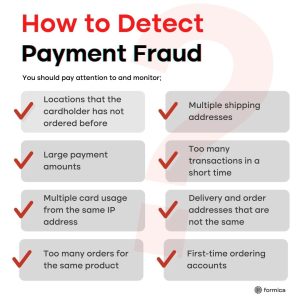
The scope of these challenges extends beyond unauthorized transactions, encompassing identity theft, account takeovers, and even instances of “friendly fraud,” where legitimate customers initiate unjustified chargebacks.
Consequently, payment fraud detection necessitates a multi-faceted approach that surpasses basic verification methods. It is not merely a matter of financial loss; rather, it entails a complex network of risks that demands sophisticated and adaptable solutions to safeguard economic ecosystems.
What is Payment Fraud?
Payment fraud is a complex and constantly changing form of deceitful or unlawful transactions that seek to gain financial benefits through unauthorized and deceptive activities. It encompasses a wide range of illicit actions, including unauthorized transactions across different payment channels such as credit cards, virtual checks, direct debits, and phone payments. Fraudsters frequently employ advanced methods to manipulate transaction data to appear legitimate, thus evading anti-fraud systems.
The emergence of instantaneous payments has brought forth fresh obstacles, as these transactions are final and concluded within mere seconds, necessitating the utmost importance of real-time fraud detection. Let us endeavor to comprehend the intricacies of payment fraud, a multifaceted and sequential procedure that demands sophisticated, real-time remedies for efficacious prevention. To illustrate this concept, we shall delve into a hypothetical scenario involving TravelABC, a fictitious travel e-commerce corporation.
How Does Payment Fraud Happen?
Payment fraud occurs when unauthorized or deceptive transactions are executed to obtain financial benefits. Fraudsters utilize a multitude of intricate methods to surpass security protocols and create an illusion of legitimacy for their transactions. Now, let us delve into a comprehensive analysis of the various types of payment fraud and their typical modus operandi.
A group of highly skilled cybercriminals successfully infiltrated a database containing a plethora of compromised credit card data. Their strategic focus turned towards TravelABC, as they astutely observed that the company predominantly depends on rudimentary fraud detection measures, such as IP address and email domain verification.
Identity Mimicking: The hackers use a Virtual Private Network (VPN) to effectively replicate the IP addresses originating from the customary locations where the pilfered credit cards are typically utilized.
Device Fingerprinting Evasion: The hackers employ emulators to replicate the devices typically linked to the cardholders, to deceive and gain unauthorized access.
Transaction Camouflaging: In order to minimize the risk of immediate detection, they initiate their activities by making inconspicuous transactions such as arranging airport transfers or reserving accommodations at budget hotels.
Account Takeover: Instances have been observed where cyber attackers go to the extent of seizing control of pre-existing client accounts, exploiting the stored credit card details to carry out substantial reservations.
Shifting Fraud Landscape
The landscape of payment fraud is experiencing unprecedented growth and advancement, transforming into an intricate and sophisticated challenge. The digitization of banking and payment services, although providing convenience to customers, has introduced a paradoxical situation. It has unveiled an array of vulnerabilities that are eagerly exploited by fraudsters, thereby presenting a significant dilemma.
The rapidity with which transactions are presently processed can be viewed as both advantageous and disadvantageous. While it undoubtedly improves the overall customer experience, it also limits the opportunity for comprehensive scrutiny, consequently creating a more favorable environment for fraudsters to exploit.
The mentioned types of fraud, namely Account Takeover, Synthetic Identity, and Business Email Compromise, exhibit not only a wide range but also a sophisticated nature.
McKinsey paints a vivid picture of the escalating challenges in combating payment fraud. Here’s a breakdown of the key points:
Rising Scale and Complexity: The article starts by highlighting the alarming increase in fraud, with losses to banks. The digital shift has opened up new vulnerabilities, making it easier for fraudsters to exploit the system.
Quick Transactions, Less Time for Checks: The speed of digital transactions leaves banks with little time to identify and counteract fraudulent activities, making the situation even more precarious.
Sophistication of Fraud: Fraudsters are becoming more sophisticated, sharing stolen data and techniques on the dark web, making it increasingly difficult for financial institutions to keep up.
Fragmented Resources: Despite having well-funded anti-fraud groups, resources within organizations are often scattered across different departments like cyber, compliance, legal, IT, and fraud teams, leading to poor coordination.
Types of Payment Fraud
Payment fraud types are complex problems that continuously evolve. Each type provides valuable insights into various aspects of payment fraud, spanning from detection to prevention.
Account Takeover (ATO)
Fraudsters gain unauthorized access to existing customer accounts, either for a one-time funds transfer or ongoing exploitation.
Synthetic Identity
A new identity is created by combining fragments of stolen or fake information to apply for financial products.
