Mobile app fraud has become a pressing concern today, as our reliance on digital transactions continues to grow. This issue poses significant risks such as financial loss, identity theft, and reputational damage, affecting all participants within the financial ecosystem. At Appsealing, we bear witness to the silent and ongoing battles fought in the digital realm, where the stakes are elevated, and the consequences are far-reaching in nature.
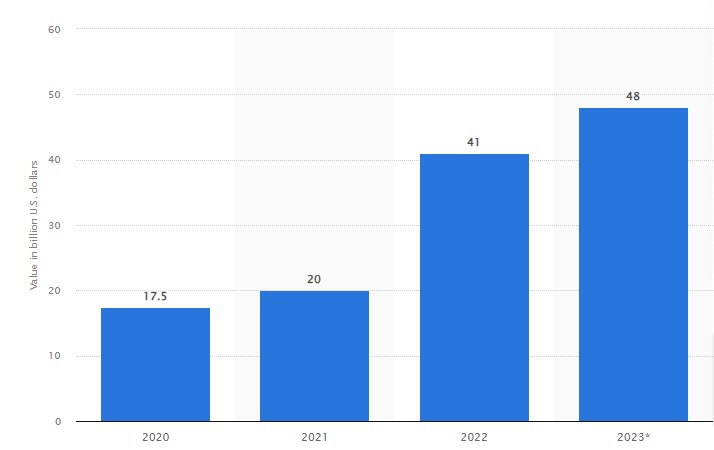
Recent reports and statistics highlight the pressing need to tackle the escalating crisis of mobile app fraud. A study surge in mobile app fraud over the past year, resulting in significant revenue losses amounting to 41 billions for businesses globally. Additionally, another report covering the UK concerned 37.8% of instances of APP fraud related to products. Furthermore, this report states that APP fraud volumes are expected to double by 2026, with significant increases in the UK, India, and the US.
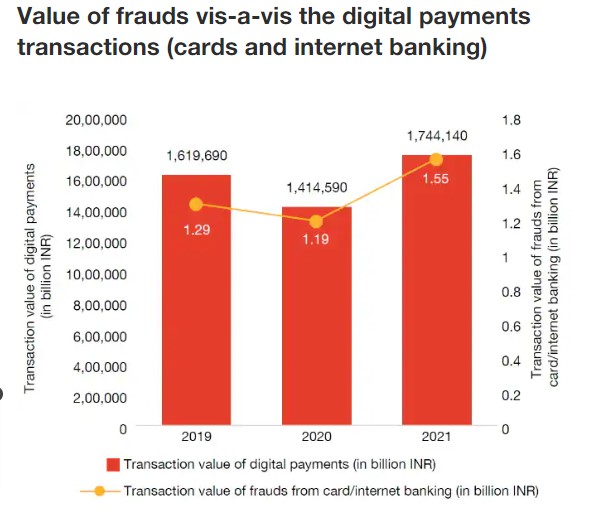
In the context of India, a prominent leader in the realm of digital payments, faces a formidable challenge in combating the escalating losses attributed to Authorized Push Payment (APP) fraud. These losses are projected to surge from $330 million in 2021 to a staggering $612 million by the year 2026.
The increase in fraudulent activities not only hurts financial performance but also undermines consumer trust, as individuals are left to deal with the consequences of identity theft and data breaches. In the complex realm of digital transactions, the key to maintaining integrity and security lies in effective detection and prevention measures.
Therefore, it is crucial to gain a comprehensive understanding of the intricate nature of mobile app fraud as we navigate through the intricate landscape of digital transactions.
In the following discourse, we aim to demystify the concept of mobile app fraud. Through a comprehensive analysis, we will examine its diverse types, delve into its malevolent consequences, and equip you with the requisite expertise to maneuver through the perilous landscape of the digital market with assurance and safety.
What is mobile app fraud?
