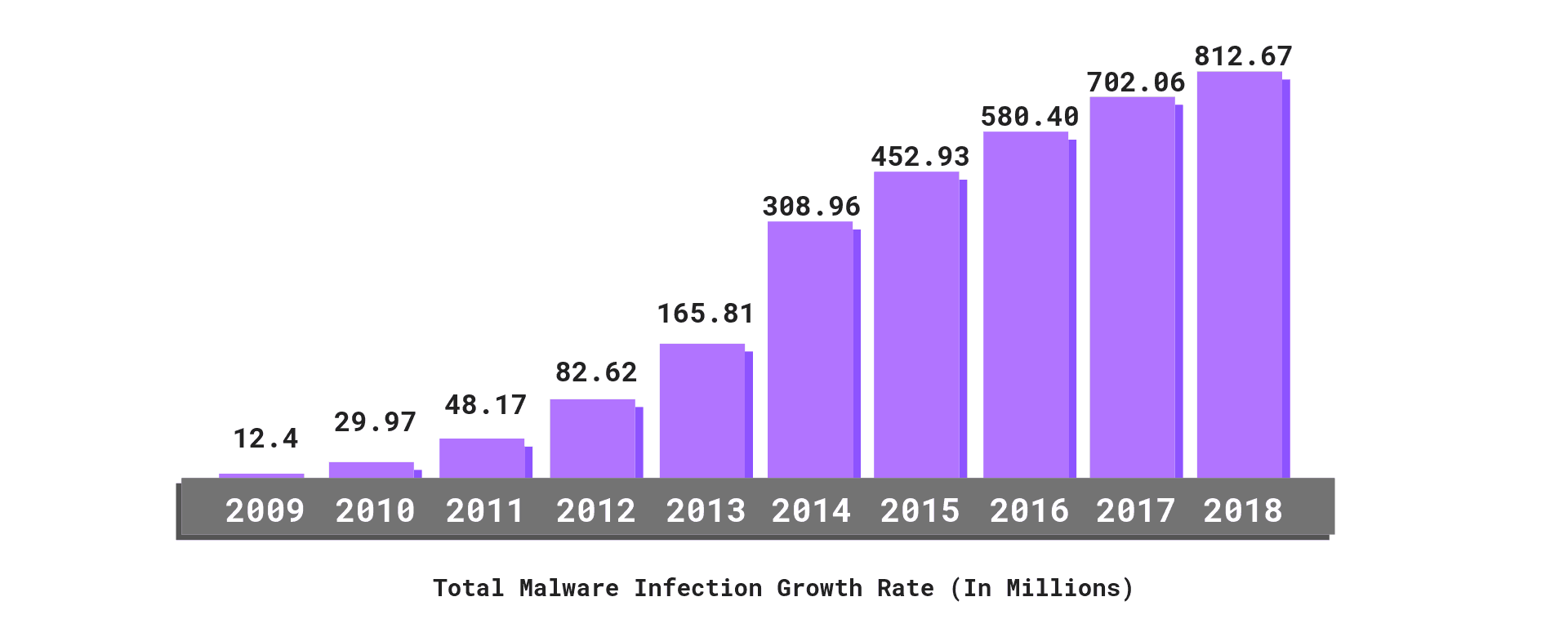
Enterprise app security has advanced a long way, yet some forms of hacking like SQL injections, which were first noticed and tackled in 1998, are still a threat today (BQE Software’s BillQuick Web Suite was a victim of SQL injection). In fact, a 2020 Edgescan Vulnerability Stats Report reported that 42% of vulnerabilities in Internet-facing applications were from SQL injection errors!
Source: PurpleSec
It just goes to show, IT security is a continuous and ongoing process, and as the line between real and digital continues to blur, ensuring 100% enterprise application security becomes even more critical and difficult.
What is Enterprise Application Security?
Enterprise Application Security is the safeguarding of all enterprise applications from external attacks and hacks. The purpose is to prevent external sources from accessing, stealing, and exploiting any and all data (public or privileged, internal, or customer-related) owned by the organization, and the method of achieving absolute enterprise application security is by not just maintaining application security but also the security of all other IT elements – hardware, virtual machines, operating systems, third-party apps, etc., that the organization utilizes.
Why enterprise application security is critical today is not a tough question to answer. Almost every business relies on multiple applications hosted on-premise and the cloud for day-to-day operations. As data moves across these apps and platforms, each element becomes a point of vulnerability. Proof of this is a statistic in Comparitech’s 2021 cyber security vulnerability report – 18,362 vulnerabilities were published in 2020 as opposed to 17,382 in 2019 and 17,252 in 2018.
Another important factor is that the data itself has become more personal. Consumers conduct almost every daily activity – conversations, transportation, connections, financial transactions, purchases, etc., digitally, and so the data that is susceptible to attacks today is extremely personal and confidential.
