In today’s rapidly evolving mobile app landscape, robust protection is more critical than ever. With a dramatic rise in mobile app vulnerabilities and attacks, developers must implement comprehensive mobile application security measures to safeguard sensitive user data and app functionality. From combating malware and data breaches to preventing reverse engineering and phishing attacks, this blog explores essential strategies for mobile app protection in 2024. As mobile app threats grow more sophisticated, leveraging advanced technologies like AI, machine learning, and real-time, protection is crucial for ensuring secure, trustworthy applications across platforms.
What is Mobile App Protection?
Mobile App Protection, being a critical component of mobile application development, refers to the strategies and measures implemented to safeguard mobile applications from vulnerabilities and malicious actors. In 2024, the landscape of mobile app security is more challenging than ever, with threats rapidly evolving alongside technological advancements. Reports indicate a significant rise in mobile app vulnerabilities and attacks. For instance, Kaspersky’s Q1 2024 data highlights over 10.1 million blocked attacks involving malware, adware, and unwanted software, with adware alone constituting 46% of these threats.
Similarly, the likelihood of attacks on Android apps surged from 34% in 2023 to 84% in 2024, while iOS apps saw an increase from 17% to 29%. As mobile app usage continues to grow, with users spending an average of 5.5 hours daily on apps, securing these applications against threats like data breaches, insecure data transmission, and malicious code is paramount. Implementing multiple mobile application security measures include design, coding, testing, deployment, and maintenance to protect user data, prevent unauthorized access, and ensure the integrity of the app across different platforms, including Android, iOS, and iPhone.
The primary goal of mobile app protection is to prevent unauthorized access, data breaches, malware attacks, and other app security threats that can compromise sensitive user information and the app’s functionality.
Common Mobile App Security Threats
Understanding the common security threats that mobile apps face is crucial for developers and security professionals to implement effective protection measures. This section will explore various security threats that can compromise mobile app security, including those specific to Android and iOS platforms. By identifying and addressing these threats, organizations can better safeguard their applications and protect user data from malicious actors.
Malware:
Malware refers to any malicious software specifically designed to exploit vulnerabilities in mobile devices, such as smartphones and tablets.
Mobile malware poses significant threats to both individual users and organizations by targeting the operating systems and applications on these devices.
Data Breaches:
Data breaches represent a significant security threat to mobile applications, involving unauthorized access to sensitive user information. These breaches can result from various vulnerabilities within the app’s architecture or external attacks, leading to severe consequences for both users and businesses.
Insecure Data storage:
Insecure data storage refers to vulnerabilities arising from improper handling and protection of sensitive data within a mobile app’s storage mechanisms. Such data breaches as threats are prevalent when developers assume that malware or unauthorized users will not access a device’s filesystem, leading to inadequate security measures.
Common vulnerabilities include storing sensitive information such as
- usernames,
- passwords, and
- credit card numbers in plaintext,
using weak or nonexistent encryption, and failing to implement robust access controls.
These weaknesses allow attackers to easily access and manipulate sensitive data, especially if the device is lost, stolen, or compromised by malware.
Unsecured Wi-Fi Networks
Unsecured Wi-Fi networks pose a significant threat due to their lack of encryption and authentication protocols, which can expose sensitive data transmitted between mobile apps and servers.
When a mobile device connects to an unsecured Wi-Fi network, such as those commonly found in public places like cafes, airports, or hotels, the data exchanged over the network is susceptible to interception by malicious actors.
Attackers can employ techniques like man-in-the-middle (MITM) attacks, where they position themselves between the device and the network access point, capturing sensitive information such as login credentials, personal data, and financial information.
Reverse Engineering
Reverse engineering poses a significant security threat to mobile applications by allowing attackers to deconstruct and analyze the app’s compiled binaries to extract sensitive information and understand its internal workings. This process involves using tools to decompile Android APK files or iOS IPA files, enabling attackers to access the source code, proprietary algorithms, and cryptographic keys. Once reverse engineered, attackers can exploit discovered vulnerabilities, replicate app functionalities, or inject malicious code.
