The EU regulation has also adopted the Digital Operational Resilience Act (DORA) to ensure that significant ICT service providers and financial organizations can deal with digital disruptions, including cyber threats. DORA improves the operational resilience of the whole financial sector in the EU by establishing generally applicable rules for ICT risk management across the industry. The act was adopted in 2023 and will be effective as of January 2025.
Purpose of DORA
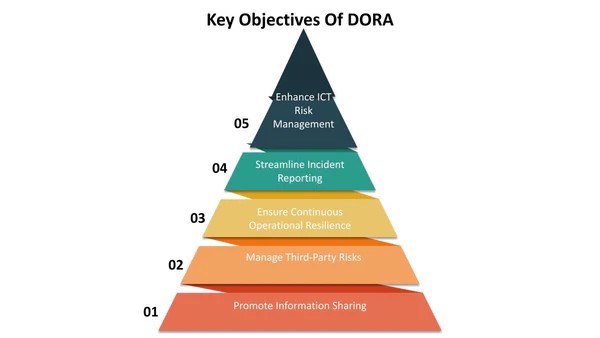
Given that so many financial services are now deeply rooted in digital systems, DORA’s role is to ensure that these institutions can identify, prevent, and manage cyber threats so as not to compromise the confidentiality, integrity, and availability of the information they process on behalf of their customers. DORA promotes resilience through clearly defined standards to counter systematic risks that may arise due to ICT failure. It also addresses third-party risks by regulating outsourced ICT services to comply with the set standards.
The act improves the rate of disclosure by asking organizations to report significant ICT incidents to the relevant authorities so that cybercrimes are collectively dealt with. In essence, DORA strengthens the protection of the EU financial sector’s consumers, stabilizes the market, and improves the general readiness against the increasing dangers of the digital environment.
DORA scope
From a company perspective, DORA is all-encompassing. It affects any company working in the financial sector with dependencies on digital systems or in collaboration with third-party ICT suppliers for services within the EU. DORA is not limited to traditional financial institutions such as banks but expands to other entities and their digital environments.
1. Core Financial Entities
Entities in the EU’s financial industry, including banks, payment service providers, insurance firms, investment companies, and asset managers, are required to adhere to DORA. These entities are most affected and must adjust their ICT risk management, resilience testing, and incident reporting to meet DORA standards. Businesses must incorporate resilience within their digital platforms so that organizations can monitor, prevent, and manage cyber threats appropriately.
2. Critical Third-Party ICT Providers
This applies to third-party ICT providers offering financial organizations platforms, storage, cloud solutions, and security services. However, if a company does not qualify as a financial institution, any ICT provider that supplies such an institution within the EU, regardless of its location, must adhere to DORA. This will help ensure that third-party vulnerabilities do not affect the functioning of a particular financial entity.
3. Outsourced Service Providers and Business Partners
Other organizations that outsource essential ICT functions are also implicated. DORA emphasizes contractual obligations to ensure that third-party providers meet resilience requirements. Financial institutions have to evaluate all their vendors providing digital services to ensure that contractual agreements contain provisions for data security, disaster recovery, and compliance with DORA acts.
4. Management Accountability
DORA directly assigns senior management and boards responsibility for comprehending and managing ICT risk. The regulatory body demands that organizations in financial sectors adopt an excellent corporate governance structure that determines the board of directors to be in charge and accountable for implementing and monitoring the resiliency standards. Failure to comply can lead to fines or reputation loss, which places pressure on the leadership to consider digital preparedness.
5. Global Companies with EU Operations
For companies involved in financial operations in the EU, DORA outlines precise expectations that apply to ICT systems at every branch worldwide, demanding alignment with EU resilience standards. Compliance calls for companies to integrate DORA’s requirements into their wider digital risk strategies, even if EU-focused operations represent just a small fraction of their entire business. The regulation’s reach ensures that everything tied to EU-facing functions, data storage, and ICT services sticks to DORA’s defined resilience benchmarks.
6. Regulated Reporting and Transparency Requirements
The DORA regulates and standardizes reporting obligations, requiring firms to notify and report significant ICT events to the authorities in the EU. This puts a lot of pressure on financial institutions to invest in soundtracking and reporting structures–to categorize and quickly analyze incidents effectively.
Current Status of DORA
By October 2024, the Digital Operational Resilience Act (DORA) was in its last stretch of preparation, setting the stage to become fully enforceable on January 17, 2025. Financial organizations and their ICT third-party service providers have been working diligently to align their systems and operations with DORA’s strict requirements. To support this, the European Supervisory Authorities (ESAs) have released a comprehensive set of technical standards and guidelines to aid compliance.
In July 2024, the ESAs rolled out a second series of policy documents under DORA, which included final draft regulatory technical standards and guidelines aimed at strengthening the digital resilience of the EU’s financial sector. A few months earlier, in May 2024, they had also introduced templates and tools for an optional trial run, giving entities a hands-on opportunity to gear up for DORA’s full implementation.