Mobile app fraud comprises deceitful tactics that aim to exploit legitimate apps, deceive users, and illicitly generate revenue within the mobile app ecosystem. These fraudulent activities specifically target a range of stakeholders, including users who download apps from the App Store or Play Market, as well as developers of genuine applications. The perpetrators frequently utilize fraudulent apps that closely resemble legitimate ones, leading users to unknowingly download them for malicious intents.
The proliferation of fraudulent mobile applications has led to a multitude of illicit activities, such as unauthorized transactions, data breaches, and the dissemination of malicious software. These deceitful apps not only inflict harm upon unsuspecting users but also damage the standing of legitimate applications, resulting in financial losses for both developers and advertisers. In light of the existence of fraudulent apps within reputable marketplaces like the App Store or Play Market, it is imperative for all parties involved to adopt a proactive and vigilant approach to ensure the integrity and security of the mobile app ecosystem.
How is Mobile app fraud or malicious mobile activity detected?
The implementation of a comprehensive and sophisticated detection system that combines automated tools and expert human analysis enables stakeholders in the mobile ecosystem to enhance their defense against fraud and malicious activities. It is crucial to acknowledge that the landscape of mobile app fraud is constantly changing, which underscores the importance of continuous vigilance and the ability to adapt to emerging threats.
Device fingerprinting:
Device fingerprinting is a technique that entails gathering comprehensive data regarding the user’s device, including but not limited to the operating system version, device type, and IP address. This valuable information can subsequently be utilized to detect and prevent fraudulent activities, such as instances in which a solitary device is employed to generate numerous accounts or when a device operates from a location divergent from the user’s account address.
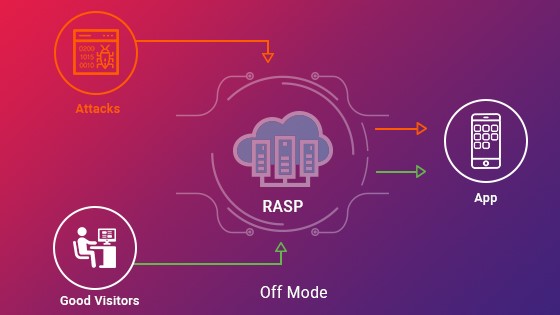
Runtime Application Self-Protection (RASP) security is a crucial technology that enhances the security posture of mobile applications by actively detecting and responding to threats in real-time, during the application’s execution or runtime.
Below is an overview of how RASP security works to protect customers and mobile apps from various threats, including tampering, illegal modifications, and unknown threats:
Real-time Monitoring for Traffic Analysis:
Recognizing non-human traffic, rapid surges, or unusual patterns that are typically associated with bots or automated processes.
Active Threat Monitoring:
- Real-Time Protection: Appsealing RASP actively monitors the app’s behavior and user interactions during runtime. It can instantaneously identify and mitigate known and unknown threats.
- Internal Monitoring: Unlike perimeter defenses, RASP works from within the app, offering more detailed insight into the application’s runtime behavior and data flow.
Behavior Analysis:
- User Behavior: Analyzing patterns of user interaction with apps to identify anomalies indicative of fraud.
- Device Behavior: Monitoring device characteristics and behaviors that deviate from the norm, suggesting potential malicious activity.
Traffic Analysis:
Recognizing non-human traffic, rapid surges, or unusual patterns that are typically associated with bots or automated processes.
Machine Learning and AI:
Implementing algorithms capable of learning and adapting to new threats, improving detection rates over time.
Especially useful in identifying sophisticated or evolving forms of fraud.
VAPT
The implementation of Vulnerability Assessment and Penetration Testing (VAPT) plays a vital role in guaranteeing the security of mobile applications. By actively detecting and resolving vulnerabilities, the methodology for VAPT in mobile apps safeguards sensitive data, upholds user trust, and ensures compliance with cybersecurity and data protection regulations. Employing a methodical and well-organized approach, VAPT conducts a comprehensive evaluation of an application’s security status, furnishing valuable insights for enhancing security measures and bolstering defenses against potential cyber threats.
