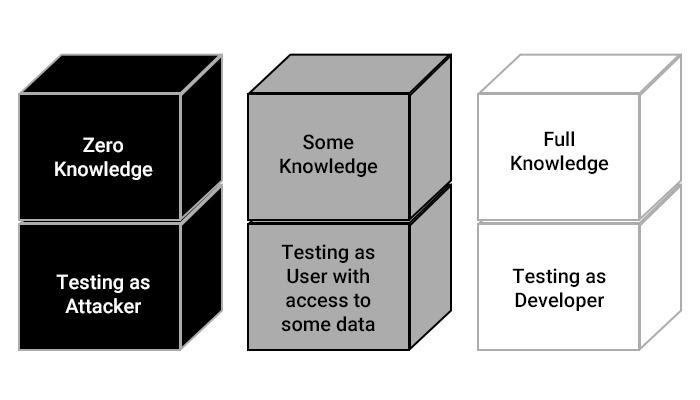
White Box testing is a full-fledged testing method where the tester is provided with full network and system information. This type of testing focuses on the in-depth and quick detection of vulnerabilities. Due to available information, the tester can directly focus on the target point and detect vulnerabilities, saving time and money for the clients.
Gray-Box Testing
As the name suggests, this method employs principles of both black- and white-box testing. The tester is provided with some information about the internal structure. Some minimal information like log-in credentials and other basic access information is provided to the tester. This type of testing is done to understand the damages a privileged user can cause to the internal structure. The tester will check the level of access that can be gained after gaining access to the internal setup. This method provides greater freedom to the tester who can choose to employ both manual and automated processes to find loopholes. This is by far the most effective method and improves the chances of zeroing in on possible vulnerabilities that are a little harder to detect.
These types of pen testing can be further divided into more specific groups, such as:
External Network Pen Test
External Network Penetration testing is the process of penetrating the network from external vulnerabilities. The tester will conduct a thorough examination of the information available externally and attempt to breach the security blocks with that information. So, the process is carried out offsite with ethical hacking techniques.
External network pen testing evaluates how your external security systems react to a cyberattack, and therefore, it is the most important and inevitable of all tests. Every large and small business uses some sort of external defense to restrict unauthorized access to the internal network, and the efficiency of that defense system can be assessed only with external testing. The results obtained from external pen testing can help you eliminate even minute vulnerabilities in the security structure.
Internal Pen Testing
Internal Pen Testing is the penetration test conducted on the internal network of the systems. The tester will recreate a scenario where the hacker has already gained access to the internal network. The tester will use various pen testing tools to exploit the vulnerabilities on the internal side of the network. Therefore, you can get a clear picture of the vulnerabilities and the amount of damage a hacker can do after gaining access to the systems.
Internal pen testing greatly improves your cybersecurity by exposing the vulnerabilities on the inner circle of the network. After these vulnerabilities are removed, it becomes difficult for a hacker to cause damage even after entering the network.
Social Engineering
Social engineering is fairly new in the pen testing scenario. Here, the tester will try to extract sensitive business information by connecting with staff via emails, phone, physical access, social media, and other modes of communication. The goal is to lure the employees into exposing sensitive information that a hacker can use to access the network and cause damage.
Social Engineering has become quite essential nowadays, especially due to the modern work-from-home system. Employees work from home, and there may be other devices with other devices and unprotected wireless networks that increase vulnerabilities greatly.
With social engineering testing, a business can understand the vulnerabilities and train the staff accordingly to prevent attacks. Usually, the employees are made familiar with the best practices of system handling that will ensure a risk-free social structure at work.
Application Penetration Testing
Mobile and web applications are extremely important for any online business nowadays. A lot of transactions happen online, and a lot of sensitive data is transferred via applications. And that is the reason why cybercriminals nowadays have a keen eye on applications.
Application penetration testing primarily focuses on exposing vulnerabilities and their severities so that you can clearly understand the security levels of your web and mobile apps. It also helps you in improving the security structure of your applications to provide a secure online experience to the users.
