The perpetual struggle between device customization and mobile application security remains an ongoing dilemma that poses considerable challenges for both developers and security experts.
At Appsealing, we’ve witnessed the rise and evolution of various rooting solutions, with Magisk standing out as one of the most innovative and popular among them. Magisk provides users with exceptional systemless rooting capabilities, enabling them to customize their devices without making any changes to the system partition. However, this innovative tool also poses distinct security challenges for application developers.
In this blog, we’ll delve deep into the reasons behind this stance, the potential risks of not doing so, and the methods to effectively implement such restrictions.
What is Rooting?
Rooting, in the context of Android devices, refers to the process of obtaining privileged control over the device’s operating system. Android, which is built upon the Linux kernel, has inherent multi-user capabilities. In a standard setup, most users and applications operate without the ability to execute certain privileged commands or access specific system files.
Rooting allows users to overcome these limitations set by hardware manufacturers and achieve administrative (superuser) permissions. With these elevated permissions, users can install a modified version of the operating system, run specialized applications that require deeper system access, and make changes that are otherwise restricted on unrooted devices.
Moreover, Rooting provides access to the “root” user, the most privileged user on Linux systems, thereby allowing modifications and access that are otherwise restricted. Rooting an Android device can provide users with advanced customization options and greater control over their devices. However, it is important to acknowledge that this process also exposes the device to a wide range of security vulnerabilities and potential threats.
For businesses and individuals prioritizing mobile application security, understanding these risks are crucial.
- Malware Vulnerability: According to a report by Kaspersky, rooted devices are more susceptible to malware attacks. Their research indicated that nearly 70% of Android devices infected with malware were rooted.
