Obfuscation… to make something obscure or unintelligible. In the programming world, obfuscation is about transforming your code such that it is rendered useless for any human to understand while making no changes to its execution or output of the code.
With the help of advanced tools and platforms, programmers may deliberately obfuscate code to conceal its purpose or logic to prevent the tampering of their application. This can be achieved by manual alteration of the code or by using an automated tool.
iOS app obfuscation has become an industry trend for mobile application developers and publishers, as data protection and security are primary concerns for all mobile consumers.
iOS App Obfuscation
Mobile applications (both Android and iOS) are a constant target for hacking and reverse engineering in today’s mobile-first world. But there’s a major misconception that iOS apps are not as vulnerable to hacking as other apps.
Objective-C and Swift are the world’s most common languages for developing iOS apps. These languages are typically compiled to machine code, making it hard to translate the app code back to the original source. This has led to the misconception that iOS apps are indeed ‘difficult’ to reverse engineer.
Top misconceptions about iOS apps:
- Hard to reverse engineer machine code.
- Apple’s code encryption will suffice to safeguard apps reverse engineering.
- Restricted access to the machine code of the apps (after download) could easily prevent analysis of the application.
As a bad habit, developers working on apps for iOS will focus mainly on the app’s UX and UI before getting it published, thereby overlooking a critical factor – security.
Misconception: Not so difficult to reverse engineer machine code!
As technology evolves by leaps and bounds, we have witnessed more mature technology in place for reverse engineering ‘machine code.’ Also, when Objective-C and Swift are compiled to machine code, lots of metadata are present in the binary, which is required in these languages. This makes the reverse engineering process much easier.
Perpetrators can easily understand your code and reverse engineer it. Therefore, as a developer, you must be aware of the dangers and take the necessary precautions to avoid them.
Code obfuscation has become a standard practice for iOS developers to prevent hackers from decompiling and reverse engineering code. Obfuscation can scramble the app’s code (in various ways) to make it difficult to comprehend and analyze.
Need for iOS App Obfuscation
iOS applications are highly susceptible to reverse engineering attacks because of their design. The app’s classes and protocols are stored right inside the object file, which allows an attacker to map out the application’s design.
In iOS, most attacks will come due to the weaknesses of the Objective-C runtime:
- The application design is stored in the binary, enabling an attacker to reconstruct the app architecture.
- The reflection mechanism in Objective-C easily enables attackers to modify the application state.
- The messaging framework of Objective-C is very simple. Due to this, messages can be easily tracked and manipulated.
Objective-C implements a simplistic messaging framework that can be manipulated easily to tamper with the main code with an application’s runtime. Even basic attacks would suffice to manipulate the objective-C runtime to bypass authentication and policy checks.
You should consider implementing anti-debug techniques for apps that contain highly sensitive data, like in financial or banking apps. These techniques can increase the complexity of reverse engineering your code.
One such technique is used for C/C++ that limits the runtime manipulation by an attacker. As a best practice, you should consider writing critical portions of your iOS app code in low-level C to avoid any exposure by the Objective-C runtime or Objective-C reverse engineering tools such as class-dump-z, Cycript, Frida, etc.
iOS App Obfuscation Advantages
Let’s quickly highlight the direct advantages of obfuscation:
- Protect the machine code from being copied and altered without permission.
- Make your app’s logic and algorithms less exposed.
- Make it extremely difficult for hackers to identify vulnerabilities in your code.
Apart from the obvious benefits of enhanced security and reduced threats, automated code obfuscation offers a unique advantage. It helps protect the software’s IP (intellectual property) by making reverse-engineering a program difficult and economically unfeasible.
Other advantages of automated obfuscation include:
- Protecting licensing mechanisms
- Avoiding unauthorized access
- Efficient shrinking of the size of the source code
iOS App Obfuscation Disadvantages
While the obfuscation process can make reading, writing, and reverse-engineering a code complicated and time-consuming, it will not necessarily make it impossible.
Another problem could be that most antivirus tools, such as the AVG AntiVirus, will alert their users when they browse a page with code that is manually obfuscated.
This is because obfuscation can also be used to hide malicious code, which can be detrimental to a user’s system. This makes it a red flag for antivirus tools.