Wireless Testing
Wireless testing is essential if you are using a common wireless network for business operations. Wireless networks have a high possibility of vulnerability due to several interconnected devices in the network. The network chain can contain loopholes that may sometimes go unnoticed without robust penetration testing.
As you can see, penetration testing covers all aspects of a business network to ensure maximum detection of vulnerabilities. There are other penetration testing types such as cloud penetration testing, IOT penetration testing, crypto currency penetration testing, and several other types depending on the needs of various businesses worldwide.
Penetration Testing Methods
Organizations employ different types of strategies to safeguard their networks, applications, and computers against cyberattacks. They involve using in-house and external professionals and agencies to mimic attacks as if they were taking place in a real-life scenario. Below are some strategies organizations employ to preempt hacking attempts:
Targeted Penetration Testing
In this type of testing, the organization’s IT professionals coordinate with pen testers and keep each other informed at all stages of the process. The tests are carried out on an open server, so that all developments can be monitored, recorded, and analyzed by both parties.
External Penetration Testing
It is a very conventional approach to pen testing, where ethical hackers try to breach internal networks through external servers, clients, and people. The pen tester’s main objective is to gain access to a particular server through whatever means it can be done within legal limits. Testers may take advantage of a weak web application or even coax a user to divulge sensitive information, like passwords, over a phone call.
Internal Penetration Testing
The primary objective of internal pen testing is to analyze the company’s defense mechanism in case of an attack where the hacker has breached the initial network. The pen tester mimics internal attacks that often target the lesser important systems. Then, they launch an attack on the primary target with the help of the information gained earlier.
Blind Penetration Testing
Testers carry out an attack using publicly available information. It is as close as it gets to a real attack, where ethical hackers have to work their way in taking cues from the information already at hand and not depend on any help from the organization even when it has authorized this type of testing.
Double-Blind Penetration Testing
This process, also known as zero-knowledge testing, is even more covert than blind testing. Testers have little or no knowledge about their target’s defense systems, and, likewise, the target company has no clue what approach, scale, and duration attackers will adopt to harm its systems. This approach needs highly skilled pen testers, as they have to rely on their experience to choose appropriate tools and methods to break into a company’s defenses.
Penetration Testing Phases
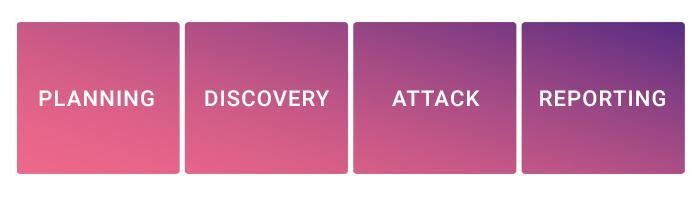
Professional testing is a systematic procedure that involves a step-by-step penetration system that provides a clear view of the detected vulnerabilities and their severities. Now let’s take a look at the various stages of professional pen testing.
Strategy Preparation
This is the initial stage where the tester develops a strategy based on the guidelines provided by the client. The client and the tester conduct several discussions to develop a precise plan targeting every required phase of network security. The types of tests, their need, the success rates, and other statistics are also transparently discussed to ensure client satisfaction. Once the plan is developed, the tester sticks to the strategy for the entire process of penetration testing.
Information Discovery
In the next stage, the tester scans the entire network structure and collects business information that can be used for penetration. Information like IP addresses, email addresses, names of important employees, personal information, job titles, and other potentially sensitive information is discovered and documented for testing. Professional testers may use various online and offline methods to gather this information, without breaching the terms mentioned in the initial plan.
Penetration
The third and most important part is penetration. During this stage, the tester will narrow down on each target and conduct different penetration attacks on them. These attacks are called ethical hacking, which is identical to a real-life cyber-attack scenario. The tester will try to exploit each vulnerability with an aim to expose the amount of damage it can cause. And The client will be provided with a clear demonstration of how a real-life cyberattack would look like on their business systems.
