On July 19, 2024, a routine software update from cybersecurity firm CrowdStrike led to an unprecedented global IT outage, affecting approximately 8.5 million Microsoft Windows devices. The incident, which experts have called the largest IT outage in recent history, caused massive disruptions across multiple industries, including aviation, healthcare, banking, and government services. This article delves into the details of the incident, its causes, the impact on various sectors, and the recovery efforts undertaken to mitigate the damage.
Brief Overview of the Incident
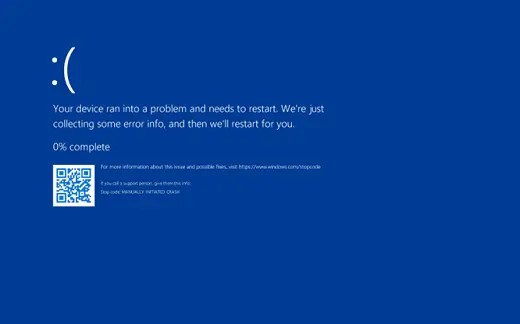
The outage began when CrowdStrike released a sensor configuration update to its Crowdstrike Falcon platform at 04:09 UTC. This update contained a logic error that caused Windows systems to crash, resulting in the infamous “Blue Screen of Death” (BSOD).
The problematic update was intended to enhance security by targeting newly observed malicious named pipes used by common command-and-control (C2) frameworks in cyberattacks. However, the update inadvertently caused a system crash due to a logic error.
Scope of Impact
Microsoft disclosed that approximately 8.5 million Windows devices were affected by the faulty update, representing less than 1% of all Windows machines globally. Despite the relatively small percentage, the impact was significant due to the widespread use of CrowdStrike’s Falcon platform in critical enterprise systems. The outage affected major airlines, hospitals, banks, and government services, highlighting the vulnerabilities in interconnected IT infrastructures.
What was the cause of the outage?
The root cause of the outage was a flawed sensor configuration update released by CrowdStrike. The update, part of routine operations to enhance protection mechanisms, contained a logic error in Channel File 291. This file controls how Falcon evaluates named pipe execution on Windows systems. The logic error caused an infinite loop, consuming CPU resources and resulting in system crashes.
Channel Files and Their Role:
- Channel Files are located in C:\Windows\System32\drivers\CrowdStrike\ and have filenames that start with “C-” followed by a unique identifier number.
- These files are part of the behavioral protection mechanisms used by the Falcon sensor, updated several times a day in response to novel tactics, techniques, and procedures discovered by CrowdStrike.
Channel File 291:
- Channel File 291 specifically controls how the Falcon sensor evaluates named pipe execution on Windows systems.
- Named pipes are used for normal, interprocess, or intersystem communication in Windows.
- The update at 04:09 UTC was designed to target newly observed malicious named pipes used by C2 frameworks but triggered a logic error leading to an OS crash.
The update was released at 04:09 UTC on July 19, 2024, and was identified and isolated by 05:27 UTC. Systems running Falcon Sensor for Windows version 7.11 and above that downloaded the updated configuration between 04:09 UTC and 05:27 UTC were affected.
Impact on Major Industries
Major airlines, including Delta, United, and American Airlines, issued ground stops due to communication issues caused by the IT outage. This led to thousands of flight cancellations and delays globally.
Delta Air Lines and its regional affiliates canceled over a quarter of their scheduled flights on the East Coast, while United and United Express canceled over 500 flights. American Airlines’ network saw 450 flight cancellations.
Airports faced significant challenges with check-in systems and flight information display systems (FIDS), which showed the “Blue Screen of Death.” This forced many airports to revert to manual processes for issuing boarding passes and updating flight statuses on whiteboards.
Hospitals experienced disruptions in electronic medical record systems, forcing a return to manual, paper-based methods. This shift slowed down operations considerably, particularly for younger healthcare professionals accustomed to digital systems.
– Elective surgeries and non-emergent procedures were postponed in several hospitals, including Mass General Brigham and Cincinnati Children’s Hospital Medical Center. Laboratory operations and radiology services also faced delays, impacting patient care and treatment plans.
ATM and Online Banking Issues:
– Major banks such as Bank of America, Capital One, Chase, TD Bank, and Wells Fargo reported service interruptions. These disruptions affected customer transactions, online banking services, and internal operations.
Waterloo station in London
– Some card payment services were disrupted, causing delays and inconvenience for customers attempting to make transactions.
Customer Communication and Support
– Banks like TD Bank informed customers about the global technology disruption and warned of longer wait times for services. They encouraged customers to use ATMs and visit branches for transactions.