And yet another factor is brand reputation. The two brands listed in our introduction (BillQuick Web Suite and MCH Group) will forever be remembered for having been hacked, and that is a tough stain to shake off.
Enterprise application security is extremely important because the number of vulnerabilities has increased, the data has become more personal and valuable. In a fairly open and connected world, organizations cannot afford to tarnish their reputation even once.
This article covers the different points of vulnerabilities that organizations must secure for complete enterprise application security and mentions various ways of doing so.
Enterprise Application Security Threats
1. Device-specific threats
Most organizations allow employees to work from their personal devices (BYOD) or at least connect their personal devices to the office network for personal use. This automatically makes the device a point of threat.
Insecure applications and OS vulnerabilities – If the device has insecure applications installed, if the user has unknowingly given the app unrestricted access, or if the user’s phone has an outdated OS, it could become a threat to the organization’s network. An unsecure app can be used to collect credentials used by the user to connect to the network and inject malware.
It is sometimes the most popular apps that are vulnerable. In fact, WhatsApp and Facebook Messenger are some of the top blacklisted apps for iOS in organizations, according to a report by Techbeacon.
Educating employees about this helps, but organizations will have to be prudent and take matters into their own hands and use access control to prevent any apps other than those needed for business from running on the business network.
2. Network-specific threats
Unsecured network connections (like WiFi) can expose the network and all connected devices to cyber attacks. Today, this is especially a risk with employees working from home and connecting to the organization network remotely through their public network.
There are measures like using VPNs that can mask IPs and mitigate some of the damage that could occur, but using prevention methods like malware protection and network monitoring systems are preferred.
3. User-specific threats
Source: Varonis
Some cyber attacks happen because of bad actors within the organization – malicious employees and negligent ones.
Close to 81% of the global workforce have experienced full or partial closing of their workplace, a BBC article reported. This has resulted in many people losing their jobs, and coupled with the increasing number of vulnerabilities in organization IT, malicious players have used cyber attacks as a means of revenge. Christopher Dobbins, who was laid off from his place of work, a medical device packaging company, hacked the company’s network and deleted shipping information. This breach caused serious delays in the delivery of personal protective equipment (PPEs) in the middle of a global pandemic!
On the other hand, negligent employees could unknowingly put the organization at risk by revealing confidential credentials, clicking on suspicious links, falling for phishing attacks, etc. Some employees of Twitter who were working remotely fell prey to a “vishing” (voice phishing) attack in 2020. They received calls from hackers claiming to be Twitter IT administrators. These impersonators persuaded the employees to reveal confidential credentials and used them to log in to the admin console and manipulated the accounts of close to 130 high-profile people, like Barack Obama, Joe Biden, and Kanye West, and used the accounts to run a Bitcoin scam. The incident knocked Twitter’s stocks down by 4%.
4. App-specific threats
For organizations that take ownership of applications, being aware of app-specific threats will help mitigate attacks.
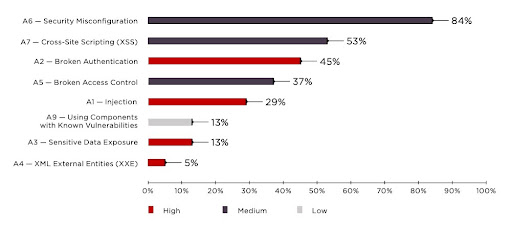
Source: Positive Technologies
Injection flaws – Malicious queries can be injected into database systems like MySQL, NoSQL, OS, and LDAP to corrupt the database or extract information.
Broken authentication – A flawed authentication system (often validating via a database) is vulnerable to brute force attacks that can be used to break into the system.
Exposed sensitive data – Passing sensitive data like credit card information or authentication credentials unencrypted can lead to phishing of this data.
XML External Entities (XXE) – An XXE is a vulnerability in the way an app parses XML input. It happens when a weakly-configured XML parser processes an unauthorized external entity XML injected by an attacker.
Broken access control (BAC) – BAC happens when the system enforcing access control is not functioning properly, either due to bugs or a hack. This allows users with limited access to access restricted data.
Security misconfiguration – Unsecured default configurations, incomplete configurations, and open cloud storage are forms of security misconfiguration that lead to hacks. Research by DivvyCloud, a US-based supplier of security and compliance automation for cloud and container environments, suggests that cloud misconfigurations in 2018 and 2019 are what led to the exposure of 33.4 billion records in enterprises around the world, with the cost estimated to be as much as $5tn.
Unsecured deserialization – When applications deserialize – convert bytes of data back into objects, malicious or untrusted data unabated – the system is vulnerable to malicious serialized Java objects injected by attackers.