Business Email Compromise
Social engineering tactics are used to trick employees into transferring funds to a fraudster’s account.
Identity Theft
Identity theft is a complex criminal act in which an individual unlawfully obtains and exploits another person’s personal information, including Social Security numbers and financial account particulars, with the intention of engaging in fraudulent financial activities or other deceitful practices.
Example: A hacker successfully gains access to John’s personal information, including his Social Security number and date of birth. With this obtained data in hand, the hacker proceeds to illicitly establish a credit card account in John’s name, subsequently engaging in multiple transactions of considerable value.
Carding
Carding encompasses the extensive examination of pilfered or created credit card data on online platforms to authenticate the accuracy of the card particulars. Following successful verification, these cards are used for unauthorized transactions or sold on the dark web.
Example: A fraudulent individual utilizes sophisticated software to input numerous credit card numbers on an e-commerce platform until a legitimate one is identified. Subsequently, a nominal purchase is made to verify its authenticity.
Chargeback Fraud
Chargeback fraud, also referred to as “friendly fraud,” is a deceitful act committed by consumers who intentionally reverse a transaction after receiving the acquired goods or services. By falsely alleging that the transaction was unauthorized or that the goods were not delivered, the consumer aims to deceive and gain an undue advantage.
Example: Sarah purchases a high-end camera through an online platform, promptly receives the product, and subsequently initiates a chargeback with her credit card provider, deceitfully asserting non-receipt of the merchandise.
Account Takeover (ATO)
Account Takeover occurs when a fraudster illicitly attains unauthorized entry into another person’s online accounts, such as email or banking platforms. This nefarious action enables the perpetrator to execute unapproved transactions while frequently altering the account’s email address and password, effectively restricting the original owner from accessing their rightful account.
Example: Unauthorized access was obtained to Emily’s online banking account by a malicious individual, who proceeded to modify the associated contact email and subsequently conducted a transfer of funds to an offshore account.
Synthetic Identity Fraud
Synthetic Identity Fraud pertains to the act of fabricating a novel and fictional identity by amalgamating genuine and counterfeit personal information. Subsequently, the perpetrator utilizes this synthetic identity to initiate the establishment of fresh financial accounts, frequently resulting in an accumulation of indebtedness.
Example: A fraudster combines a real Social Security number with a fake name and address to open a new credit card account, which they max out and never pay off.
Business Email Compromise
Business email compromise (BEC) fraud encompasses the unauthorized access or manipulation of a business email account, to deceive the targeted company, its employees, or its partners into transferring funds or confidential information to accounts exclusively controlled by the perpetrators.
Example: An employee receives an email that appears to be from the CEO, asking for an urgent wire transfer. The employee complies, only to find out it was a scam.
Card-Not-Present (CNP) Fraud
Card-Not-Present (CNP) Fraud is a type of fraudulent activity wherein an individual uses unlawfully obtained credit card details to carry out transactions that do not necessitate the presence of the physical card. These transactions commonly take place online or via telephone, where the card is not physically presented.
Example: A scammer uses stolen credit card information to purchase airline tickets online, where the physical card isn’t needed.
Account Enrollment Fraud
Account Enrollment Fraud is a deceptive practice that entails the utilization of pilfered or fabricated identity information to initiate fresh accounts, for instance, bank accounts, utility services, or phone contracts, to exploit these accounts for financial benefits.
Example: Using stolen identity documents, a fraudster opens a new mobile phone contract and racks up a large bill in international calls.
Phishing
Phishing is a deceptive practice used by cybercriminals to deceitfully extract confidential data, such as passwords and credit card details, from unsuspecting individuals.
These malicious actors masquerade as reputable entities, typically through fraudulent websites or email communications, to manipulate victims into divulging their sensitive information.
A user receives an email that appears to be from their bank, asking them to “confirm” their account details. The link leads to a fake website where the information is captured and later used for fraud.
Skimming
Skimming means the illicit acquisition of credit or debit card data whilst conducting a bona fide transaction utilizing a diminutive contraption called a skimmer. These skimmers are frequently positioned on automated teller machines (ATMs) or fuel dispensers at gas stations.
Example: A skimming device is placed on an ATM. When Tom uses the ATM, his card information is captured, and unauthorized transactions are later made using his account.
The Difference Between Payment Fraud and Friendly Fraud
Payment Fraud and Friendly Fraud are two distinct types of fraudulent transactions, despite both involving unauthorized or deceitful activities. Payment Fraud is an extensive category encompassing a variety of fraudulent schemes that consist of unauthorized transactions. Friendly fraud, on the other hand, refers to a distinct form of payment fraud committed by a genuine customer. The key differences Between Payment Fraud and Friendly Fraud have been depicted as follows:
- Perpetrator: Payment fraud typically involves a perpetrator who is often an external party seeking to deceive. Conversely, friendly fraud entails the customers themselves perpetrating the fraudulent activity.