 Phishing Attacks
Phishing Attacks
Phishing attacks on mobile applications utilize deceptive social engineering techniques to trick users into divulging sensitive information. The compact nature of mobile screens and the tendency for users to multitask on their phones is easy attack target that that often manifest through various communication channels such as SMS (smishing), email, social media, and even in-app messages, targeting mobile users due to the increased reliance on smartphones for both personal and professional activities.
Once a user interacts with these deceptive elements, they may be redirected to fraudulent websites designed to harvest credentials or install malware on their devices.
Inadequate Encryption
Inadequate encryption mobile applications, arises when sensitive data is not properly encrypted, leaving it vulnerable to unauthorized access and interception. This threat often results from using outdated or weak encryption algorithms, improper implementation of cryptographic protocols, or failing to encrypt data altogether. For instance, using deprecated algorithms like MD5 or SHA-1, which are susceptible to collision attacks, can compromise data integrity and confidentiality. Attackers can intercept and decipher sensitive information such as personal details, login credentials, and financial transactions.
Code Tampering:
Mobile applications Code tampering involves unauthorized modification of an app’s code to alter its functionality or behavior. This threat typically occurs after the app has been deployed and can be executed by attackers who decompile the app, modify its source code, and then repackage it. The modified app can be distributed through unofficial channels, leading to a range of malicious activities. Code tampering can enable attackers to bypass mobile application security controls, access premium features without authorization, or inject malware to steal sensitive data from users. For example, an attacker might alter the code to disable security checks or redirect user data to a malicious server. This not only compromises the app’s integrity and security but also poses significant risks to users, such as data breaches and financial loss.
Insufficient Cryptography
Insufficient cryptography is a critical mobile app security threat to mobile applications, arising from the improper implementation or use of cryptographic mechanisms, which can leave sensitive data vulnerable to unauthorized access or tampering. This threat often manifests through the use of weak or outdated encryption algorithms, such as MD5 or SHA-1, which are susceptible to cryptographic attacks like brute force or collision attacks.
Additionally, poor key management practices, such as storing encryption keys insecurely or using hardcoded keys, can compromise the encryption’s effectiveness, allowing attackers to decrypt sensitive data. Insufficient cryptography can also result from flawed encryption implementation, where programming errors or misconfigurations undermine the intended security measures. These vulnerabilities can lead to severe consequences, including data breaches, privacy violations, and intellectual property theft.
Poor Network Security
Poor network security poses a substantial threat to mobile applications by exposing data transmitted between the app and external servers to interception and manipulation by malicious actors. This vulnerability often arises from the use of insecure communication protocols, such as HTTP instead of HTTPS, which do not encrypt data in transit, making it susceptible to eavesdropping and man-in-the-middle (MITM) attacks.
Additionally, inadequate validation of SSL/TLS certificates can allow attackers to present fraudulent certificates and intercept sensitive data. Other factors contributing to poor network security include the lack of proper authentication and authorization mechanisms for API endpoints, enabling attackers to gain unauthorized access to backend systems.
Essential Mobile App Protection Strategies
White Box Cryptography Support
White-box cryptography is a sophisticated mobile app security strategy designed to protect cryptographic keys within mobile applications, even in environments where an attacker has full access to the app’s execution. White-box cryptography embeds cryptographic keys within the application code in such a way that they are indistinguishable from other data, making it extremely difficult for attackers to extract them, even with full access to the app’s binary.
Unlike traditional cryptographic methods that assume the execution environment is secure, white-box cryptography operates under the assumption that an adversary can observe and manipulate the application’s runtime environment. This approach is particularly crucial for mobile apps, which often run-on devices that are susceptible to tampering and reverse engineering.