- SafetyNet Failures: Google’s SafetyNet Attestation API is designed to check device compatibility, safety, and integrity. Devices that are rooted often fail these checks. A study revealed that apps relying on SafetyNet witnessed a 40% increase in fraud rates on devices that bypassed these checks.
- Banking and Financial Risks: A survey conducted by Symantec found that over 30% of mobile banking trojans specifically targeted rooted devices, exploiting the elevated permissions to steal sensitive financial data.
- Unauthorized Data Access: In a research study, it was found that apps on rooted devices had a 50% higher chance of accessing data they weren’t supposed to, compared to those on non-rooted devices.
- Custom ROM Vulnerabilities: A significant portion of users root their devices to install custom ROMs. However, not all custom ROMs are secure. A study indicated that around 20% of devices with custom ROMs had potential security vulnerabilities that weren’t present in official firmware releases.
- Compromised Update Mechanism: Rooted devices often don’t receive official security updates. According to a report, nearly 60% of rooted devices were running outdated Android versions with known security vulnerabilities.
Different Tools used for rooting Android devices
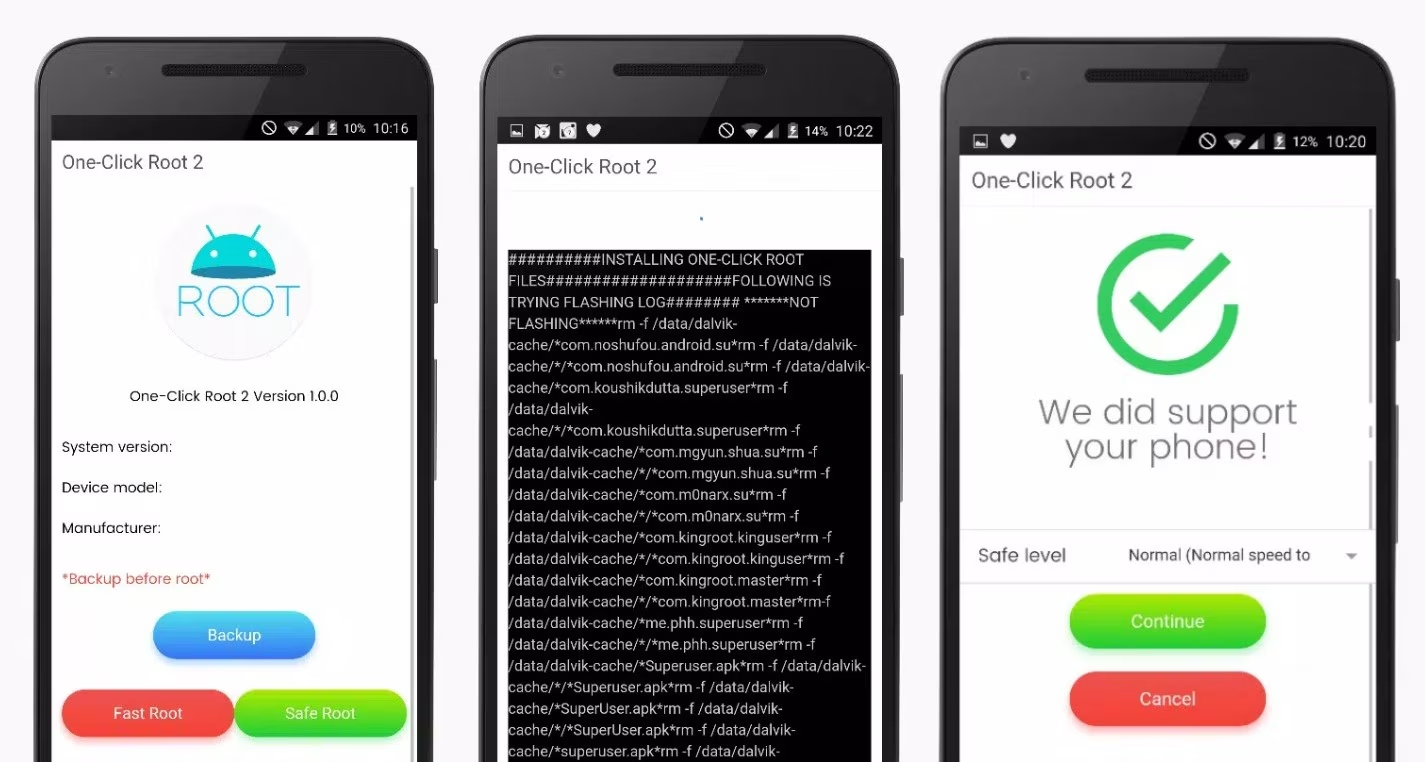
One Click Root
One Click Root APK offers a streamlined approach to rooting, unlocking a plethora of features and customizations. Whether the goal is to eliminate bloatware, introduce a custom ROM, or enhance device performance, this tool provides a straightforward solution. Additionally, for those wary of data loss, Dr.Fone also offers a Data Recovery tool for Android, ensuring data retrieval without the need for root access.
Download One Click Root APK:
- Begin by downloading the One Click Root APK file to your Android device. Ensure you have a stable internet connection to avoid any interruptions during the download process.
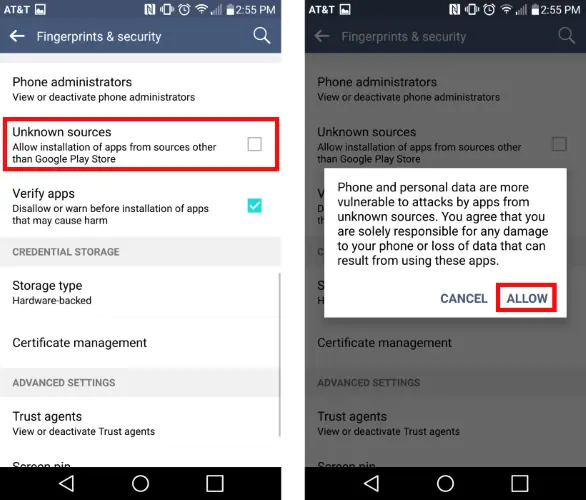
Enable Unknown Sources:
- By default, Android devices are set to block installations from sources outside the Google Play Store for security reasons. To install the One Click Root APK, you’ll need to override this setting.
- Navigate to your device’s settings.
- Find and select the “Security” or “Privacy” option (the exact name might vary based on your device).
- Look for an option labeled “Unknown Sources” and toggle it on. This will allow the installation of apps from sources other than the Play Store.