DORA Enforcement
It’s undoubtedly a coordinated push by both European and national authorities to build strong digital resilience across the EU’s financial sector. Through clear standards, established penalties, and supportive resources, DORA aims to integrate solid cybersecurity practices throughout all layers of financial operations and ICT service providers.
Here’s a detailed breakdown of how DORA enforcement is designed to work and its implications for affected entities:
1. Implementation Timeline and Compliance Deadline
The European Union set the wheels in motion for the Digital Operational Resilience Act (DORA) by adopting it on January 16, 2023. Talking about the date, the clock is now ticking, with a compliance deadline of January 17, 2025. By then, any organization falling under DORA’s standards must be fully aligned with its requirements. Financial institutions are on the list, of course, but the scope also pulls in crucial ICT service providers that support the EU’s financial industry.
2. Supervisory Authorities and Oversight Mechanism
There is a network of European Supervisory Authorities (ESAs) like the European Banking Authority (EBA), European Insurance and Occupational Pensions Authority (EIOPA), and European Securities and Markets Authority (ESMA) that guide and enforce DORA’s standards across the EU, working closely with national authorities (NCAs) in each member country.
3. Key Areas of Compliance and Enforcement Focus
Enforcement will focus on several core areas, which align with DORA’s primary objectives:
Enforcement under DORA will zero in on a few critical areas that match its primary goals:
- ICT Risk Management: To meet compliance standards, robust ICT risk management systems, complete with continuously monitored and reviewed controls and continuous monitoring, will be needed. Companies will also need to implement these systems, which will include regular risk assessments, controls, and continuous monitoring. Enforcement teams will look closely at whether businesses have solid policies, procedures, and clear accountability to manage ICT risks effectively.
- Incident Reporting: DORA requires companies to swiftly report major ICT incidents to the relevant authorities using standardized protocols. Supervisory bodies will monitor these reports closely to ensure transparency and encourage prompt responses to emerging issues.
- Resilience Testing: The entities establish and maintain comprehensive digital operational resilience testing programmes that are expected to regularly test robust digital defences. Authorities will review these testing protocols, looking at the methods used and the results, to ensure that any weaknesses are properly addressed.
- Third-Party Risk Management: When it comes to outsourced ICT services, institutions need to actively manage and monitor the risks involved. Contracts with third-party providers should clearly lay out compliance expectations, and regulators will be assessing how institutions handle reliance on these providers, especially where dependencies or concentration risks might arise.
- Information Sharing and Threat Intelligence: To boost resilience across the sector, institutions are encouraged to share threat intelligence with others in the industry. Authorities aim to promote this collaboration, as it can be a powerful tool in defending against new and evolving threats.
4. Enforcement Measures and Penalties for Non-Compliance
Fines and Administrative Penalties:
For entities that fall short of DORA compliance, financial penalties are available. These penalties aren’t light, either—they’re crafted by national authorities to be impactful, aiming to push organizations toward full compliance.
Operational and Governance Reviews:
Authorities can conduct detailed reviews of an institution’s operations and governance. If they find that the institution isn’t meeting DORA’s standards, they can step in and require specific corrective actions or a plan to fix issues within a set timeline.
Suspension of Services: In the most severe cases, especially with ICT providers, authorities have the power to suspend or limit services. This option protects the financial sector from potential systemic risks that could come from weak resilience standards.
5. Management Accountability and Reporting Obligations
Senior Management Accountability: Under DORA, and with clear segregation, senior management and boards are expected to set and approve all measures related to ICT risk management processes. It clearly directs to eliminate the complexities arising from gaps, overlaps, and conflicts, and falling short of these responsibilities could lead to personal consequences, such as fines or other penalties.
Regular Reporting Obligations: Financial institutions and ICT providers are required to submit regular reports on their resilience efforts, compliance activities, and any significant incidents. These reports give authorities a clear view of each organization’s compliance status and help them monitor new and emerging risks.
6. Technical Standards and Guidelines for Enforcement
The European Supervisory Authorities (ESAs), working with the European Commission, have crafted detailed technical standards and guidelines to help with enforcement. These standards set clear expectations for compliance, covering things like how incidents should be reported, methods for assessing risk, and steps for resilience testing. Financial institutions and their third-party providers are expected to follow these guidelines closely to ensure they meet DORA’s requirements smoothly.
7. Transitional Period and Support for Compliance
The European Supervisory Authorities (ESAs), together with the European Commission, have created a set of technical standards and guidelines to make enforcement clearer. These standards give straightforward instructions on what’s expected for compliance, covering everything from how incidents should be reported to methods for assessing risks and procedures for resilience testing.