Many developers may use code obfuscation just to reduce file size. So naturally, when a user gets an alert from their antivirus software about an obfuscated code (which could be harmless for the user), it could deter them from using the software altogether.
Methods Used for iOS Obfuscation
Let’s explore the popularly used methods and techniques in obfuscating iOS apps.
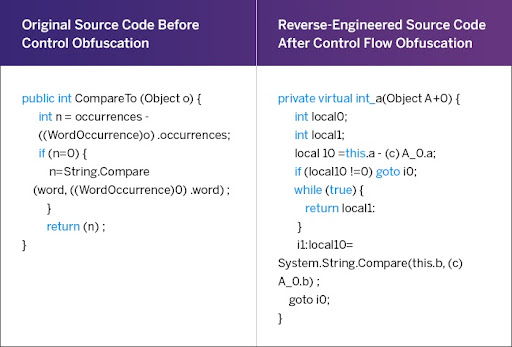
1. Control flow obfuscation
To determine the execution intent of an app, one needs to understand its control flow. Control flow obfuscation deals with altering an application’s “logical execution flow”. This is achieved by controlling the flow of the app dynamic in a different and controlled manner.
This is a great way to obfuscate logic and confuse hackers because it takes a lot longer and a lot more analysis to understand how the code executes and why it takes a certain direction.
One of the most direct ways of obfuscation is to use arbitrary strings and unexpected statements within the code and add random case-switch statements (dead code). These statements confuse the hacker as they serve no purpose in the execution or flow of the code while posing to be a critical part of the code. You can use this type of alteration in the order of program execution statements, especially in the case of conditional program orientation.
Source: PreEmptive
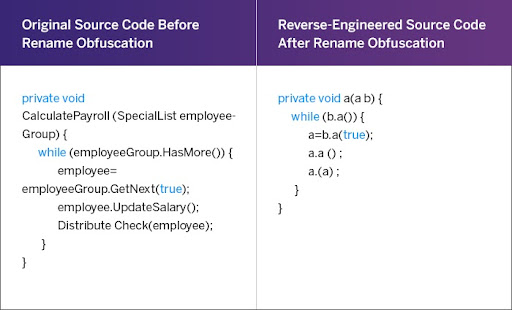
2. Rename obfuscation
Renaming is a process in which entities such as classes, methods, fields, annotations, and packages are completely renamed to make Java bytecode more compact and more difficult to reverse engineer.
The names you establish in your source code carry a lot of sensitive information about your code’s individual components.
These names are usually retained in the final bytecode as they are needed to invoke a ‘Main‘ method of a given class in a different project. However, these names serve no purpose after compilation apart from making your application easier to understand for an attacker. With renaming, you can easily replace these names with meaningless names (e.g., a, b).
Source: PreEmptive
3. Layout and data obfuscation
Data obfuscation is a technique that targets the data structures used in the code so that the perpetrator won’t be able to understand or lay hands on the actual intent of the program.
This typically involves modifying how data is stored into memory and how it is interpreted to show the final output. Let’s explore some different variants for this method:
1. Aggregation obfuscation
This method alters the way data is stored. For example, the arrays could be broken down into many sub-arrays. These individual sub-arrays could then be referenced at different locations of the program.
2. Storage obfuscation
This method obfuscates the very manner in which data is stored in memory. For example, publishers can juggle between local and global storage of variables. That way, the real nature of variable behavior is obfuscated.
3. Ordering obfuscation
This technique reorders how the data is ordered but does not alter the behavior of the code snippet. You can accomplish it by programming a separate module that is called for all instances of the variable reference.
4. String encryption
String obfuscation works by scrambling a string in various random ways. This hides and replaces the strings with a nonsensical representation of the string. The CPU will automatically be able to descramble the string during execution, while a hacker would be able to make little meaning out of the string from a static analysis.
In Closing: Is Obfuscation Alone Enough?
While obfuscation can be a highly effective and fool-proof security measure to protect applications against reverse engineering and intellectual property theft, it is not enough to fully protect your apps from real-world attack scenarios.
Therefore, 360-degree code protection is required. This would include comprehensive runtime protection along with obfuscation to fully protect your iOS apps.