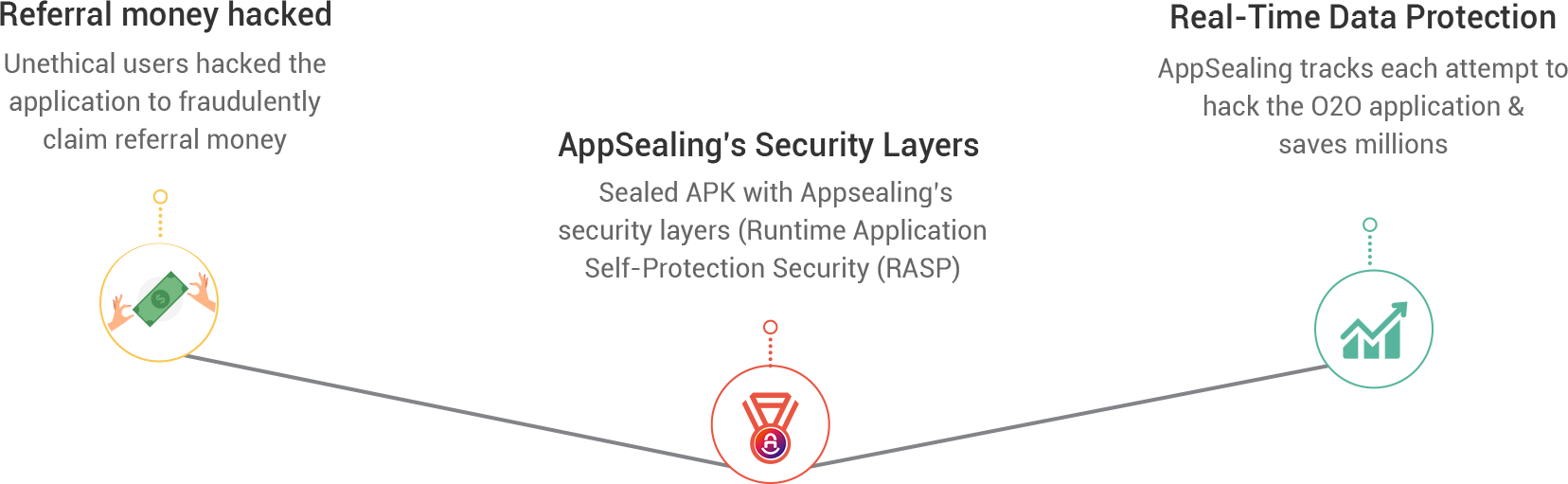
Stop referral money hacks
Due to the nature of Online-to-Offline apps, they often deal with user’s sensitive personal information which is often managed within the application. Due to such high stores of data being stored, hackers exploit the application features by posing as new users using emulators and, thus, claim the referral money. Hackers usually cheat Android IDs of users’ devices using the access offered. Such activities expose O2O apps to problems such as:
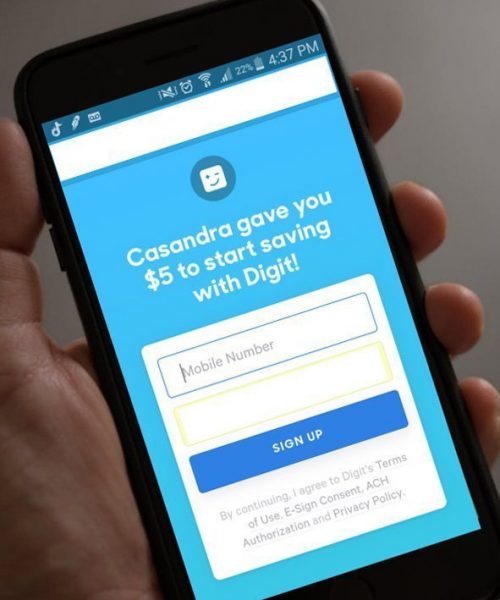
Innovative Solutions for the Online To Offline Industry

Runtime App Self-Protection
O2O applications are the top target for cybercriminals. The timeline pressure to go live leads to the lack of attention given by App Developers towards Application Security. Runtime App Self Protection technology limits its execution in untrusted environments and blocks attempts to access malevolently without proper authorization.
With AppSealing’s RASP feature, App developers have the freedom to meet the time to market:
Results
AppSealing’s secure and robust service stops end users from using their app in an untrusted environment, where rooted devices and emulators pretend as new users and steal referral cash. AppSealing has consistently proved to be an effective, efficient, and economic antidote to the app security ills of various clients, thus helping save millions in referral cash. Apart from ensuring a strong user experience, AppSealing’s O2O app security solutions also preserve the brand image and value.