1. Planning & Preparation:
The initial phase of the Vulnerability Assessment and Penetration Testing (VAPT) process is known as Planning and Preparation. This phase serves as the cornerstone for a successful security assessment. Here’s a brief breakdown.
- Scope Definition: Determine the scope of testing, including the systems to be assessed and testing methods to be used.
- Information Gathering: Collect information about the application, infrastructure, and underlying technologies.
2. Vulnerability Assessment (VA):
The VA process systematically identifies, analyzes, and reports on the vulnerabilities present in an application, system, or network.
- Automated Scanning: Use automated tools to scan the mobile application for known vulnerabilities.
- Source Code Review: Conduct a manual review of the application’s source code to identify potential security risks.
- Risk Assessment: Evaluate and prioritize identified vulnerabilities based on their potential impact and exploitation likelihood.
3. Penetration Testing (PT):
PT is an authorized simulated cyberattack against a system, application, or network to evaluate its security.
- Pre-Exploitation Analysis: Plan the penetration testing process, choosing the appropriate tools and methodologies.
- Exploitation: Actively attempt to exploit identified vulnerabilities to assess their practical impact and severity.
- Post-Exploitation Analysis: Understand the depth and breadth of an exploited vulnerability, evaluating the potential damage and access granted through the exploit.
4. Reporting:
The reporting phase encompasses the documentation and communication of findings derived from the Vulnerability Assessment (VA) and Penetration Testing (PT) to the pertinent stakeholders. A paramount objective of this stage is to generate a report that serves as a meticulous record of the assessment’s methodology, findings, risk levels, and recommended remedial actions.
- Documentation: Prepare a comprehensive report detailing found vulnerabilities, exploitation results, data accessed, and the potential impact of exploitation.
- Recommendations: Provide specific, actionable recommendations for addressing and mitigating each identified vulnerability.
5. Remediation:
Remediation entails the meticulous resolution or alleviation of the vulnerabilities that have been distinguished during the assessment.
- Patch & Fix: Developers should promptly address and fix the identified vulnerabilities, applying patches or reconfiguring security settings as necessary.
- Retesting: Conduct follow-up assessments to verify that the fixes are correctly implemented and effective in preventing the vulnerabilities.
6. Knowledge Sharing & Review:
The Knowledge Sharing and Review phase encompasses the vital task of disseminating valuable insights, lessons learned, and best practices acquired throughout the Vulnerability Assessment and Penetration Testing (VAPT) process. This phase involves the dissemination of knowledge to the wider team or organization, ensuring that the information is shared effectively and efficiently.
By sharing this valuable expertise, the team can enhance their understanding and collectively benefit from the experience gained during the VAPT process.
- Share insights and findings with relevant stakeholders and team members.
- Conduct a review of the testing process to identify areas for improvement and adjustment in future assessments.
In-App Security
Mobile In-App Security encompasses the comprehensive array of measures and practices incorporated within a mobile application to fortify it against an array of security threats and vulnerabilities.
This sophisticated security framework is meticulously developed to safeguard the sensitive data that is either transmitted through or stored within the application, guarantee the utmost integrity and confidentiality of user information, and deter unauthorized access or any form of malicious activity.
Below are the key components of In-App Security:
Ensuring the security of mobile applications is of utmost importance in safeguarding both users and their associated data. By incorporating stringent security protocols within the application, developers can establish a secure and reliable environment for users. This ensures the protection of sensitive data and transactions, shielding them from a wide range of potential cyber threats and vulnerabilities.
These security practices should be integral to the app development process, from the initial design phase to continuous monitoring and improvement after the app’s deployment.