JavaScript Code Encryption
JavaScript code encryption transforms JavaScript code into a format that is difficult to understand, with the aim of protecting the code from unauthorized access and tampering. However, due to the nature of JavaScript being executed on the client-side, true encryption is not feasible since the code must be decrypted to run in the browser. Instead, obfuscation is commonly used as a practical approach to protect JavaScript code.
- Obfuscation Techniques: Obfuscation involves transforming the code to make it less readable and harder to reverse-engineer. Common techniques include renaming variables and functions to non-descriptive names, removing whitespace and comments, and altering the code structure without changing its functionality.
- Tools and Libraries: Several tools are available for JavaScript obfuscation, such as Google Closure Compiler, JScrambler, and UglifyJS. These tools apply various obfuscation techniques to make the code difficult to interpret while maintaining its original functionality.
- Security Best Practices: To enhance the security of JavaScript code, developers should combine obfuscation with other security measures, such as implementing secure coding practices, validating user inputs, and using Content Security Policies (CSP) to mitigate risks like cross-site scripting (XSS) attacks.
Data Encryption
Data encryption is a critical component of mobile app security, providing a robust mechanism to protect sensitive information from unauthorized access and potential breaches. It ensures that data remains confidential and secure, both at rest and in transit, by transforming it into an unreadable format that can only be deciphered by authorized parties with the correct decryption key.
How Data Encryption can be implemented in iOS?
- File-Level Encryption: iOS uses strong encryption algorithms to protect data stored on the device. Apple provides built-in encryption APIs that allow developers to encrypt sensitive data stored locally, ensuring it remains inaccessible to unauthorized entities.
- Secure Enclaves: iOS devices with Secure Enclave technology provide an additional layer of security by isolating encryption keys and cryptographic operations from the main processor, enhancing the protection of sensitive data.
How Data Encryption can be implemented in Android?
- File-Based Encryption (FBE): Android supports file-based encryption, allowing different files to be encrypted with different keys. This provides granular control over data access and ensures that data remains protected even if the device is compromised.
- Android Keystore System: Android provides the Keystore system for securely storing cryptographic keys, protecting them with hardware-backed security, and making them inaccessible to unauthorized apps and users.
Protection from SSL Pinning

By embedding or “pinning” a server’s SSL certificate or public key within the app, developers can ensure that the app only communicates with a trusted server, even if malicious actors attempt to intercept or alter the data in transit.
- Android Implementation: In Android, SSL pinning can be implemented using libraries like OkHttp and Retrofit. Developers can configure these libraries to pin the server’s certificate or public key, ensuring secure communication.
- iOS Implementation: For iOS apps, SSL pinning can be implemented using NSURLSession or third-party libraries like Alamofire. The app can be configured to compare the server’s certificate or public key against the pinned version, enhancing security.
Real-time Protection
Real-time protection of mobile apps provides continuous monitoring and defense against potential threats such as malware, unauthorized access, and code tampering, as they occur. Real-time protection can identify anomalies and respond before they escalate into significant mobile application security breaches.
Technical Implementation
- Runtime Application Self-Protection (RASP): RASP technology is embedded within the application to provide real-time monitoring and protection. It can detect and block threats such as SQL injection and code injection attempts during the app’s runtime, minimizing the window of vulnerability.
- Threat Intelligence Integration: Leveraging threat intelligence platforms allows real-time protection systems to stay informed about emerging threats, enabling them to adapt security configurations and respond proactively to new attack patterns.
- Machine Learning and AI: Advanced real-time protection solutions use machine learning and AI to analyze app behavior and network traffic. These technologies can distinguish between normal and malicious activities, reducing false positives and enhancing threat detection accuracy.
Anti- Keylogger
By preventing keyloggers from capturing input data, anti-keylogger measures protect sensitive information such as login credentials and financial details from being intercepted by malicious actors.
Anti-keylogger strategies help maintain user privacy by ensuring that personal and confidential information entered into the app remains secure and inaccessible to unauthorized parties.