- Intent: Payment fraud is a deliberate act carried out to deceive. Occasionally, there may be instances of friendly fraud resulting from misinterpretation, for instance, when a family member unknowingly purchases without the cardholder’s knowledge.
- Merchant Relationship: Friendly Fraud refers to a regrettable breach within the merchant-customer relationship, where the customer, in essence, manipulates the merchant. In contrast, Payment Fraud does not entail such intricate relationship dynamics.
- Resolution: Friendly fraud can often be resolved through effective communication between the customer and the merchant, fostering a mutually beneficial resolution. Conversely, payment fraud typically necessitates the involvement of legal channels and may lead to the imposition of criminal charges.
3 Pillars of Payment Fraud
In today’s dynamic realm of payment fraud, enterprises are bolstering their defensive strategies through a comprehensive three-pronged approach. This includes the implementation of a sophisticated Rules Engine, the utilization of Machine Learning algorithms, and the application of Link Analysis techniques using Graph Networks.
A refined rules engine
While machine learning provides a robust and dynamic method for detecting fraud, rules offer a level of immediacy and specificity that machine learning models can’t always provide. They allow for quick interventions, can be set to counteract emerging threats, and can be fine-tuned to allow for business changes and good customers. However, the power of rule-setting comes with the responsibility to use it wisely, necessitating safeguards like impact tests and expert oversight.
Source: The Federal Reserve
Let’s dive deeper into the nuanced role that a “Refined Rules Engine” plays in the modern landscape of fraud prevention.
The Continuing Relevance of Rules in a Machine Learning World
While machine learning has been a game-changer in identifying complex fraud patterns, it’s not the end-all-be-all solution. Rules still serve as a vital tool in a fraud analyst’s arsenal for several reasons:
Quick Response to Ongoing Attacks
Rules can be implemented in real time to halt a fraud attack as it’s happening. This is particularly useful when the attack can be traced to a specific location or characteristic.
Example: Imagine a scenario where a series of fraudulent transactions are all coming from a particular IP address in a specific city. A rule can be immediately set to block all transactions originating from that IP address, effectively stopping the attack in its tracks.
Proactively Blocking Emerging Fraud Trends
Machine learning models often rely on historical data, which may not be up-to-date with the very latest fraud schemes. Rules can be set to counteract new types of fraud that haven’t yet been incorporated into the machine learning model.
Example: If there’s a new phishing technique that fraudsters are using to gain access to accounts, but this technique hasn’t yet resulted in chargebacks and thus isn’t in the historical data, a rule can be set to flag or block transactions that show signs of this new phishing method.
Allowing Good Customers and Adapting to Business Changes
Rules aren’t just about blocking or flagging; they can also be set to allow certain types of transactions. This is particularly useful when a business changes, like acquiring a new brand or launching a new kind of transaction, that the machine learning model needs to be trained on.
Example: A retail business acquires a luxury brand. The average transaction value for this new brand is significantly higher than the existing brands. A rule can be set to allow these higher-value transactions without flagging them as potential fraud, giving the machine learning model time to adapt.
Safeguards and the Responsibility that Comes with Rule-Making
The power to set rules comes with the responsibility to ensure they don’t have unintended negative consequences. Here’s how that’s managed:
- Impact Tests: Before a rule is set live, its potential impact is assessed using historical data. If the rule would affect a significant percentage of transactions, it requires additional oversight and approval.
- Test Rules: This feature allows analysts to “dry run” a rule to see its potential impact without actually setting it live. This is a crucial step in fine-tuning rules to ensure they’re both effective and safe.
- Expert Oversight: Specialized investigation teams are on hand to assist in setting rules, particularly when a rule could have a broad impact. These teams have the experience to know which combinations of conditions are most effective and least likely to result in false positives or negatives.
Machine Learning
Instead of binary yes/no decisions that traditional rule-based systems offer, Machine Learning uses sophisticated algorithms to evaluate the risk level of each transaction, categorizing them as low, medium, or high risk. This nuanced approach allows for more targeted and effective fraud prevention measures.
Unlike rule-based engines that require manual input for each rule, machine learning models are proactive and operate in real time. They continuously learn from both historical data and new incoming information to make accurate risk assessments. This makes machine learning particularly agile and responsive to emerging fraud trends.
Further, the automation and scalability of machine learning are also noteworthy.
Imagine having a team of analysts running hundreds of thousands of queries to evaluate each transaction; machine learning accomplishes this Herculean task in mere milliseconds and with little to no human intervention. This makes it incredibly efficient at handling the high volume of transactions that occur every second in today’s digital payment landscape.