Component vulnerabilities – Using devices or applications with known vulnerabilities is a major no-no. These vulnerabilities can easily expose your IT infrastructure and lead to attacks, as happened with the Citrix Netscaler vulnerability CVE-2020-19781, which led to multiple ransomware attacks.
Steps for Strong Enterprise Application Security
1. Educate your employees
It might seem strange that the first step in preventing cyberattacks is human-based, but the number of attacks that happen because of negligent employees is huge and can be very easily mitigated.
In fact, a 2020 report by Cybintsolutions stated that 95% of cybersecurity breaches are due to human error!
This is understandable because breaching applications and hardware isn’t as easy as exploiting human naivety.
All employees within the organization and not just members of the IT team must be educated on the dos and don’ts of technology.
2. Implement a strict access control policy
Organizational tools like Microsoft Active Directory give IT admins central level control into providing organization-wide access. This includes restrictions to devices (company and personal), networks, and users.
By moving the responsibility for access from the user to the organization (via the IT team), you can greatly reduce threats and vulnerabilities due to negligence.
Having centralized control of access also allows you to quickly block infected apps and devices to minimize the spread of a threat during an attack.
3. Force strong user authentication
The 2019 Verizon Data Breach Investigations Report (DBIR) stated that 80% of all data breaches were caused by ‘weak’ passwords and credentials being compromised.
Reiterating our earlier point, the organization must move the responsibility of using highly secure and complex credentials from the employee to the company (enforced via the IT team).
Again, using access control and policy tools or by implementing them into applications, the IT team must enforce the use of complex credentials and also put in place a policy for regular password changes. You might be forced to give up the ease of use for security – single sign-on (SSO) is more convenient for employees but is vulnerable to attacks as opposed to OAuth 2.0 with two-factor authentication.
4. Encrypt all data
We have already highlighted how unencrypted data can be phished, extracted, or exploited. This can be user-based data like credentials or serialized/deserialized data flowing through applications.
Securing in-transit data can be done through methods like using SSL with 256-bit encryption. Using encryption algorithms and keys through data encryption solutions or in-house methods will help prevent data (even if stolen) from being deciphered.
Encouraging protecting stored data through application-level access control and encryption is a prudent way of preventing data exploits.
5. Update just in time
Updating firmware, software and applications is a tricky business – sometimes a patch is released to fix a potential threat and should be immediately implemented, and sometimes a patch is released which contains a vulnerability and should be immediately rolled back.
The timing of these updates is key, and the IT team in charge of updating firmware, software, and applications should do so with a proper process. Read the changelog for the update, identify if there is any need for immediate updating, release the update in the test environment first and look for any breakdown, and finally roll out the update in chunks across the organization.
6. Identify all points of vulnerability
Creating a document of all elements in the IT ecosystem – the hardware, the applications, and network elements (on-premise and cloud-based) will create a level of transparency and improve monitoring and tracking processes.
This method of covering all elements will help you leave no blind spots in security and protect the entire IT stack.
When you implement an operations manager, you can integrate all elements within the IT ecosystem for monitoring and tracking and then analyze each endpoint for possible vulnerabilities and attacks.
7. Monitor, track, and attack
Systems like Microsoft’s System Center Operations Manager (SCOM) or DynaTrace should be used to track and monitor hardware, networks, and applications. They are equipped to identify cyber threats, analyze erratic, irregular, and abnormal behavior, and notify you of potential threats and attacks.
These systems help organizations take proactive measures to mitigate attacks and data leaks.
Cybersafety solutions like malware protection and antivirus should be another important addition to all devices and applications within the organization – both for executive-level and their employees.
8. Make security a part of the business process
Security analysis, testing, and fixing should become a part of the business lifecycle. Running drills and training for employees and tests for applications, software and hardware on a regular basis to ensure they are safe should become a mandatory practice for the IT team.
Introducing a mindset of continuous checking and improving for security will help you stay on top of all elements within the enterprise and keep your team prepared to act against threats if and when they do occur.
Final Thoughts
Ensuring 100% security and 0% breaches is foolish. The technological landscape is one that is ever-evolving, and with change comes new risks. IoT (Internet of Things) is becoming a norm across organizations in the world, and with this extremely high level of connectivity, we expose ourselves to higher risks and vulnerabilities.
But that does not mean organizations should not implement modern solutions like AI and ML that give technology more control (and thus open up potential risks). On the contrary, technology can exponentially increase productivity and results while introducing a fractional amount of risk.
Organizations must understand that security has to be seen as a business goal, just like revenue and client-level SLAs, and should be treated as a KPI for the IT team. Security is also a joint responsibility between the business and its employees. Lastly, security is a matter of doing everything possible to ensure safety and then monitoring all systems so the business can take proactive and quick reactive measures.