8. Long-Term Enforcement and Impact
By setting and maintaining high standards, the DORA acts to safeguard and mandate financial entities’ operational stability and reduce risks of ICT disruptions that could impact the wider economy. With continuous oversight from the ESAs and NCAs, institutions are encouraged to adopt proactive security practices. With mechanisms for enforcing adherence and addressing non-compliance, the DORA approach is meant to lessen systemic risks and build confidence in the digital strength of the EU’s financial systems among consumers and stakeholders alike.
What are the DORA requirements?
By focusing on comprehensive ICT risk management, incident reporting, resilience testing, third-party oversight, and robust governance, DORA requirements aim to ensure that financial institutions and their ICT providers are well-prepared to withstand digital threats and maintain operational continuity.
Here’s a detailed look at the key requirements under DORA:
1. ICT Risk Management
Governance Framework: Companies must establish a formal governance framework for managing ICT risks, integrated into their overall risk management policies. This framework should define roles, responsibilities, and accountability for ICT risk management.
Risk Assessments and Controls: Regular assessments of ICT risks are required, with specific measures to control and mitigate these risks. This includes asset inventories, backup procedures, and disaster recovery plans.
Monitoring and Maintenance: Systems must be continuously monitored for vulnerabilities and updated regularly to defend against potential cyber threats.
2. ICT Incident Reporting
Incident Detection and Response: Institutions must have robust mechanisms for detecting and managing ICT-related incidents, ensuring business continuity and data integrity during disruptions.
Reporting Requirements: Significant ICT incidents must be reported promptly to the relevant supervisory authorities using standardized reporting templates. This ensures authorities can monitor systemic risks and respond swiftly if necessary.
Follow-Up Analysis: Post-incident reviews are required to analyze the root causes, measure impacts, and implement corrective actions to prevent similar incidents in the future.
3. Digital Resilience Testing
Regular Testing: Financial institutions must perform regular digital resilience testing, including assessments of systems, applications, and security controls.
Advanced Testing for High-Impact Entities: Institutions classified as “high-impact” must conduct more sophisticated tests, such as threat-led penetration testing (TLPT) and Red Team Exercises, simulating real-world cyberattacks to evaluate the robustness of their defenses.
Remediation and Reporting: Results from these tests must be used to improve security measures, and authorities may review testing outcomes to ensure that vulnerabilities are addressed promptly.
4. ICT Third-Party Risk Management
Risk Assessment of Vendors: Financial institutions must assess the risks posed by third-party ICT providers, particularly those offering critical services like cloud storage, cybersecurity, or data analytics.
Contractual Requirements: Contracts with third-party providers should include clear terms on resilience standards, data protection, and contingency plans. DORA emphasizes that companies must have written agreements outlining these requirements.
Concentration Risk and Exit Strategies: Institutions are encouraged to manage concentration risk by avoiding heavy reliance on a single provider. They should also have exit strategies and contingency plans in case of service disruptions from a third-party provider.
5. Information Sharing and Collaboration
Threat Intelligence Sharing: DORA encourages financial institutions to share threat intelligence and best practices with one another to build a collaborative defense posture against cyber threats.
Cybersecurity Awareness and Training: Firms are encouraged to raise awareness about ICT risks among employees, particularly those in key roles, and provide regular training on recognizing and mitigating cybersecurity risks.
6. Reporting and Accountability
Management Accountability: Senior management and boards are held accountable for DORA compliance. They must understand and oversee ICT risk management, with clear documentation of their involvement in resilience strategy.
Regular Reporting and Disclosures: Financial institutions are required to report on their compliance status, resilience measures, and incident handling processes to the relevant regulatory authorities.
Transparency: Companies must be transparent about their digital resilience, particularly when sharing information with stakeholders, supervisors, and, where appropriate, customers.
7. Operational Continuity and Disaster Recovery
Business Continuity Plans: Institutions must have robust business continuity plans that address potential ICT disruptions, ensuring minimal downtime and the ability to maintain critical operations.
Recovery and Backup Procedures: DORA requires entities to establish secure backup systems and data recovery procedures that allow for the rapid restoration of services after a disruption.
8. Technical Standards and Guidelines
DORA outlines specific technical standards for various resilience activities, including incident reporting templates, risk assessment frameworks, and resilience testing protocols. Companies are expected to follow these standards to meet DORA compliance effectively.
Conclusion
DORA sets a high standard for digital operational resilience across the EU financial sector, reflecting the growing importance of safeguarding against ICT and cyber risks. By establishing comprehensive requirements for ICT risk management, incident reporting, resilience testing, third-party oversight, and management accountability, DORA ensures that financial institutions and critical ICT providers are better prepared to prevent and respond to digital threats. As DORA becomes enforceable in January 2025, institutions that prioritize compliance will not only enhance their resilience but also contribute to a more secure and stable financial ecosystem within the EU. Embracing DORA’s framework ultimately protects customers, strengthens market confidence, and positions the financial sector to withstand an increasingly complex cybersecurity landscape.