Install One Click Root APK:
- Once you’ve enabled installations from unknown sources, locate the downloaded APK file on your device.
- This is typically found in the “Downloads” folder or the notification panel.
- Tap on the file to initiate the installation process.
- Follow the on-screen prompts to complete the installation. This usually involves tapping on “Install” and waiting for the process to finish.
Launch One Click Root APK:
- After the installation is complete, find the ‘One Click Root’ app icon on your device’s home screen or app drawer.
- Tap on the icon to open the application. Upon launching, you might see a message prompting you to connect your device to a computer.
Connect Your Device to Your Computer:
- If prompted, connect your Android device to your computer using a USB cable.
- Ensure that “USB debugging” is enabled on your device. This can be done by navigating to “Settings” > “Developer Options” > “USB Debugging” and toggling the switch on. If you don’t see “Developer Options” in your settings, you might need to unlock it by tapping multiple times on the “Build Number” under “About Phone.”
- Root Your Device with One Click Root APK:
With your device connected and the app launched, tap on the “Root” button within the One Click Root APK interface. The application will start the rooting process, which might take a few minutes. Ensure you don’t disconnect the device or interrupt the process.
Completion:
Once the rooting process concludes, you can disconnect your device from the computer.
Your Android device should now be rooted, granting you elevated permissions and access to a wider range of features and customizations.
SuperSU
Rooting your Android device with SuperSU opens a world of possibilities, allowing you to tap into deeper system functionalities and customize your device to your liking. However, it’s crucial to follow the process carefully to ensure a successful rooting.
How to get started?
- Unlock Your Bootloader: Before proceeding, ensure that your device’s bootloader is unlocked.
- Install a Custom Recovery: You need to have a custom recovery like TWRP installed on your device. This will be used to flash the SuperSU file.
- Download SuperSU: Obtain the latest version of the SuperSU flashable ZIP file from a reliable source.
- Transfer SuperSU to Your Device: Place the downloaded SuperSU file in the root directory of your phone’s internal storage. You can do this by connecting your device to a computer via USB or directly downloading it to your device.
- Boot into Recovery Mode: Restart your device and boot into recovery mode using the specific key combination for your device.
- Flash SuperSU: In the TWRP recovery menu, select ‘Install,’ navigate to the location where you placed the SuperSU file, select it, and swipe to confirm the flash.
- Reboot Your Device: Once the flashing process is complete, go back to the main menu of the TWRP recovery and select ‘Reboot.’
- Verify Root Access: After your device has rebooted, check for the SuperSU app in your app drawer. To further verify that the rooting process was successful, download the Root Checker app from the Google Play Store and follow the instructions to check for root access.
- Manage Root Permissions: When running a rooted app for the first time, you will receive a SuperSU prompt asking if you want to grant the app Superuser access. Make sure to grant access to trusted apps only.
- Enjoy Your Rooted Device: You have successfully rooted your Android device with SuperSU and can now enjoy the extended capabilities and customization options that come with root access.
AdWay
AdAway is a popular ad-blocking application designed specifically for rooted Android devices. It aims to enhance the user experience by eliminating various forms of intrusive ads that appear when users browse the internet, play games, or engage with apps. These ads can range from persistent banner ads to full-screen flash ads and unexpected pop-ups.
AdAway operates by modifying the HOSTS file on your Android device, effectively blocking ads across all browsers, apps, games, and websites. To function correctly, AdAway requires root access, meaning it’s exclusively available for rooted devices. If your device isn’t rooted, you’ll need to root it first to utilize AdAway.