Assessments and Reports
Once all the penetration tests are complete and the vulnerabilities detected, the tester will assess the overall process and create a report for the client. Professional testers will categorize every vulnerability, according to the severity and threat level so that the client can understand and prioritize further actions accordingly.
Elimination
In this stage, the tester will conduct meetings with the client to discuss the vulnerability elimination process. The tester will provide transparent suggestions on how to ensure the best security on your network. Once approved by the client, the tester will then carry out the elimination process and close all loopholes and vulnerabilities in the security structure.
Retesting
Once all the vulnerabilities are cleared, the tester will conduct a repeat test to ensure there are no more gaps in the cybersecurity infrastructure.
These are the common stages of penetration testing that the professionals use to ensure the best results.
Penetration Testing Teams
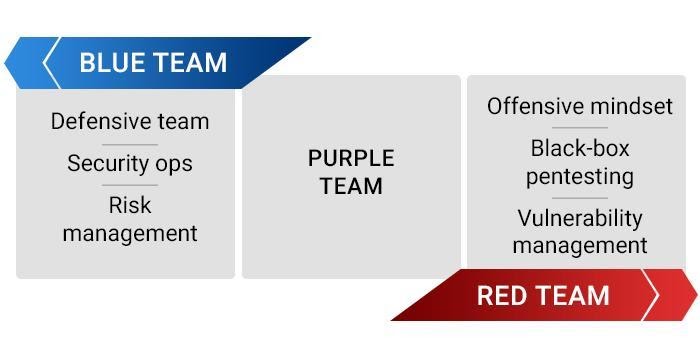
As seen above, penetration testing is an elaborate and detailed process and is not carried out by just one person or team alone. Testers are broadly categorized into three teams: Red, blue, and purple.
Although they are interconnected, each team has a distinctive and equally important role to play in the whole process. We define their roles below:
Red Team
This is the team directly tasked with penetrating the organization’s defense barrier and gaining access to the systems. It can be compared to the stealth team in armed security forces. The red team utilizes the latest hacking techniques and may even write their own scripts to develop a virus to attack targets, much like how a hacker with malicious intentions does. They infiltrate the systems using both physical and virtual techniques while trying their best to evade detection.
Blue Team
This team comprises highly skilled analysts from within the organization whose main role is to neutralize any attack to the company security system. They are tasked with the duty of finding out, handling, and weakening attacks orchestrated by the red team. It has to be on its toes all the time, foresee any emerging attack, and take necessary precautions to avert or minimize the damage. It needs to actively monitor traffic on the organization’s network and be ready to jump into action at the shortest possible time.
Purple Team
The target organization’s top security professionals make up this team. Its primary task is to observe how effectively the red and blue teams are working with each other. Eventually, the goal of the purple team is to learn about the vulnerabilities in the organization’s system and prepare a road map, which includes educating the current employees about security threats and reinforcing the security wall of the network.
Pen testers may also use some open-source pen testing tools to move quickly through the stages of testing.
Penetration Testing Tools
Pen-testing tools are software applications used by testers to carry out their activities efficiently. Depending on their goals, testers opt for tools that they feel best suit their requirements. There are countless testing tools, both paid and free, available on the web. Given below is a list of some of the widely used pen-testing tools:
Metasploit
It is an open-source framework widely used by both the red and blue teams. As it is an open-source, Ruby-based framework, Metasploit can easily be tailored for almost all operating systems. The framework is powerful and can detect vulnerabilities in network servers with ease.
Visit Website: Metasploit
Wireshark
It is a packet sniffer/network protocol analyzer that lets the tester view the happenings in the network in real-time with the minutest of details. This open-source project, which has been developed through contributions over the last two decades, effectively deep-scans several web protocols with ease. It is part of the kit of most testers due to its protocol analysis features that make accessing traffic in real time hassle free.