Technical Implementation
- Input Obfuscation: One common technique is to obfuscate or randomize input data, making it difficult for keyloggers to capture meaningful information. This can involve using virtual keyboards or randomized input fields.
- Behavioral Analysis: Implementing behavioral analysis can help detect and block keyloggers by monitoring for unusual input patterns or unauthorized access to input data.
- Secure Input Methods: Utilizing secure input methods, such as biometric authentication (fingerprint or facial recognition), can reduce the reliance on traditional keyboard input, thereby minimizing the risk of keylogging.
Data Security
Data security measures protect personally identifiable information (PII), financial data, health records, and other sensitive information from unauthorized access and breaches. This is critical in preventing identity theft, financial fraud, and other cybercrimes. Implementing robust data security practices ensures compliance with data protection regulations such as GDPR, HIPAA, and PCI DSS. Non-compliance can result in significant legal and financial penalties, as well as reputational damage.
Technical Implementation
- Data Encryption: Encrypting data both at rest and in transit is a fundamental practice. This involves using strong encryption algorithms like AES-256 to ensure that even if data is intercepted, it remains unreadable without the appropriate decryption key.
- Secure Storage: Utilize platform-specific secure storage mechanisms, such as the Android Keystore and iOS Keychain, to store sensitive data securely. Avoid storing sensitive information in plaintext or in easily accessible locations.
- Access Controls: Implement strict access controls to ensure that only authorized users and applications can access sensitive data. This includes using role-based access control (RBAC) and multi-factor authentication (MFA) to enhance mobile application security.
- Data Minimization: Collect and store only the minimum amount of data necessary for the app’s functionality. This reduces the risk of data breaches and minimizes the impact if a breach occurs.
Packet Sniffing Tool Detection
By detecting packet sniffing tools, mobile apps can prevent unauthorized access to sensitive data such as login credentials, personal information, and financial transactions, which might otherwise be intercepted during transmission. Detecting packet sniffing activities helps maintain the integrity and confidentiality of data transmitted over the network, ensuring that communication between the app and its servers remains secure. Packet sniffing detection can thwart MITM attacks, where attackers intercept and potentially alter the communication between a mobile app and its server.
Technical Implementation
- Network Monitoring and Analysis: Implement network monitoring tools that can detect unusual traffic patterns indicative of packet sniffing activities. These tools can analyze network traffic for anomalies that suggest the presence of sniffers.
- Intrusion Detection Systems (IDS): Use IDS to monitor network traffic for suspicious activities that may indicate packet sniffing attempts. IDS can alert administrators to potential threats in real-time, enabling swift countermeasures.
- Secure Communication Protocols: Employ secure communication protocols such as HTTPS and TLS to encrypt data in transit, making it unreadable to packet sniffers. This ensures that even if data packets are captured, they cannot be easily decrypted.
Tools and Solutions for Mobile App Protection
In the realm of mobile application security, a comprehensive approach involves using various tools and solutions to identify, mitigate, and protect against vulnerabilities and threats. Key methodologies include Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Runtime Application Self-Protection (RASP). Each plays a unique role in securing mobile applications throughout their lifecycle.
Static Application Security Testing (SAST)
SAST is a white-box testing method that analyzes an application’s source code, bytecode, or binary code to identify security vulnerabilities. It does not require the application to be running, allowing vulnerabilities to be detected early in the development lifecycle.
- Early Detection: Identifies vulnerabilities during the coding phase, enabling developers to address issues before the application is deployed.
- Comprehensive Analysis: Scans the entire codebase to uncover potential security flaws such as SQL injection, cross-site scripting (XSS), and buffer overflows.
Dynamic Application Security Testing (DAST)
DAST is a black-box testing approach that evaluates an application while it is running. It simulates attacks to identify vulnerabilities that could be exploited by malicious actors. It tests the application in a production-like environment, identifying vulnerabilities that may be missed by static analysis. Furthermore, a DAST tool can test applications without access to the source code, making it suitable for third-party applications.