1. Data Encryption:
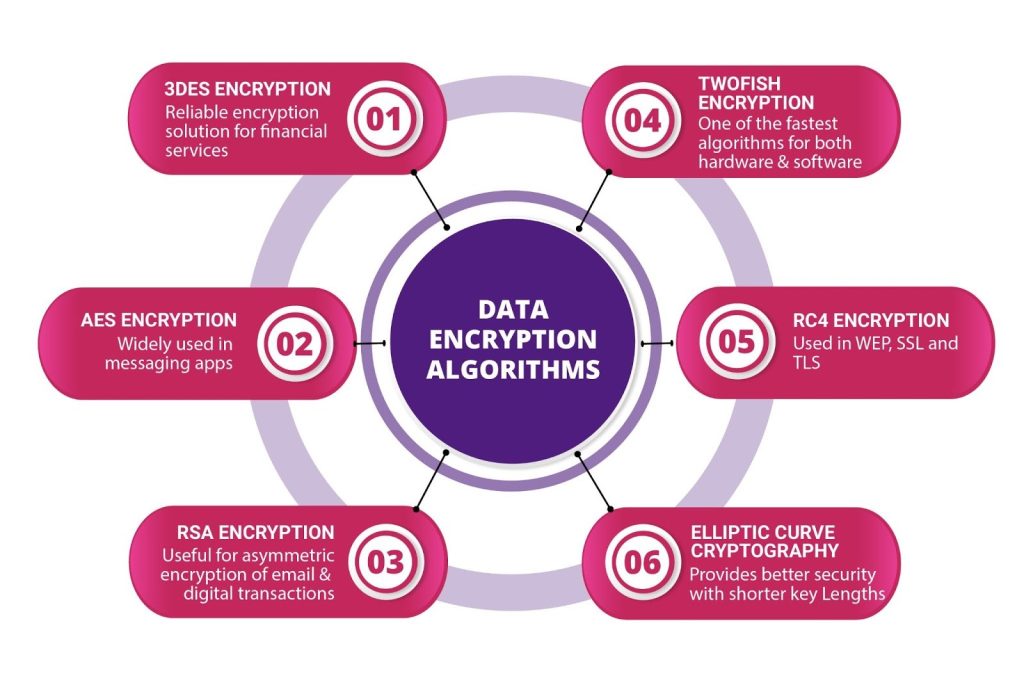
Data encryption is an essential element of In-App Security, guaranteeing the safeguarding of transmitted and stored data within the application against unauthorized access and breaches. Through the process of encryption, readable data is transformed into a coded format, rendering it incomprehensible to malicious individuals without the appropriate decryption key.
- It ensures that data transmitted between the app and servers is encrypted using robust algorithms like AES (Advanced Encryption Standard), safeguarding it from being intercepted or accessed by unauthorized entities.
- It stores data within the app or on the device and should also be encrypted to protect it if the device is lost or compromised.
2. Authentication & Authorization:
Authentication is the process that diligently verifies the identity of users, employing various methods such as credentials, biometrics, or even multi-factor authentication. In contrast, authorization serves as a crucial procedure that bestows or withholds access permissions to distinct resources and functions within the application, solely contingent upon the authenticated user’s profile. In other words,
- Authentication: Verifies the identity of users accessing the app, often through credentials, biometrics, or multi-factor authentication mechanisms.
- Authorization: Controls user access to various app features and data, granting permissions based on predefined roles or access levels.
3. Code Obfuscation & Integrity Checks:
Code obfuscation is the process of transforming the source code of an application into a highly convoluted and intricate format, rendering it arduous to decipher and comprehend. This technique serves to heighten the complexity of reverse engineering endeavors, thereby bolstering the overall security of the application.
Additionally, integrity checks play a crucial role in guaranteeing the sanctity of the app’s code, thereby fortifying it against any potentially malicious alterations. In other words,
- Code Obfuscation: Makes the application’s source code more difficult to read and understand, hindering reverse engineering attempts by malicious actors.
- Integrity Checks: Validates that the application’s code has not been tampered with or modified, protecting against code injection or alteration attacks.
4. Secure Communication:
Secure communication ensures all data exchanges between the app and servers occur securely. By utilizing secure communication protocols like HTTPS (SSL/TLS), data transmitted is encrypted, providing confidentiality and integrity during transit, and protecting against potential interceptors and eavesdroppers. Implements secure communication protocols like HTTPS (SSL/TLS) to encrypt data transmitted between the app and servers, protecting against man-in-the-middle attacks.