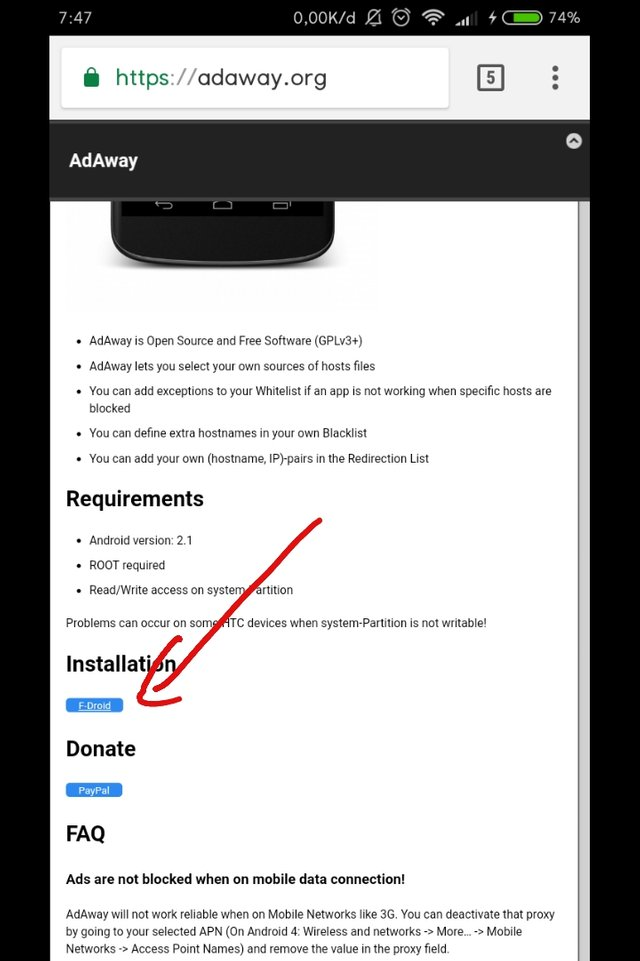
Since AdAway isn’t available on Google Play, you’ll need to source it from alternative platforms:
Third-Party App Store – F-Droid:
- Use your device’s web browser to search for and download F-Droid.
- During the download, you might receive a prompt; select “OK.”
- Open the downloaded APK file. If you haven’t enabled installations from unknown sources, you’ll receive a prompt. You can enable this feature in your device’s settings.
- After enabling, return to the Downloads folder, tap on the F-Droid APK file, and install it.
Once F-Droid is installed, use it to search for AdAway. You can opt to download either the latest version or a previous one.
How to Use AdAway to Block Ads:
- Grant Root Permission: Upon launching AdAway for the first time, you’ll be prompted to grant root permissions. Tap “OK” to provide the necessary access.
- Initiate Ad Blocking: Press the “Download files and apply ad blocking” button. AdAway will then download and apply the necessary host files to start the ad-blocking process.
- Reboot (Optional): After the ad-blocking files are applied, you might receive a suggestion to reboot your device. While it’s not mandatory, you can choose to do so.
- Scan for Adware: AdAway offers an option to scan for adware directly from its menu.
- Customize Blocking: You can whitelist or blacklist specific host files. Additionally, you can add custom host files to the blocking list if needed.
Once the process is complete, AdAway will block ads across all apps and websites. One of its significant advantages is that you don’t need to run it repeatedly to maintain ad-blocking; it remains effective unless you update the version. After setting up AdAway, it’s recommended to disable the “Unknown Sources” option in your device’s settings for security reasons.
Magisk
Magisk is a free and open-source software designed for rooting Android devices. Developed by John Wu, Magisk has become a go-to solution for Android enthusiasts looking to gain root access on their devices. Unlike traditional rooting methods, Magisk offers a systemless approach, ensuring that the device’s system partition remains unaltered. This modular design not only provides a safer rooting experience but also allows users to add new features and functionalities to their devices.
Key Features:
- Root Access: Magisk enables users to gain root access to their Android devices, allowing for deeper customizations and modifications.
- Magisk App: Alongside the rooting solution, Magisk comes with a built-in app that lets users manage root permissions and install various modules to enhance device capabilities.
- Systemless Approach: Magisk doesn’t modify the system partition of the device, making it a safer and cleaner rooting method.
- Modular Design: Users can add new features and functionalities to their devices by installing Magisk modules.
Compatibility:
Magisk is compatible with devices running Android 6.0 and above.
Moreover, Magisk is a powerful and open-source tool designed to root Android devices without modifying the system partition. This systemless approach ensures that the device remains as close to its original state as possible, while still granting users the elevated privileges associated with rooting.