Runtime Application Self-Protection (RASP)
RASP is a security technology that integrates within a mobile application’s runtime environment to provide real-time protection against threats. It monitors the application’s behavior and intercepts potentially malicious actions.
Benefits:
- Real-Time Protection: Detects and blocks threats as they occur, providing immediate response to attacks such as code injection and tampering.
- Zero-Day Protection: Offers protection against unknown vulnerabilities by analyzing application behavior and identifying anomalies.
- Low False Positives: Due to its deep integration with the application, RASP can accurately distinguish between legitimate and malicious activities, reducing false positives.
AppSealing’s RASP security solution provides robust protection by embedding security features within the application. It continuously monitors for threats and applies runtime protection measures without impacting performance. AppSealing’s RASP is designed to protect against a wide range of threats, including data breaches and tampering, by intercepting calls and analyzing traffic in real-time.
Future Trends in Mobile App Protection and the Role of AI and ML
The future of mobile app protection is heavily influenced by AI and ML, which are driving advancements in threat detection, user authentication, and compliance with security standards. These technologies are essential for developing more resilient and secure mobile applications in an increasingly complex threat landscape.
- AI-Driven Security: AI is transforming mobile app security by enabling more sophisticated threat detection and response mechanisms. AI algorithms can analyze vast amounts of data to identify patterns and anomalies indicative of security threats, allowing for proactive defense strategies.
- Machine Learning for Threat Prediction: ML models are being used to predict potential security threats by learning from historical data. This predictive capability allows security systems to anticipate and mitigate risks before they manifest.
- Biometric Authentication: AI and ML are enhancing user authentication processes through biometric methods such as facial recognition and fingerprint scanning. These technologies provide more secure and user-friendly authentication options, reducing reliance on traditional passwords.
- Zero-Trust Environments: The adoption of zero-trust security models is increasing, emphasizing the need to verify every access request, regardless of its origin. This approach is crucial in a landscape where mobile devices frequently access sensitive data from various locations.
- Geo-Compliance: As regulations become more stringent, geo-compliance is gaining importance, ensuring that mobile apps adhere to regional data protection laws and standards.
Conclusion
Mobile application protection is crucial in safeguarding sensitive user data and ensuring app integrity against evolving cyber threats. This comprehensive guide highlights essential strategies, including data encryption, SSL pinning, and real-time protection, to defend against vulnerabilities like malware, data breaches, and reverse engineering. Tools such as SAST, DAST, and RASP provide robust security frameworks, with AI and ML enhancing threat detection and response capabilities. As mobile threats grow more sophisticated, integrating these advanced technologies becomes vital for proactive defense. By adopting these strategies, developers can build secure, trustworthy applications that comply with regulations and maintain user trust, ensuring a resilient mobile app ecosystem in an increasingly digital world.
Frequently Asked Questions
What is mobile app protection?
Mobile app protection involves integrating multiple layers of security into a mobile application to safeguard it against static and dynamic analysis, as well as runtime threats. This includes measures to protect the app’s code, data, and functionality from unauthorized access and manipulation.
How can I secure my mobile app?
To secure a mobile app, implement strong user authentication, secure the software supply chain, encrypt data, ensure secure data storage, and protect the backend. Regularly perform security checks and use SSL certificates to secure data in transit.
What are the common threats to mobile app security?
Common threats to mobile app security include malware, data breaches, insecure data storage, reverse engineering, phishing attacks, and inadequate encryption. These threats can compromise user data and app functionality if not properly addressed.
Why is regular updating important for app security?
Regular updating is crucial for app security as it addresses vulnerabilities and bugs discovered after the app’s release. Updates can patch security holes, enhance functionality, and protect against new threats, ensuring the app remains secure and reliable.
What tools can help in securing a mobile app?
Tools that can help secure a mobile app include Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools for identifying vulnerabilities, as well as Runtime Application Self-Protection (RASP) for real-time threat detection and response. SSL certificates and encryption libraries are also essential for securing data in transit and at rest.