Visit Website: Wireshark
Kali Linux
This Linux distribution contains a powerful set of tools for pen testing, which has over 600 ethical hacking components. It is a highly advanced testing suite available on Linux machines. The tester needs to be well-versed in TCP/IP protocols to operate these tools effectively and carry out activities like code injection and password sniffing.
Visit Website: Kali Linux
Netsparker Security Scanner
It is one of the most popular pen-testing web applications. Testers can use Netsparker to detect anything from cross-site scripting to an SQL injection in websites and web applications. It can scan up to 1,000 applications in one go. It employs a proof-based scanning mechanism, guaranteeing maximum accuracy.
Visit Website: Netspark Security Scanner
Aircrack-ng
This open-source tool is the first choice of the testers who want to break into a wireless network. Pen testers can use this tool to monitor and analyze the Wi-Fi security mechanism of a target, collect data packets, and convert them into text files for further study.
Visit Website: Aircrack-ng
Limitations of Penetration Testing
Even if an organization regularly conducts pen tests, its system will not become foolproof due to certain limitations of the testing process. A pen test cannot eliminate all vulnerabilities, because, at the end of the day, the quality of the test depends on several factors, including the skill set of the testing team. Here are a few drawbacks in pen-testing processes that cast doubts over their overall effectiveness:
Skill and Experience of Testers
Penetration tests can be broadly divided into three sections: network, system, and web. It is highly unlikely that an objective result can be obtained if a tester specializes in one area and has only working knowledge of the other two. Since the dynamics of security structures keep changing at a rapid pace, it is difficult to find someone who is an expert in all three areas.
Time Constraint
Testers have a given period within which they have to find vulnerabilities, breach the systems, and prepare reports. Attackers are not bound by a time frame. They can plan an attack in leisure and carry it out when the target least expects it. Testers are also burdened with the task of recording every step they take and gathering evidence in the form of screenshots and documentation. An attacker, on the other hand, can carry out attacks without being bothered about making diary entries or similar laborious requirements.
Custom Exploits
Not all security systems can be breached using the standard pen-testing framework. Advanced systems need to be cracked by creating a custom attack plan with customized scripts. Writing custom code is an advanced skill. To avail the services of such highly skilled testers, a company needs to allocate a substantial budget.
Access Limitations
Companies often draw lines that the testers cannot cross. Only certain servers and segments that the organization has allowed to be scrutinized can be attacked by testers. But, in a real-life scenario, attackers are not bound by any contract or restrictions. This limits the actual efficiency of the test and may give the organization a false feeling of the system being watertight.
How often Should Penetration Testing be Conducted
Penetration testing is certainly not a one-time process. Once tested, your systems will surely be safe for a long time. However, as time passes, new undetected vulnerabilities may arise that can cause cyberattacks.
Therefore, it is important to test your network and systems more often. The best option is to set a regular time interval for testing. That way, you can be sure that your network is safe and regularly updated. Most businesses prefer to run a penetration test at least once a year, however, you can also do it more frequently according to your business needs.
Cyber threats change over time as hackers develop new methods to infiltrate systems. If you have partnered with a reliable service provider, they will notify you whenever a new threat is detected. So, a quick test whenever you get a notification would be a wise choice that ensures safety from the latest threats.
You must also remember to conduct penetration tests whenever your network and security infrastructure is changed or upgraded. Upgrades and changes in the existing setup often lead to new weak points that hackers can exploit.
Finally, it is advisable to conduct a social engineering test every once in a while. Businesses hire new employees who may not be well-familiar with the protocols and the best practices. A social engineering test will help you fish out such weak points effectively.
Conclusion
Despite its limitations, pen testing remains the most efficient way to mimic a real-life attack and test the defense mechanism of the target organization. However, given that it is carried out in a controlled environment and its efficiency is dependent on the testers’ skills, the results of this exercise should be taken with a pinch of salt.
Organizations should also understand that pen testing is not an alternative to the existing application security testing system, but it is there to supplement it. The information thus gathered can help companies plan their security budget in a better manner and developers create software/applications that withstand similar attacks in the future.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.