Let’s dig deeper into its working style.
Key Steps to Root Your Android Device with Magisk:
Preparation: Before you can use Magisk, you need to have the TWRP custom recovery installed on your device. This requires unlocking the bootloader of your phone, which might be different for each device.
Advantages of Magisk:
- Magisk can trick Google SafetyNet into thinking the phone is not rooted.
- It uses a systemless root method, leaving system files untouched.
- Magisk Hide allows users to hide root status from certain apps, enabling apps like Google Pay to work on rooted devices.
Install ADB and Fastboot:
- For Windows, download the latest version of Android SDK Platform Tools and extract them to a convenient folder.
- For Linux users, simply use the command sudo apt install adb fastboot.
Flash TWRP:
- Download the latest version of TWRP for your device.
- Enable developer options on your device and activate “USB debugging.”
- Connect your device to your computer and use the command fastboot flash recovery twrp-X.X.X.XXX.img to flash TWRP.
Install Magisk:
- Download the latest Magisk release on your computer.
- Use the command adb push magisk-vXX.X.zip to transfer the Magisk .zip file to your Android device.
- On your device, use TWRP to install the Magisk .zip file.
- Once the installation is complete, reboot your device.
You should now see the Magisk Manager app on your device, indicating that Magisk has been successfully installed.
Advantages of Using Magisk for Rooting Android Devices
1. Installation of Custom ROMs and Kernels:
Magisk allows users to install custom ROMs and kernels, providing a new device experience software-wise. Custom ROMs offer performance improvements, user-friendly interfaces, and frequent updates. Kernels can enhance battery life and device performance.
2. Removing Pre-installed OEM Apps:
Users can remove bloatware and unnecessary apps that come pre-installed on their devices, freeing up space and improving performance.
3. Ad-Blocking Across Apps:
Magisk enables system-wide ad-blocking, providing a smoother and interruption-free experience in apps and games.
4. Installing Incompatible Apps:
Users gain access to a wider range of apps, including those not normally compatible with their device. They can also receive Android updates before they are officially released.
5. Enhanced Display Options and Internal Storage:
Magisk allows for extensive customization of the device’s display and skins. Users can also increase their internal storage by moving apps to the SD card.
6. Improved Battery Life and Speed:
Apps like Greenify can be used to optimize device performance and extend battery life, but they require root access.
7. Comprehensive Device Backups:
Users can create full backups of their device, including apps, settings, and system data.
8. Access to Root Files:
Magisk provides access to system files and sections of the device that are normally restricted, offering more control and customization options.
9. CPU Clocking:
Users can adjust their device’s CPU speed to optimize performance or extend battery life.
10. Extensive Tweaking and Optimization:
Magisk opens up possibilities for extensive device tweaking and optimization, allowing users to tailor their Android experience to their preferences.
The advent of systemless rooting methodologies, such as Magisk, has significantly transformed the landscape of Android customization and mobile app security. Unlike traditional rooting methods that modify the system partition, systemless rooting leaves the system intact, making root detection considerably more challenging.
This subtlety in rooting mechanisms has been increasingly exploited by hackers, posing potential app security threats to mobile devices. So, how to prevent such malicious attempts? It’s time to learn about some planned strategies
10 Strategies and Features to Prevent Apps from Running on Magisk Supported Rooted Devices:
The rise of systemless rooting methodologies like Magisk has complicated root detection, leaving mobile devices vulnerable to security threats. Apps lacking robust security solutions struggle to detect such rooting, compromising overall security. Ensuring an app’s ability to accurately identify a device’s root status is crucial for maintaining mobile application integrity.
Let’s throw light on the key strategies
-
Implement Root Detection Mechanisms:
Integrate advanced root detection mechanisms within your app to identify systemless rooting methods like Magisk.
-
Leverage SafetyNet Attestation:
Utilize Google’s SafetyNet Attestation API to verify the integrity of the device and ensure it hasn’t been tampered with.
-
Regularly Update Detection Methods:
Stay abreast of the latest rooting techniques and continuously update your app’s root detection methods to counteract new rooting strategies.