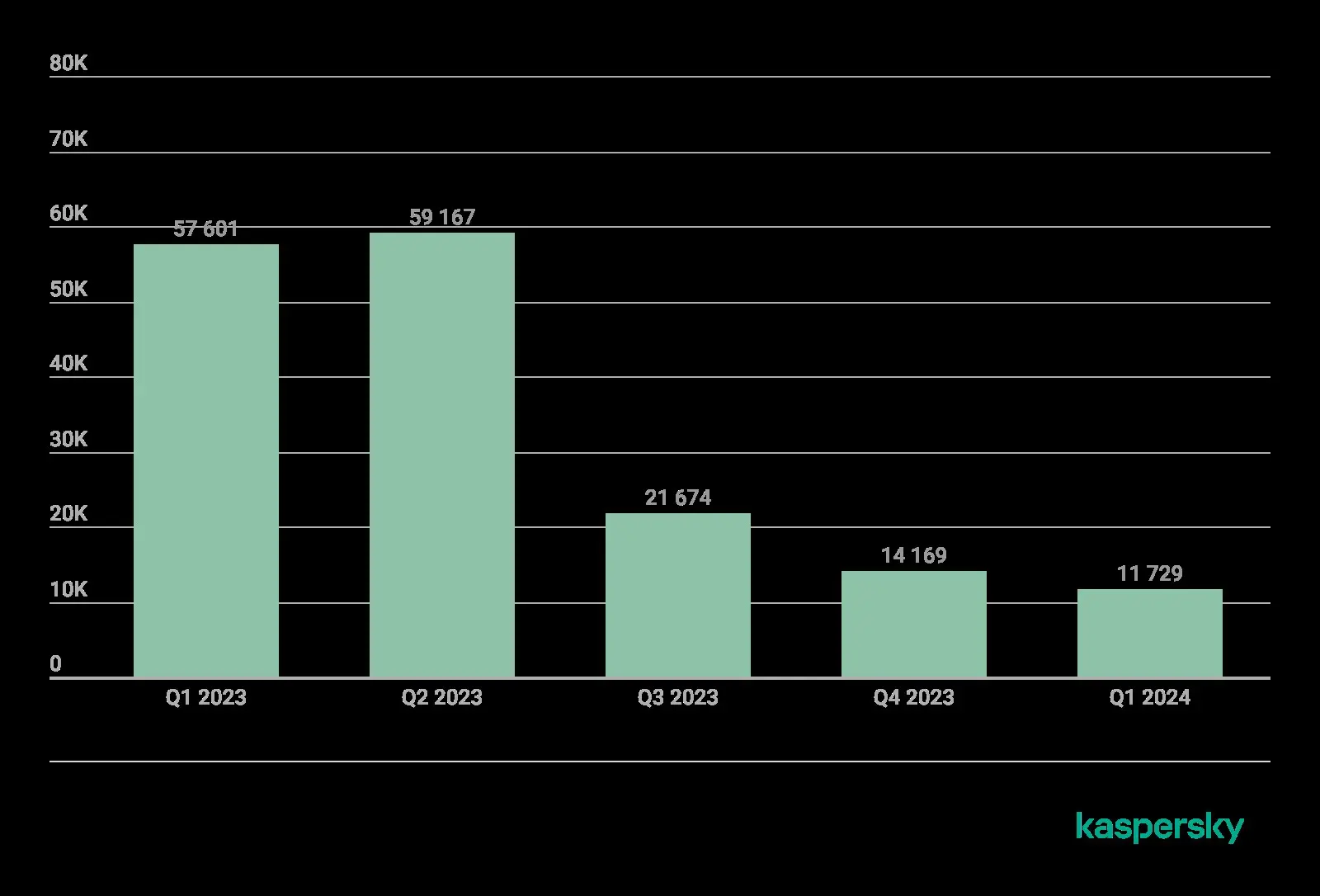 Source
Source

 Phishing Attacks
Phishing Attacks