iOS App Encryption is a crucial aspect of Apple’s mobile application security infrastructure, designed to safeguard user data from unauthorized access. It comprises several layers of encryption that work together to provide comprehensive protection for sensitive information on iOS devices.
iOS App Encryption
The default protection levels in iOS Data Protection allow you to choose the level of encryption that best suits your needs. From no protection to complete protection, these levels provide varying degrees of mobile application security to protect your sensitive data from unauthorized access, incident or security breach.
iOS App Encryption Default Levels
No protection: This level provides no encryption for the file, meaning that the file is always accessible to anyone who has physical access to the device. This level is not recommended for sensitive data, as it provides no protection against unauthorized access.
Complete until first user authentication (default): This level encrypts the file and makes it inaccessible until the user unlocks the device for the first time after a reboot or shutdown. After the first unlocking, the file remains accessible until the device is shut down or rebooted again. This level provides basic protection against unauthorized access, as it requires the user to unlock the device before accessing the file.
Complete unless open: This level encrypts the file and allows you to open existing files only when the device is unlocked. If you have a file already open, you may continue to access that file even after the user locks the device. You can also create new files and access them while the device is locked or unlocked. This level provides additional protection for sensitive data, as it requires the user to unlock the device to open a file, but still allows you to access files that are already open.
Complete: This level provides the strongest protection for files, as the file is only accessible when the device is unlocked. This level encrypts the file and makes it completely inaccessible until the user unlocks the device. This provides the highest level of protection against unauthorized access, as the file cannot be accessed even if the device is lost or stolen.
Apple Encryption Questions and What do they Mean?
Should I select ‘Yes’ if I am using https to connect to the server?
When submitting an app to the Apple App Store, there is a question about whether the app uses HTTPS to connect to the server. The answer to this question should be “Yes” . HTTPS is a secure protocol that encrypts data sent between the app and the server, providing an additional layer of mobile application security to protect user information from being intercepted or tampered with. Selecting “Yes” confirms that the app is using this secure protocol to connect to the server, and assures users that their information is being protected.
When should I select the ‘No’ option?
There are some cases where an app needs to communicate with a server through an unsecured connection, which is not allowed by default in Apple’s App Transport Security (ATS) feature. In these situations, the developer can permit the insecure connection by manually setting the “Allow Arbitrary Loads” option to “true” in the app’s info.plist file under the “App Transport Security Settings” section.
Choosing “Yes” in the above section, would lead to
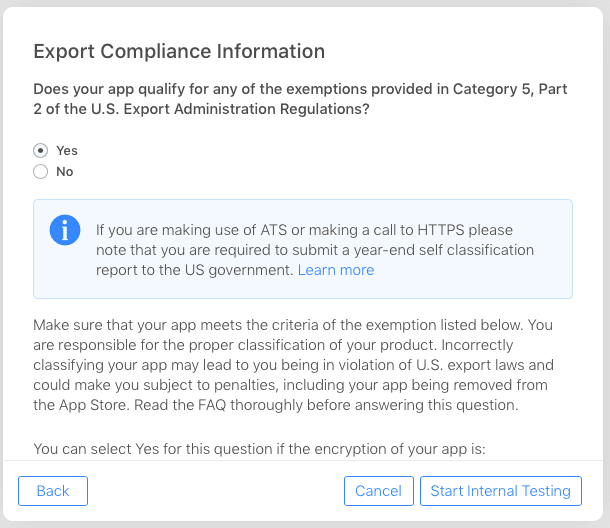
Does your app qualify for any of the exemptions provided in Category 5, Part 2 of the U.S. Export Administration Regulations?
The exemptions listed in the statement indicate certain scenarios where an app’s encryption may be exempt from the regulations. These scenarios include encryption that is specially designed for medical end-use, limited to intellectual property and copyright protection, limited to authentication, digital signature, or the decryption of data or files, specially designed and limited for banking use or “money transactions,” or limited to “fixed” data compression or coding techniques.
If an app’s encryption falls under one of these exemptions, the developer may select “Yes” when answering the question about encryption during the app submission process.
If my app uses Apple Keychain, Will it fall under any of these exceptions?
The Apple app would qualify for the exception under Category (c), which is limited to authentication, digital signature, or decryption of data or files, since it uses Apple Keychain.
If my Apple iOS app uses third party encryption libraries, will it fall under any of these exceptions?
The majority of third-party encryption libraries available for iOS utilize widely recognized encryption and decryption algorithms. Apple has included these standard encryption methods as an exception under Category (c). As a result, if an app is using these common encryption libraries in iOS, the developer may answer “YES” to the question about encryption during the app submission process.
Under which exceptions do my app fall if it doesn’t meet any of these categories?
If the iOS app utilizes a custom encryption algorithm, which is typically created by the app’s developers, the appropriate response to the encryption question during the app submission process is “NO.”
AppSealing and iOS App Encryption
AppSealing provides a robust SDK-based solution to apply comprehensive protection to your iOS apps. You can seamlessly integrate AppSealing’s SDK into your build pipeline without any negative impact.
No impact on App Performance: The implementation of AppSealing in your app does not impact its performance or usability. We guarantee that the extra layer of mobile application security provided by AppSealing does not impact the app’s memory, CPU usage, battery life, or frames per second (FPS).
Essential Security Function: Benefit from advanced mobile application security features such as Jailbreak Detection, Integrity Protection, and Anti-Debugging to enhance the security of your application. These mobile application security features are applied at runtime to ensure comprehensive protection.
Compatible Mobile game engine: AppSealing is designed to work seamlessly with the most widely used game engine, Unity, on mobile platforms. Compatibility with the Unreal engine is currently being developed and will be available soon.
Protection from Jailbreak
AppSealing offers a level of mobile application security that is comparable to a pure environment. It can also prevent apps from launching on jailbroken devices to enhance security measures.
Integrity Protection
AppSealing offers Integrity Protection by utilizing hash validation for app components and modules. This reduces the amount of maintenance required to maintain integrity control within the application over time.
If you’re looking for on-premises infrastructure to secure your mobile apps, you might want to consider a few things before making your final decision.
- First, what kind of mobile application security do you need?
- Do you need to protect against data breaches, malware, or both? Second, how many users do you need to support?
- And finally, what’s your budget?
Once you’ve answered these questions, you’ll be in a better position to choose the right on-premises infrastructure for your needs.
Unlock your Mobile App security Strategy. Try AppSealing today.