-
Educate Users:
Proactively educate your app’s users about the potential risks associated with rooting their devices and encourage them to maintain a secure device environment.
-
Use Obfuscation Techniques:
Implement code obfuscation to make it more difficult for attackers to reverse engineer your app and bypass root detection mechanisms.
-
Monitor App Behavior:
Regularly monitor your app’s behavior and performance for any anomalies that could indicate it is running on a rooted device.
-
Collaborate with Security Experts:
Work with mobile app security experts and leverage their knowledge to enhance your app’s root detection capabilities.
-
Encourage Secure Practices:
Promote secure practices among your user base, encouraging them to install mobile application security solutions that can detect systemless rooting methods.
-
Provide Clear Communication:
Clearly communicate the risks associated with rooting to your users and explain why certain functionalities may be restricted on rooted devices.
-
Offer Alternative Solutions:
For users on rooted devices who are unable to access certain app functionalities, provide alternative solutions or versions of your app that maintain security without requiring root access.
How AppSealing Helps?
AppSealing delivers comprehensive and continuous security for your mobile application, vigilantly overseeing operations on rooted devices to maintain a safe ecosystem. It guarantees a security standard for mobile applications equivalent to that experienced on non-rooted devices. Serving as a formidable mobile app security shield, AppSealing scrutinizes the mobile application for any unintentional interactions with the memory, filesystem, firmware, and more.
Implications on Businesses When Apps are Used on Rooted Devices:
While rooting provides users with more control over their devices, it introduces significant security risks that can have severe implications for businesses, especially those dealing with sensitive user data. Companies need to carefully weigh the risks and implement robust security measures to protect their apps and users, even considering disallowing their apps from running on rooted devices to maintain a secure and trustworthy environment.
Here are some of the key risks:
-
Data Vulnerability:
On a rooted device, the sandboxing security model of Android is compromised, allowing malicious apps to access and modify other apps’ data. This poses a severe risk for apps dealing with sensitive user information, as it can lead to data theft.
-
Network Security Risks:
Rooted devices are susceptible to Man-in-the-Middle (MitM) attacks and fraudulent certificates, which can compromise the secure communication between the app and the server. This can lead to data interception and unauthorized access to user information.
-
Abuse of App Functionalities:
Rooted devices allow users or malicious actors to abuse app functionalities, leading to scenarios like spoofing, cheating, and unauthorized access to premium features.
-
Reputation and Financial Loss:
For businesses, especially in the financial sector, the risks associated with running apps on rooted devices can translate to substantial financial losses and damage to the company’s reputation.
-
Intellectual Property Theft:
The ease of access to app data and functionalities on rooted devices makes intellectual property theft a significant concern, as attackers can reverse engineer the app to access proprietary algorithms or content.
-
Legal and Compliance Issues:
For apps dealing with regulated data, such as personal health information, running on a rooted device can lead to non-compliance with legal and regulatory standards, resulting in legal repercussions and fines.
-
Loss of User Trust:
The potential for data breaches and unauthorized access on rooted devices can lead to a loss of trust among users, affecting the app’s user base and popularity.
-
Increased Support and Maintenance Costs:
Dealing with the implications of running on rooted devices can lead to increased costs for businesses in terms of customer support, security updates, and maintenance.
-
Challenges in Risk Management:
Deciding whether to allow the app to run on rooted devices, implementing root detection mechanisms, and managing the associated risks can be challenging and resource-intensive for businesses.
-
Potential for Targeted Attacks:
Rooted devices are more susceptible to targeted attacks, as attackers can leverage the privileged access to deploy sophisticated malware or conduct espionage.
Conclusion:
Systemless rooting methodologies like Magisk have revolutionized Android customization, offering users unparalleled control over their devices. However, this innovation doesn’t come without its challenges, especially in terms of app security on rooted devices. Magisk, while powerful, makes root detection difficult, posing potential vulnerabilities for mobile applications, particularly those without robust security measures.
Appsealing as a mobile app security platform, addresses these challenges head-on, providing comprehensive protection equivalent to that on non-rooted devices. It ensures a secure environment, even on rooted devices, by monitoring activities and preventing inadvertent access to crucial system components.