– Banks and financial institutions worked to reassure customers and restore services as quickly as possible. This included deploying IT teams to address the issues and provide support.
Recovery Efforts
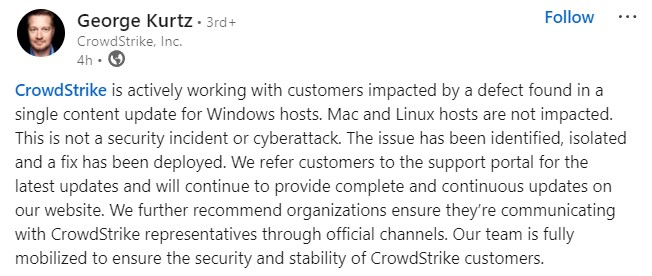
CrowdStrike quickly identified the issue and rolled back the problematic update by 05:27 UTC on July 19, 2024. The company provided remediation steps and worked with affected customers to restore services. CrowdStrike emphasized that this was not a cyberattack but a technical flaw. The company mobilized all available resources to assist customers and ensure the security and stability of their systems.
In a statement, CrowdStrike CEO George Kurtz apologized for the disruption and assured customers that the issue had been identified and isolated. He emphasized the company’s commitment to transparency and continuous updates through official channels.
Microsoft’s Collaboration with Cloud Providers
Microsoft played a crucial role in the recovery efforts, deploying hundreds of engineers and experts to work directly with customers to restore services. The company collaborated with other cloud providers, including Google Cloud Platform (GCP) and Amazon Web Services (AWS), to share information and coordinate responses.
Microsoft provided manual remediation documentation and scripts to assist affected users. The company also released a USB recovery tool aimed at repairing the affected devices, offering two primary recovery options: recovering from WinPE (Windows Preinstallation Environment) and recovering from Safe Mode.
Challenges in Implementing Fixes
The recovery process was time-consuming and required significant IT resources, especially for organizations with large numbers of affected devices. Many systems required manual intervention, including rebooting in safe mode and deleting specific files. This process was particularly challenging for smaller organizations lacking robust IT support.
The incident highlighted the need for more rigorous testing protocols and controlled deployment strategies for critical software updates. It also underscored the vulnerabilities associated with widespread reliance on single vendors for cybersecurity infrastructure.
Our Take:
While cloud-based security tools certainly have their place, this incident demonstrates the risks of over-reliance on any single security solution or vendor. A defense-in-depth strategy that incorporates multiple complementary security measures, including app-level protections, is crucial for maintaining operational continuity and protecting sensitive data. At AppSealing, we remain committed to providing reliable, self-contained security solutions that empower our clients to maintain control over their application security, even in the face of broader infrastructure challenges. This incident serves as a reminder of why that approach is more important than ever in today’s interconnected digital landscape.
Proactive Anomaly Detection:
In the rapidly evolving landscape of mobile app security, it’s essential to monitor code performance in real-time during production. It allows AppSealing to proactively detect any anomalies or performance degradation that could indicate security vulnerabilities or attempted breaches. By implementing robust monitoring solutions, AppSealing can identify unusual patterns or behaviors that might signify a security threat, enabling swift response and mitigation.
Insights into Real-World Behavior:
Performance analytics provide valuable insights into how AppSealing’s security measures behave under real-world conditions. It is invaluable for understanding how the security code interacts with various app environments, user behaviors, and potential attack vectors. By analyzing this information, AppSealing can continuously refine and optimize its security solutions to better protect mobile apps against emerging threats.
Continuous Improvement:
Real-time monitoring allows AppSealing to gather data on the effectiveness of its security measures across a diverse range of apps and user scenarios. This continuous feedback loop enables the company to make data-driven decisions for improving its products. By identifying trends, common vulnerabilities, or areas where security measures might impact app performance, AppSealing can iteratively enhance its solutions to provide more robust and efficient protection.
Enhanced Customer Experience:
By monitoring the performance of its security solutions in real-time, AppSealing can ensure that its protective measures don’t negatively impact the end-user experience. Performance analytics can help identify any instances where security implementations might be causing slowdowns or crashes, allowing for quick adjustments to maintain both security and usability.
Conclusion
The CrowdStrike update incident serves as a stark reminder of the interconnected nature of modern IT systems and the potential for localized software issues to cascade into global disruptions. The incident caused significant disruptions across multiple industries, highlighting the critical importance of robust IT systems and contingency plans. As organizations continue to recover from this unprecedented IT meltdown, the tech industry faces renewed scrutiny over its practices and the potential risks associated with centralized cybersecurity solutions. The incident emphasizes the need for improved resilience and disaster recovery strategies in an increasingly digitized world.