5. Input Validation:
Input validation is an essential security measure implemented to thwart the infiltration of malevolent data into the application. Through the meticulous process of validating, sanitizing, and filtering user inputs, the application can effectively safeguard itself against a plethora of injection attacks, thereby upholding the integrity and security of the data.
It ensures that the app properly validates and sanitizes user inputs to prevent injection attacks, such as SQL injection or cross-site scripting (XSS).
6. Runtime Protection:
Runtime application security protection involves monitoring and securing the application while it’s actively running. This component safeguards against dynamic threats like code injections and function manipulations, offering real-time defense against exploits that attempt to compromise the app during operation.
Employs security measures to protect the application during its runtime, preventing exploits like code injection, tampering, or analysis from being conducted on running applications.
7. API Security:
API security is of utmost importance for applications that engage with external services and data. It entails the implementation of resilient security controls and measures on the Application Programming Interfaces (APIs) to mitigate the risks of unauthorized access, data breaches, and other potential security vulnerabilities related to data transmission.
It ensures the safeguarding of the APIs that the application interacts with by employing effective strategies such as API key management, token-based authentication, and request rate limitation.
8. Regular Updates & Patch Management:
Regularly updating and managing patches for software is of utmost importance in ensuring the security of an application. This process entails the identification, acquisition, installation, and verification of patches, effectively safeguarding against known vulnerabilities while bolstering the overall security posture of the app.
Consistently updating the application serves to address known vulnerabilities, enhance security functionalities, and fortify defenses against emerging threats.
9. Security Testing & Auditing:
Security Testing and Auditing play a vital role in detecting and resolving potential vulnerabilities present in the application. By adopting a proactive approach, we consistently conduct a range of security tests, reviews, and audits to evaluate and enhance the application’s security. The objective is to ensure that the application meets the highest industry standards and complies with all applicable requirements.
This approach includes regular assessments such as Vulnerability Assessment and Penetration Testing (VAPT) to effectively identify and mitigate any potential security risks within the application.
10. User Privacy Protection:
User Privacy Protection is a paramount priority, focused on safeguarding the personal information of our esteemed users. The commitment to this endeavor encompasses the utilization of advanced privacy-preserving techniques, strict adherence to relevant data protection laws, and the establishment of transparent and ethically sound data collection and processing practices within our application.
It implements a range of measures to fortify user privacy, including robust data anonymization protocols, minimal data collection practices, and utmost compliance with privacy regulations and industry standards.
What are the different types of mobile app fraud?
Mobile app fraud encompasses a wide range of deceptive practices and malicious activities that specifically target users, developers, and the larger app ecosystem. With the increasing prevalence of smartphones and the widespread dependence on mobile applications, numerous fraud types have emerged, each characterized by its distinct strategies, objectives, and consequences.
Location Spoofing:
Location spoofing is a devious act that involves the intentional manipulation of a user’s geographical location data, resulting in the dissemination of inaccurate information about the user’s real location.
How it Works: Hackers utilize specialized applications or tools designed for GPS spoofing to manipulate the GPS data of a device, deceptively misleading applications that heavily depend on location services.
Mitigation: Mobile app developers can incorporate sophisticated location verification mechanisms, thoroughly analyze users’ location data to detect any unlikely or impossible movements and integrate server-side checks to authenticate the credibility of location changes.
Device Spoofing:
Device spoofing involves the deceptive practice whereby malicious individuals replicate genuine mobile devices by tampering with their distinctive identifiers.
How it Works: Cyber attackers manipulate device attributes, such as the International Mobile Equipment Identity (IMEI) or employ emulators to assume the identity of authentic devices. These tactics are frequently employed to perpetrate advertising fraud or circumvent security measures.
Mitigation: Mobile application developers can incorporate reliable device fingerprinting and validation solutions into their applications. By doing so, they can effectively monitor any suspicious or frequent alterations in device attributes.
App Cloning:
Mobile App Cloning involves the meticulous and almost indistinguishable copy of the original mobile app, intending to mislead unsuspecting individuals or carry out malicious activities.