Link Analysis Using Graph Databases
Imagine a detective’s workspace, where photos of suspects, dates, and locations are pinned on a board. Connecting these pieces of evidence are strings, forming a web that helps the detective piece together the story and identify culprits. This visual representation, which helps in understanding relationships and patterns, is akin to what link analysis does in the digital realm.
A graph network operates on a similar principle. It’s a digital tool that maps out and examines the intricate connections across all customer data.
By analyzing these connections, it’s possible to discern patterns and behaviors typical of fraudsters. This “big picture” view enables businesses to identify and stop potential fraudulent activities proactively.
But the beauty of modern fraud prevention is that it doesn’t rely on just one method. Machine learning models, which autonomously analyze and score transactions based on risk, can work hand-in-hand with graph networks. For instance, a machine learning model can be trained to spot unusually large networks or networks that expand rapidly.
How to Detect & Prevent Payment Fraud
To efficiently identify and mitigate payment fraud, businesses are progressively adopting specialized technologies that extensively analyze transactional particulars and customer behaviors. Here’s a look at some of these methods:
Device Fingerprinting
Device Fingerprinting is a sophisticated method that captures and meticulously analyzes the distinctive amalgamation of software and hardware configurations found on a customer’s device. Through this meticulous process, it becomes possible to discern any suspicious or recurring patterns that may serve as indicators of potential fraudulent activity.
BIN Lookup
A Bank Identification Number (BIN) is the primary numerical sequence located on a credit card. Employing a BIN lookup aids in confirming the legitimacy and accuracy of a card by cross-referencing its particulars with a comprehensive database encompassing recognized bank numbers.
IP Lookup
Examining the IP address from which a transaction originates enables businesses to acquire valuable insights regarding the user’s geographical location and the type of connection they are utilizing. This information plays a crucial role in identifying transactions originating from high-risk locations or those that deviate from the user’s typical behavior patterns.
Reverse Email and Phone Lookup
The Reverse Email and Phone Lookup method entails the collection of supplementary data about a user’s email address or phone number. This approach enables the acquisition of valuable insights regarding the user’s credibility, particularly in cases where the email or phone number has been linked to dubious activities previously.
How to Choose a Payment Fraud Prevention Solution
Here’s how to choose a Payment Fraud Prevention Solution, focusing on key elements:
On-site Monitoring with External Data Enrichment: This is a hybrid approach where you have in-house monitoring, but you also use external tools to enhance your data.
Outsourced End-to-End Solution: Here, you rely entirely on an external provider for fraud prevention.
External Solution with Third-Party Data Enrichment: This combines an external end-to-end solution with additional data enrichment from another provider.
Also suggested is to look for solutions that offer modular features, allowing you to turn specific functionalities on or off. This helps in controlling costs and data processing.
API Integration
APIs are crucial for real-time protection and seamless updates. They allow you to integrate the fraud prevention system into your existing infrastructure easily. The benefits include real-time protection, scalability, and customization, all while the vendor manages the technical aspects.
Whitebox Systems
Opt for a transparent system—known as a whitebox system. This allows your team to understand the logic behind the risk scores and rules, offering more control and insight. It’s essential for effective communication within the company and with customers.
Dynamic Friction
Striking a balance between user experience and security is vital. Dynamic friction allows you to perform most security checks in the background, triggering additional verification only for high-risk transactions. This minimizes user friction while maintaining security.
Productivity Enhancements
Your chosen solution should not only integrate well with your existing systems but also enhance your team’s decision-making abilities. It should present information clearly and highlight what’s important.
Pricing Model
The pricing model can significantly impact your risk management strategy. Some vendors offer a chargeback guarantee, which can be reassuring but may also make the vendor overly conservative. Alternatively, a pay-per-API-call model provides more control and scalability.
Frequently Asked Questions
How long does fraud detection take?
With modern technologies, many fraud detection systems operate in real-time or near-real-time. This means potentially fraudulent transactions can be flagged within milliseconds. However, the duration for a comprehensive review or investigation can vary based on the complexity of the case.
What is faster payment fraud?
Faster payment fraud refers to fraudulent activities that exploit real-time or faster payment systems. As transactions in these systems are processed almost instantly, it provides limited time for checks, making it a target for fraudsters.
What is payment hijacking?
Payment hijacking, also known as man-in-the-middle attacks, occurs when a fraudster intercepts or alters communication between two parties during a transaction. This allows the fraudster to redirect payments to their own accounts or steal sensitive payment information.
What type of fraud is most difficult to detect?
Sophisticated frauds that use a combination of techniques, such as synthetic identity fraud (where fraudsters create new, fake identities using a mix of real and fabricated information), are among the most challenging to detect. These frauds often don’t show immediate signs of malicious activity, making them harder to identify using traditional methods.