How it Works: Cyber attackers engage in the act of duplicating authentic mobile application codes, covertly inserting malevolent components, and subsequently releasing the replicated version with the intention of misleading unsuspecting users.
Mitigation: It is highly recommended to educate users on the importance of downloading applications solely from official app stores. Additionally, it is crucial to utilize app attestation services and diligently monitor any unauthorized versions of the application.
SIM Swapping:
SIM Swapping is a fraudulent act where the perpetrator unlawfully transfers the phone number of an individual to a SIM card under their control, consequently seizing the victim’s mobile identity.
How it Works: To carry out SIM swapping, perpetrators employ social engineering strategies or gain assistance from insiders to persuade the mobile service provider to transfer the target’s phone number to a fresh SIM card.
Mitigation: It is highly recommended for users to utilize multi-factor authentication methods that do not solely depend on SMS, while carriers should adopt more robust identity verification procedures.
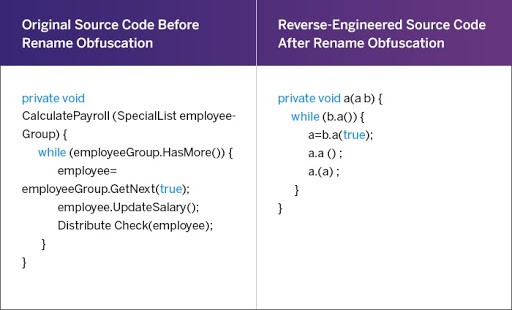
Reverse Engineering:
Reverse Engineering is the process of deconstructing an application to comprehensively analyze its internal mechanisms, intricate structure, and intricate code. This endeavor is frequently undertaken to discern potential vulnerabilities or even develop replicated applications.
How it Works: Hackers employ a range of sophisticated tools to decompile and meticulously scrutinize the source code of an application, comprehending its intricate architecture and potentially uncovering any vulnerabilities in terms of security.
Mitigation: Hackers utilize an array of sophisticated tools to decompile and thoroughly analyze the source code of an application, comprehending its intricate architecture and potentially exposing any security vulnerabilities that may exist.
Repackaging:
Definition: Repackaging entails the modification of a genuine mobile application by cyber criminals, who strategically embed harmful code within it, subsequently disseminating it through unofficial platforms.
How it Works: During the process of Repackaging, a hacker attacker inserts malware or malicious advertisements into the application, subsequently republishing it to specifically target unsuspecting users who seek free alternatives to paid applications.
Mitigation: Mobile app developers should prioritize the adoption of digital signing for applications and encourage the utilization of official app distribution channels. Also, they should implement in-app verification processes to ensure the integrity of the apps.
Overlay Attacks:
Overlay Attacks involve the creation of counterfeit interfaces or screens by malicious applications, which are superimposed on genuine applications to deceive users and illicitly obtain confidential information.
How it Works: Upon installation, the malicious application awaits the activation of target applications. Subsequently, it proceeds to superimpose deceitful interfaces onto them, effectively deceiving unsuspecting users into engaging with the counterfeit overlay.
Mitigation: It is essential for users to consistently update their mobile applications and acquire knowledge regarding the permissions and behaviors of installed apps. Simultaneously, developers can incorporate solutions that can effectively detect overlay attacks.
Rogue Keyboards:
Rogue Keyboards are insidious input methods deliberately crafted to capture and transmit user keystrokes to malevolent entities, thereby compromising any sensitive data inputted via the keyboard.
How it Works: Malicious keyboard applications deceive users into installation, subsequently capturing and transmitting input data to unauthorized individuals/hackers.
Mitigation: Users must exercise caution when installing third-party keyboards. Operating systems must also enforce more stringent controls and permissions for keyboard applications.
Mobile Banking Trojans:
Mobile Banking Trojans are a form of malicious application that cunningly mimics genuine banking apps, with the sole intention of duping users and illicitly obtaining their valuable financial data and login credentials.
How it Works: The Trojan application deceives users by presenting a counterfeit banking app interface, thereby capturing valuable login credentials and other confidential information provided by the user.
Mitigation: Financial institutions and application developers have a vital role in enlightening users about identifying and evading unofficial banking applications. Moreover, it is crucial to incorporate sophisticated authentication mechanisms.
Man-in-the-Middle Attacks:
A man-in-the-middle attack occurs when an unauthorized entity illicitly intercepts and potentially modifies the communication between two parties, such as an application and a server, without their knowledge.
How it Works: Man-in-the-middle attacks involve a discreet interception and potential modification of communication between two parties who are under the assumption that they are engaging in direct communication with one another.
Mitigation: To ensure the utmost integrity and security of data transmission, it is highly recommended to implement the utilization of HTTPS with SSL/TLS encryption, alongside the incorporation of certificate pinning.
Mobile Phishing:
Mobile Phishing entails fraudulent endeavors aimed at deceiving mobile users into disclosing sensitive or confidential information via deceitful messages, emails, or websites.
How it Works: Cybercriminals employ deceptive tactics by dispatching fraudulent messages or emails containing hyperlinks to malicious websites, strategically crafted to extract confidential data from unaware individuals.
Mitigation: It is essential to provide users with thorough training in identifying and evading phishing attempts. Simultaneously, it is imperative to deploy robust security solutions that possess the capability to detect and obstruct malicious links and phishing scams.
How to Protect Mobile Apps From Different Types of Mobile App Frauds?
The field of mobile applications operates within a constantly evolving environment, where the matter of security holds utmost importance owing to the handling of sensitive data by these apps. With the increasing integration of mobile apps into both professional and personal spheres, safeguarding them against malevolent attacks and breaches of data becomes imperative.
Below are the eight best practices for ensuring mobile app security:
Encrypt Source Code:
The source code serves as the fundamental basis for a mobile application. By employing encryption techniques, it renders the code indecipherable to any unauthorized individuals, thus safeguarding it against potential tampering or unauthorized duplication with malicious intentions.
Conduct Penetration Testing:
To ensure the utmost security of your app before launch, it is essential to proactively engage in the identification and resolution of potential security weaknesses through the simulation of cyber-attacks. This meticulous practice, commonly referred to as penetration testing, serves the purpose of revealing any vulnerabilities that could potentially be exploited by malicious individuals aiming to compromise your app’s integrity.
Safeguard Data During Transmission:
Data transmission between the user’s device and your servers is susceptible to vulnerabilities. Employing secure communication protocols such as SSL or VPN is essential in safeguarding this data during transit, thereby preventing unauthorized interception and unauthorized access..
Encrypt Stored Data:
In certain instances, applications may necessitate the storage of sensitive data on a user’s device. Encrypting this data ensures that even if an unauthorized individual were to gain access to the device’s storage, they would be unable to comprehend or utilize the stored information unless equipped with the appropriate decryption key.
Utilize Updated Cryptography Methods:
Cryptography techniques are advancing. Employing the most up-to-date and highly secure approaches to encrypt and decrypt data guarantees the continued efficacy of your security measures, effectively countering state-of-the-art threats.
Implement Strong Authentication:
To ensure secure access, users are required to generate intricate passwords and routinely change them. In the case of applications handling exceptionally confidential data, it is advisable to incorporate supplementary authentication methods such as fingerprint or retina scans.
Secure the App’s Backend:
It is imperative to ensure the utmost security for the servers and databases that your application interacts with. To safeguard against any unauthorized access or potential data breaches, it is essential to incorporate comprehensive security protocols on the backend.
Limit Sensitive Data Storage:
To enhance data security, it is recommended to limit the storage of sensitive data on the user’s device. In cases where it is necessary to store such data, it should be done in a highly secure manner. Additionally, implementing automated functionalities that facilitate the deletion of this data once it becomes unnecessary should be considered.
Conclusion:
Leveraging advanced technologies and strategic approaches, organizations can effectively safeguard against payment fraud, ensuring secure transactions and fostering trust among users in the digital transaction landscape.